𝐎𝐖𝐀𝐒𝐏 𝐓𝐨𝐩 𝟏𝟎 𝟐𝟎𝟐𝟓: 𝐖𝐡𝐚𝐭’𝐬 𝐂𝐡𝐚𝐧𝐠𝐢𝐧𝐠 𝐢𝐧 𝐀𝐩𝐩 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲?
In a world where 𝐰𝐞𝐛 𝐚𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 that power everything from banking to healthcare, security cannot be considered an afterthought anymore. 𝐎𝐖𝐀𝐒𝐏 comes here as a nonprofit organization that is committed to the 𝐠𝐥𝐨𝐛𝐚𝐥 𝐠𝐨𝐚𝐥 𝐨𝐟 𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐬𝐨𝐟𝐭𝐰𝐚𝐫𝐞 𝐨𝐩𝐞𝐧𝐧𝐞𝐬𝐬, 𝐩𝐫𝐚𝐜𝐭𝐢𝐜𝐚𝐥𝐢𝐭𝐲, 𝐚𝐧𝐝 𝐚𝐜𝐜𝐞𝐬𝐬𝐢𝐛𝐢𝐥𝐢𝐭𝐲 𝐟𝐨𝐫 𝐞𝐯𝐞𝐫𝐲𝐛𝐨𝐝𝐲.
With the increasing complexity of cyber threats and applications, OWASP provides the developers and organizations with reliable knowledge, community-based expertise, and industry-accepted guidance to create secure applications right from the start and thereby 𝐬𝐚𝐟𝐞𝐠𝐮𝐚𝐫𝐝 𝐭𝐡𝐞 𝐦𝐨𝐬𝐭 𝐢𝐦𝐩𝐨𝐫𝐭𝐚𝐧𝐭 𝐭𝐡𝐢𝐧𝐠𝐬: 𝐝𝐚𝐭𝐚, 𝐭𝐫𝐮𝐬𝐭, 𝐚𝐧𝐝 𝐝𝐢𝐠𝐢𝐭𝐚𝐥 𝐫𝐞𝐬𝐢𝐥𝐢𝐞𝐧𝐜𝐞.
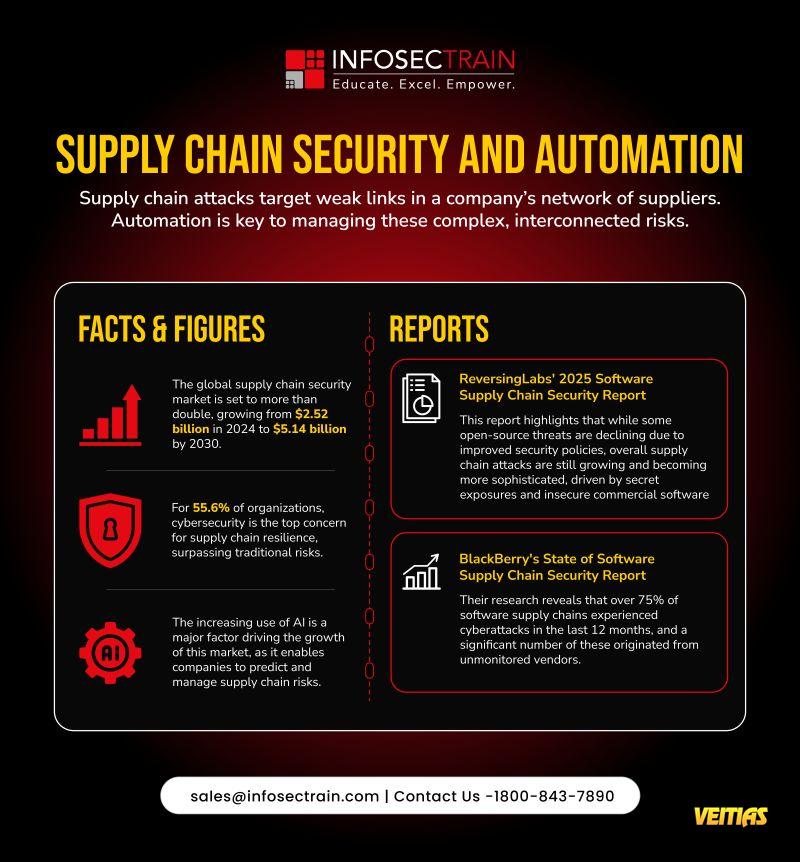
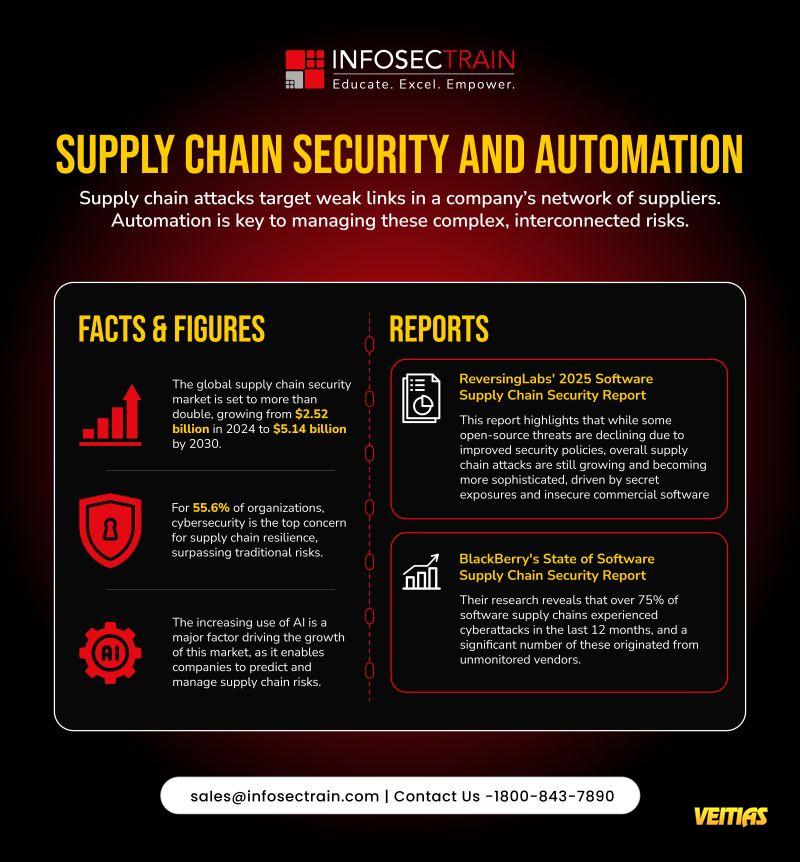
Application security has transformed and gradually evolved into a complete process of fixing codes. The 𝐎𝐖𝐀𝐒𝐏 𝐭𝐨𝐩 𝟏𝟎 𝐨𝐟 𝟐𝟎𝟐𝟓 shifts the focus towards architecture, supply chains, and cloud-first risks.
𝐑𝐞𝐚𝐝 𝐦𝐨𝐫𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/owasp-top-10-2025
𝐖𝐡𝐲 𝐢𝐭 𝐦𝐚𝐭𝐭𝐞𝐫𝐬:
Security has to be present from the very beginning and at every stage from design to deployment, especially in cloud-native environments
#OWASPTop10 #ApplicationSecurity #SecureByDesign #DevSecOps #CloudSecurity #SoftwareSupplyChain #CyberSecurity #Infosectrain
In a world where 𝐰𝐞𝐛 𝐚𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 that power everything from banking to healthcare, security cannot be considered an afterthought anymore. 𝐎𝐖𝐀𝐒𝐏 comes here as a nonprofit organization that is committed to the 𝐠𝐥𝐨𝐛𝐚𝐥 𝐠𝐨𝐚𝐥 𝐨𝐟 𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐬𝐨𝐟𝐭𝐰𝐚𝐫𝐞 𝐨𝐩𝐞𝐧𝐧𝐞𝐬𝐬, 𝐩𝐫𝐚𝐜𝐭𝐢𝐜𝐚𝐥𝐢𝐭𝐲, 𝐚𝐧𝐝 𝐚𝐜𝐜𝐞𝐬𝐬𝐢𝐛𝐢𝐥𝐢𝐭𝐲 𝐟𝐨𝐫 𝐞𝐯𝐞𝐫𝐲𝐛𝐨𝐝𝐲.
With the increasing complexity of cyber threats and applications, OWASP provides the developers and organizations with reliable knowledge, community-based expertise, and industry-accepted guidance to create secure applications right from the start and thereby 𝐬𝐚𝐟𝐞𝐠𝐮𝐚𝐫𝐝 𝐭𝐡𝐞 𝐦𝐨𝐬𝐭 𝐢𝐦𝐩𝐨𝐫𝐭𝐚𝐧𝐭 𝐭𝐡𝐢𝐧𝐠𝐬: 𝐝𝐚𝐭𝐚, 𝐭𝐫𝐮𝐬𝐭, 𝐚𝐧𝐝 𝐝𝐢𝐠𝐢𝐭𝐚𝐥 𝐫𝐞𝐬𝐢𝐥𝐢𝐞𝐧𝐜𝐞.
Application security has transformed and gradually evolved into a complete process of fixing codes. The 𝐎𝐖𝐀𝐒𝐏 𝐭𝐨𝐩 𝟏𝟎 𝐨𝐟 𝟐𝟎𝟐𝟓 shifts the focus towards architecture, supply chains, and cloud-first risks.
𝐑𝐞𝐚𝐝 𝐦𝐨𝐫𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/owasp-top-10-2025
𝐖𝐡𝐲 𝐢𝐭 𝐦𝐚𝐭𝐭𝐞𝐫𝐬:
Security has to be present from the very beginning and at every stage from design to deployment, especially in cloud-native environments
#OWASPTop10 #ApplicationSecurity #SecureByDesign #DevSecOps #CloudSecurity #SoftwareSupplyChain #CyberSecurity #Infosectrain
𝐎𝐖𝐀𝐒𝐏 𝐓𝐨𝐩 𝟏𝟎 𝟐𝟎𝟐𝟓: 𝐖𝐡𝐚𝐭’𝐬 𝐂𝐡𝐚𝐧𝐠𝐢𝐧𝐠 𝐢𝐧 𝐀𝐩𝐩 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲?
✅ In a world where 𝐰𝐞𝐛 𝐚𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 that power everything from banking to healthcare, security cannot be considered an afterthought anymore. 𝐎𝐖𝐀𝐒𝐏 comes here as a nonprofit organization that is committed to the 𝐠𝐥𝐨𝐛𝐚𝐥 𝐠𝐨𝐚𝐥 𝐨𝐟 𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐬𝐨𝐟𝐭𝐰𝐚𝐫𝐞 𝐨𝐩𝐞𝐧𝐧𝐞𝐬𝐬, 𝐩𝐫𝐚𝐜𝐭𝐢𝐜𝐚𝐥𝐢𝐭𝐲, 𝐚𝐧𝐝 𝐚𝐜𝐜𝐞𝐬𝐬𝐢𝐛𝐢𝐥𝐢𝐭𝐲 𝐟𝐨𝐫 𝐞𝐯𝐞𝐫𝐲𝐛𝐨𝐝𝐲.
✅ With the increasing complexity of cyber threats and applications, OWASP provides the developers and organizations with reliable knowledge, community-based expertise, and industry-accepted guidance to create secure applications right from the start and thereby 𝐬𝐚𝐟𝐞𝐠𝐮𝐚𝐫𝐝 𝐭𝐡𝐞 𝐦𝐨𝐬𝐭 𝐢𝐦𝐩𝐨𝐫𝐭𝐚𝐧𝐭 𝐭𝐡𝐢𝐧𝐠𝐬: 𝐝𝐚𝐭𝐚, 𝐭𝐫𝐮𝐬𝐭, 𝐚𝐧𝐝 𝐝𝐢𝐠𝐢𝐭𝐚𝐥 𝐫𝐞𝐬𝐢𝐥𝐢𝐞𝐧𝐜𝐞.
✅ Application security has transformed and gradually evolved into a complete process of fixing codes. The 𝐎𝐖𝐀𝐒𝐏 𝐭𝐨𝐩 𝟏𝟎 𝐨𝐟 𝟐𝟎𝟐𝟓 shifts the focus towards architecture, supply chains, and cloud-first risks.
👉 𝐑𝐞𝐚𝐝 𝐦𝐨𝐫𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/owasp-top-10-2025
✅ 𝐖𝐡𝐲 𝐢𝐭 𝐦𝐚𝐭𝐭𝐞𝐫𝐬:
Security has to be present from the very beginning and at every stage from design to deployment, especially in cloud-native environments
#OWASPTop10 #ApplicationSecurity #SecureByDesign #DevSecOps #CloudSecurity #SoftwareSupplyChain #CyberSecurity #Infosectrain
0 Commenti
0 condivisioni
3806 Views
0 Anteprima