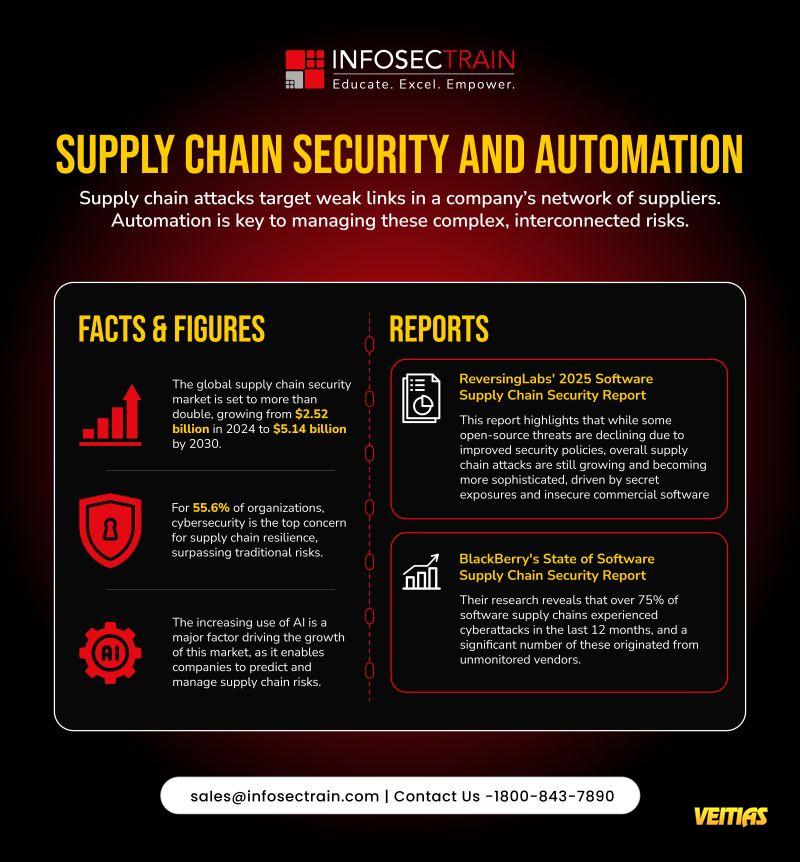
Supply Chain Security & Automation in 2025
As global supply chains grow more interconnected, cyber threats are targeting the weakest links, often through unmonitored or unsecured vendors.
Visit Our Site - https://www.infosectrain.com/
Build resilience. Automate defenses. Stay vigilant.
#SupplyChainSecurity #CyberResilience #Automation #AlinSecurity #ThreatIntelligence #CyberAwareness #DigitalTrust #VendorRiskManagement #infosectrain #learntorise
As global supply chains grow more interconnected, cyber threats are targeting the weakest links, often through unmonitored or unsecured vendors.
Visit Our Site - https://www.infosectrain.com/
Build resilience. Automate defenses. Stay vigilant.
#SupplyChainSecurity #CyberResilience #Automation #AlinSecurity #ThreatIntelligence #CyberAwareness #DigitalTrust #VendorRiskManagement #infosectrain #learntorise
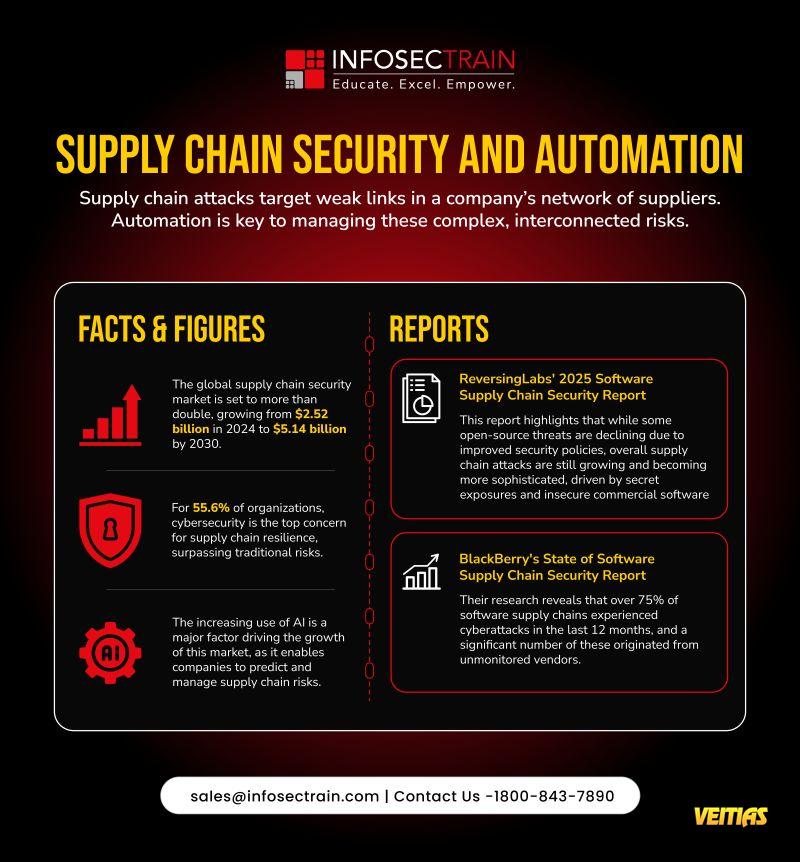
Supply Chain Security & Automation in 2025
As global supply chains grow more interconnected, cyber threats are targeting the weakest links, often through unmonitored or unsecured vendors.
Visit Our Site - https://www.infosectrain.com/
Build resilience. Automate defenses. Stay vigilant.
#SupplyChainSecurity #CyberResilience #Automation #AlinSecurity #ThreatIntelligence #CyberAwareness #DigitalTrust #VendorRiskManagement #infosectrain #learntorise
0 Commentarios
0 Acciones
819 Views
0 Vista previa