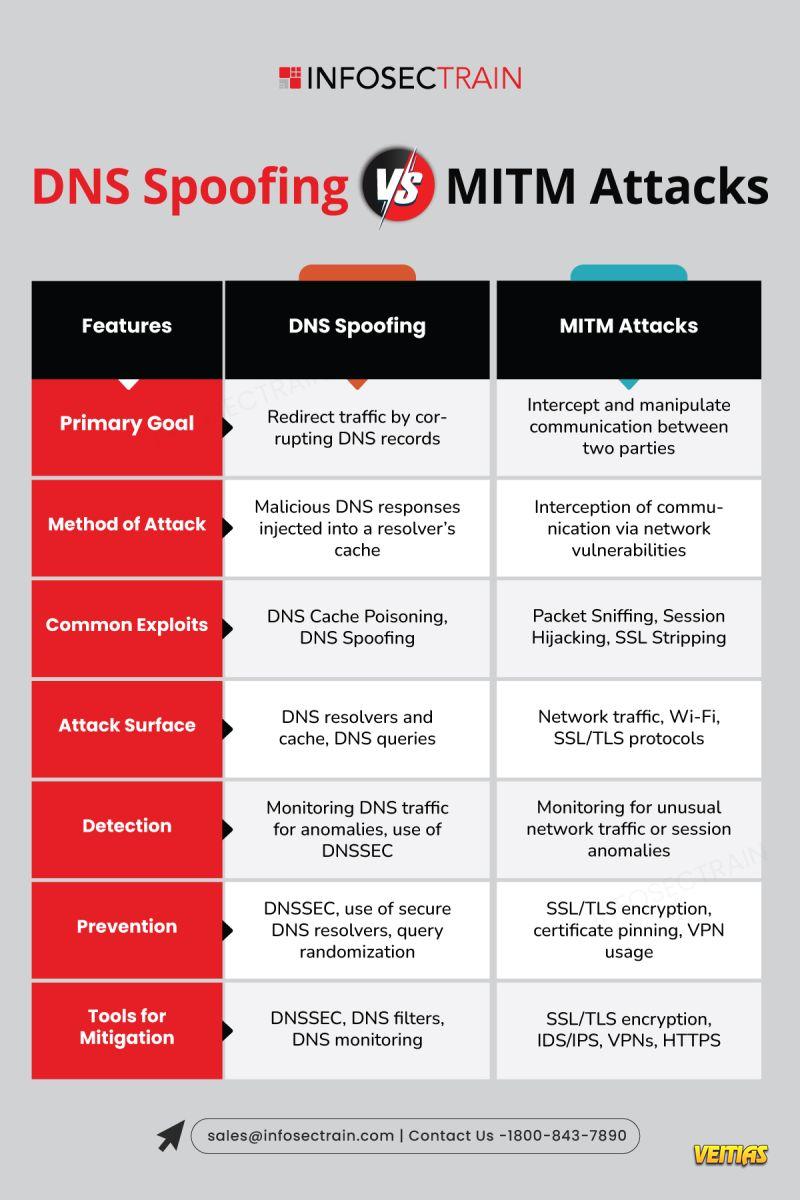
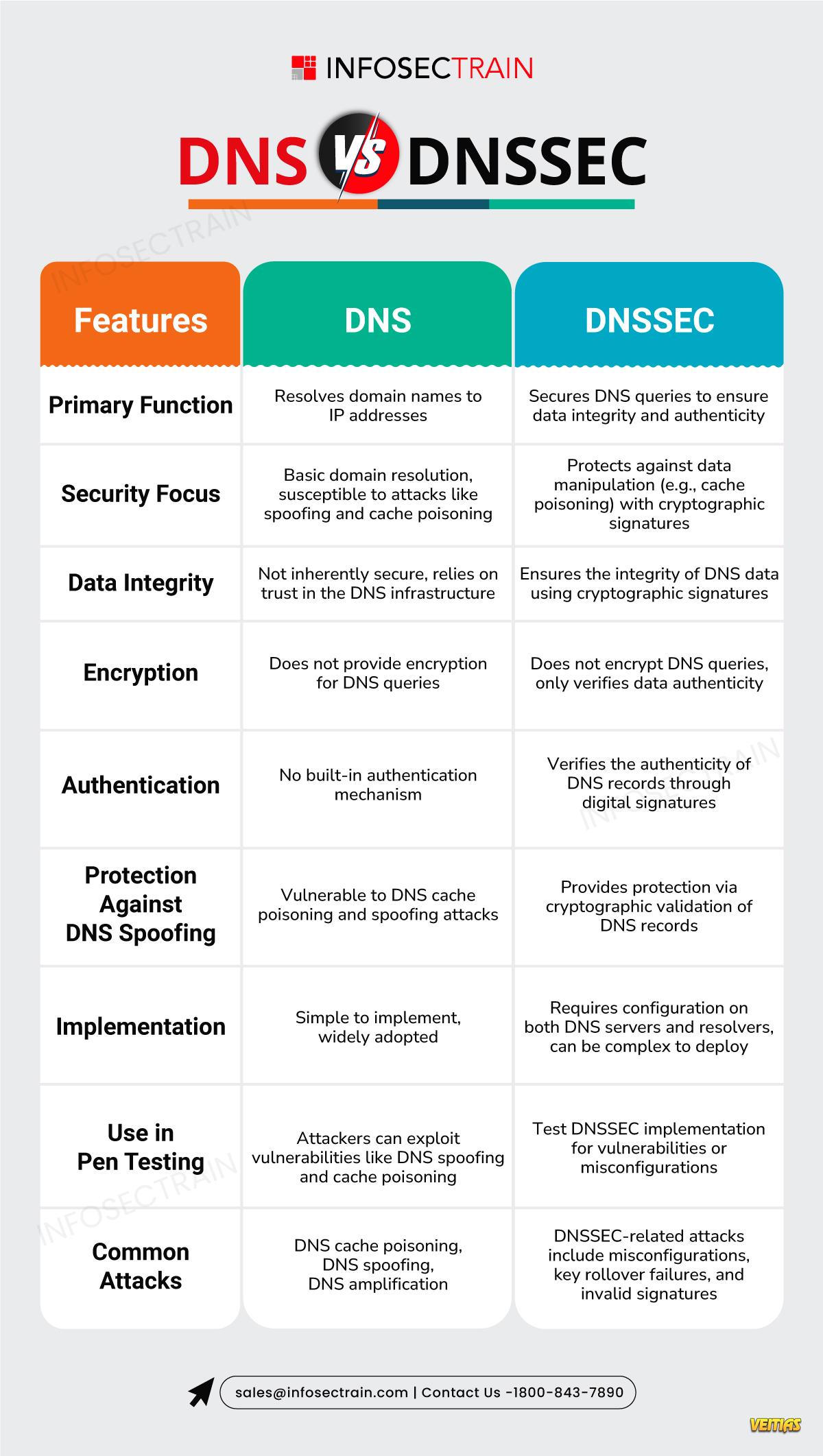
Understanding Cryptographic Controls in Information Security
With the increasing prevalence of data breaches and cyberattacks, understanding cryptographic controls is essential for organizations aiming to protect their information assets effectively. Gain a clear understanding of what cryptographic controls are and why they are crucial for maintaining data confidentiality, integrity, authenticity, and non-repudiation.
Read Here: https://www.infosectrain.com/blog/understanding-cryptographic-controls-in-information-security/
#Cryptography #InformationSecurity #DataProtection #InfosecTrain #ISO27001 #Cybersecurity #infosectrain
With the increasing prevalence of data breaches and cyberattacks, understanding cryptographic controls is essential for organizations aiming to protect their information assets effectively. Gain a clear understanding of what cryptographic controls are and why they are crucial for maintaining data confidentiality, integrity, authenticity, and non-repudiation.
Read Here: https://www.infosectrain.com/blog/understanding-cryptographic-controls-in-information-security/
#Cryptography #InformationSecurity #DataProtection #InfosecTrain #ISO27001 #Cybersecurity #infosectrain
Understanding Cryptographic Controls in Information Security
With the increasing prevalence of data breaches and cyberattacks, understanding cryptographic controls is essential for organizations aiming to protect their information assets effectively. Gain a clear understanding of what cryptographic controls are and why they are crucial for maintaining data confidentiality, integrity, authenticity, and non-repudiation.
Read Here: https://www.infosectrain.com/blog/understanding-cryptographic-controls-in-information-security/
#Cryptography #InformationSecurity #DataProtection #InfosecTrain #ISO27001 #Cybersecurity #infosectrain
0 Commentaires
0 Parts
3852 Vue
0 Aperçu