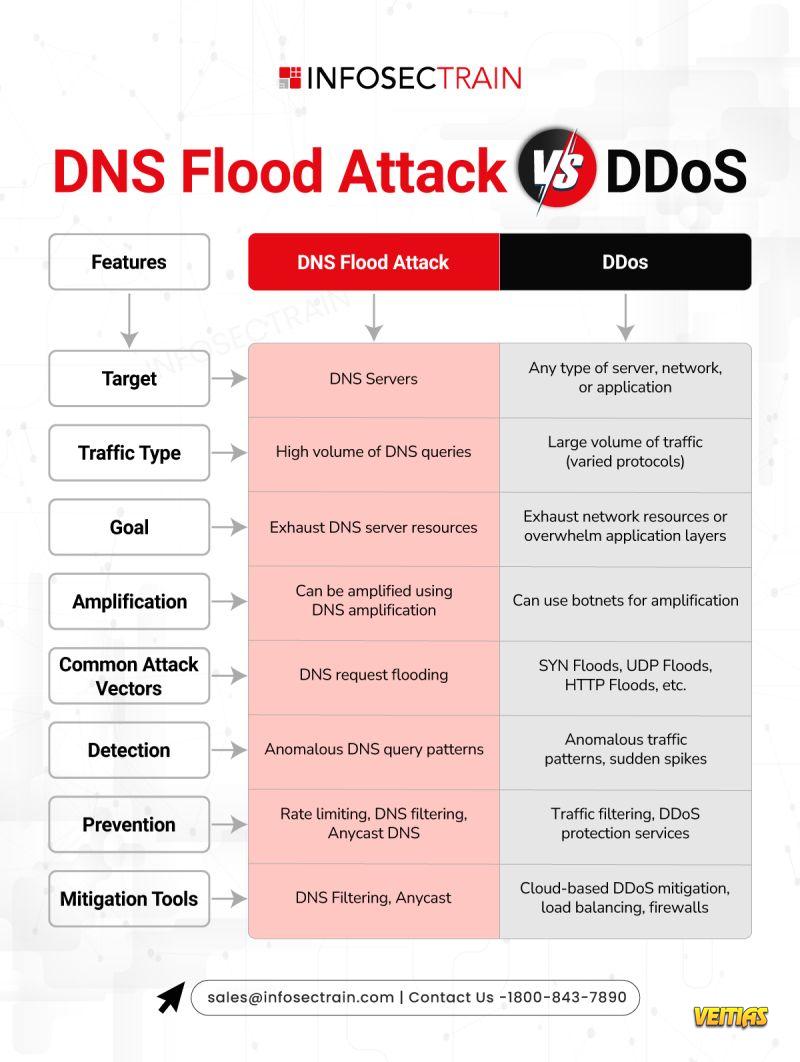
ISC2 CC Domain 3: Access Control Concepts
Who gets access to what? That's the foundation of Access Control—a critical security mechanism that ensures only authorized users can access specific resources like files, databases, networks, or physical spaces. It relies on Identification & Authentication (verifying identity), Authorization & Accountability (defining access rules and tracking usage), and principles like Least Privilege (granting minimal access) and Segregation of Duties (splitting responsibilities to prevent fraud).
Read more: https://www.infosectrain.com/blog/isc2-cc-domain-3-access-control-concepts/
#CyberSecurity #AccessControl #IAM #ZeroTrust #DataProtection #Infosec #CyberAwareness #TechSecurity #LeastPrivilege #SecurityBestPractices #infosectrain
Who gets access to what? That's the foundation of Access Control—a critical security mechanism that ensures only authorized users can access specific resources like files, databases, networks, or physical spaces. It relies on Identification & Authentication (verifying identity), Authorization & Accountability (defining access rules and tracking usage), and principles like Least Privilege (granting minimal access) and Segregation of Duties (splitting responsibilities to prevent fraud).
Read more: https://www.infosectrain.com/blog/isc2-cc-domain-3-access-control-concepts/
#CyberSecurity #AccessControl #IAM #ZeroTrust #DataProtection #Infosec #CyberAwareness #TechSecurity #LeastPrivilege #SecurityBestPractices #infosectrain
ISC2 CC Domain 3: Access Control Concepts
Who gets access to what? That's the foundation of Access Control—a critical security mechanism that ensures only authorized users can access specific resources like files, databases, networks, or physical spaces. It relies on Identification & Authentication (verifying identity), Authorization & Accountability (defining access rules and tracking usage), and principles like Least Privilege (granting minimal access) and Segregation of Duties (splitting responsibilities to prevent fraud).
Read more: https://www.infosectrain.com/blog/isc2-cc-domain-3-access-control-concepts/
#CyberSecurity #AccessControl #IAM #ZeroTrust #DataProtection #Infosec #CyberAwareness #TechSecurity #LeastPrivilege #SecurityBestPractices #infosectrain
0 Commenti
0 condivisioni
9876 Views
0 Anteprima