- 348 Posts
- 296 Photos
- 0 Videos
- Male
- 14/07/2002
- Followed by 1 people
Recent Updates
- SOC Analyst Hands-on Online Training
If you want to work in a SOC, you need more than theory - you need real attack simulations, real tools, and real investigation workflows.
InfosecTrain’s 48-Hour LIVE 𝗦𝗢𝗖 𝗔𝗻𝗮𝗹𝘆𝘀𝘁 𝗣𝗿𝗼𝗴𝗿𝗮𝗺 is designed to give you practical, job-ready experience aligned with how modern SOC teams operate.
𝟭𝟰 𝗠𝗮𝗿 – 𝟬𝟯 𝗠𝗮𝘆 𝟮𝟬𝟮𝟲
𝟭𝟵:𝟬𝟬 – 𝟮𝟯:𝟬𝟬 (𝗜𝗦𝗧) | 𝗪𝗲𝗲𝗸𝗲𝗻𝗱 𝗕𝗮𝘁𝗰𝗵🔴🛡️ SOC Analyst Hands-on Online Training If you want to work in a SOC, you need more than theory - you need real attack simulations, real tools, and real investigation workflows. InfosecTrain’s 48-Hour LIVE 𝗦𝗢𝗖 𝗔𝗻𝗮𝗹𝘆𝘀𝘁 𝗣𝗿𝗼𝗴𝗿𝗮𝗺 is designed to give you practical, job-ready experience aligned with how modern SOC teams operate. 📅 𝟭𝟰 𝗠𝗮𝗿 – 𝟬𝟯 𝗠𝗮𝘆 𝟮𝟬𝟮𝟲 🕘 𝟭𝟵:𝟬𝟬 – 𝟮𝟯:𝟬𝟬 (𝗜𝗦𝗧) | 𝗪𝗲𝗲𝗸𝗲𝗻𝗱 𝗕𝗮𝘁𝗰𝗵0 Comments 0 Shares 696 Views 0 ReviewsPlease log in to like, share and comment! - 𝗔𝗔𝗜𝗔 – 𝗔𝗱𝘃𝗮𝗻𝗰𝗲𝗱 𝗶𝗻 𝗔𝗜 𝗔𝘂𝗱𝗶𝘁 𝗖𝗲𝗿𝘁𝗶𝗳𝗶𝗰𝗮𝘁𝗶𝗼𝗻 𝗧𝗿𝗮𝗶𝗻𝗶𝗻𝗴
Lead the Future of AI Governance & Assurance
AI systems are transforming enterprises - but who ensures they’re secure, ethical, and compliant?
InfosecTrain’s 𝗔𝗔𝗜𝗔 (𝗔𝗱𝘃𝗮𝗻𝗰𝗲𝗱 𝗶𝗻 𝗔𝗜 𝗔𝘂𝗱𝗶𝘁) 𝗣𝗿𝗼𝗴𝗿𝗮𝗺 equips professionals to lead AI-enabled audits and manage AI risks confidently across the full audit lifecycle.
This 30-hour LIVE program blends governance, risk, compliance, and AI auditing practices into one comprehensive learning journey.
Led by KK Singh (22+ Years of Experience) AAIA | AISM | CISSP | CCSP | CISM | CRISC | CISA | CCSK | CDPSE | CIPM | PCI | AZ-900 | GDPR
https://www.infosectrain.com/courses/advanced-in-ai-audit-aaia-certification-training🤖🔍 𝗔𝗔𝗜𝗔 – 𝗔𝗱𝘃𝗮𝗻𝗰𝗲𝗱 𝗶𝗻 𝗔𝗜 𝗔𝘂𝗱𝗶𝘁 𝗖𝗲𝗿𝘁𝗶𝗳𝗶𝗰𝗮𝘁𝗶𝗼𝗻 𝗧𝗿𝗮𝗶𝗻𝗶𝗻𝗴 Lead the Future of AI Governance & Assurance AI systems are transforming enterprises - but who ensures they’re secure, ethical, and compliant? InfosecTrain’s 𝗔𝗔𝗜𝗔 (𝗔𝗱𝘃𝗮𝗻𝗰𝗲𝗱 𝗶𝗻 𝗔𝗜 𝗔𝘂𝗱𝗶𝘁) 𝗣𝗿𝗼𝗴𝗿𝗮𝗺 equips professionals to lead AI-enabled audits and manage AI risks confidently across the full audit lifecycle. This 30-hour LIVE program blends governance, risk, compliance, and AI auditing practices into one comprehensive learning journey. 👨🏫 Led by KK Singh (22+ Years of Experience) AAIA | AISM | CISSP | CCSP | CISM | CRISC | CISA | CCSK | CDPSE | CIPM | PCI | AZ-900 | GDPR https://www.infosectrain.com/courses/advanced-in-ai-audit-aaia-certification-training0 Comments 0 Shares 1193 Views 0 Reviews - 𝗖𝗘𝗛 𝘃𝟭𝟯 𝗔𝗜 – 𝗖𝗲𝗿𝘁𝗶𝗳𝗶𝗰𝗮𝘁𝗶𝗼𝗻 𝗧𝗿𝗮𝗶𝗻𝗶𝗻𝗴 𝗖𝗼𝘂𝗿𝘀𝗲
𝑨𝑰-𝑷𝒐𝒘𝒆𝒓𝒆𝒅 Ethical Hacking for the Modern Threat Landscape
Cybersecurity is evolving - and so is ethical hacking.
InfosecTrain’s 𝗖𝗘𝗛 𝘃𝟭𝟯 𝗔𝗜 𝗖𝗲𝗿𝘁𝗶𝗳𝗶𝗰𝗮𝘁𝗶𝗼𝗻 𝗧𝗿𝗮𝗶𝗻𝗶𝗻𝗴 equips you with next-generation hacking techniques powered by AI to detect, exploit, and defend against modern cyber threats.
This 40-hour LIVE program blends traditional ethical hacking with AI-driven methodologies, practical tools, and real-world lab environments.
Led by Ashish Rawat (6+ Years of Experience) - Web App Security | Advanced Penetration Testing | Secure Coding | OSINT | CEH | PenTest+ | Network+ | Security+ | CC
💻🤖 𝗖𝗘𝗛 𝘃𝟭𝟯 𝗔𝗜 – 𝗖𝗲𝗿𝘁𝗶𝗳𝗶𝗰𝗮𝘁𝗶𝗼𝗻 𝗧𝗿𝗮𝗶𝗻𝗶𝗻𝗴 𝗖𝗼𝘂𝗿𝘀𝗲 𝑨𝑰-𝑷𝒐𝒘𝒆𝒓𝒆𝒅 Ethical Hacking for the Modern Threat Landscape Cybersecurity is evolving - and so is ethical hacking. InfosecTrain’s 𝗖𝗘𝗛 𝘃𝟭𝟯 𝗔𝗜 𝗖𝗲𝗿𝘁𝗶𝗳𝗶𝗰𝗮𝘁𝗶𝗼𝗻 𝗧𝗿𝗮𝗶𝗻𝗶𝗻𝗴 equips you with next-generation hacking techniques powered by AI to detect, exploit, and defend against modern cyber threats. This 40-hour LIVE program blends traditional ethical hacking with AI-driven methodologies, practical tools, and real-world lab environments. Led by Ashish Rawat (6+ Years of Experience) - Web App Security | Advanced Penetration Testing | Secure Coding | OSINT | CEH | PenTest+ | Network+ | Security+ | CC0 Comments 0 Shares 1413 Views 0 Reviews - AI governance is no longer optional. InfosecTrain’s 𝗜𝗦𝗢/𝗜𝗘𝗖 𝟰𝟮𝟬𝟬𝟭 𝗟𝗲𝗮𝗱 𝗜𝗺𝗽𝗹𝗲𝗺𝗲𝗻𝘁𝗲𝗿 𝗧𝗿𝗮𝗶𝗻𝗶𝗻𝗴 is a hands-on, expert-led program designed to help professionals implement, manage, and audit 𝗔𝗜 𝗠𝗮𝗻𝗮𝗴𝗲𝗺𝗲𝗻𝘁 𝗦𝘆𝘀𝘁𝗲𝗺𝘀 (𝗔𝗜𝗠𝗦) aligned with the world’s first AI governance standard.
This program goes beyond theory - focusing on end-to-end implementation, real AI use cases, and practical readiness for organizational adoption.
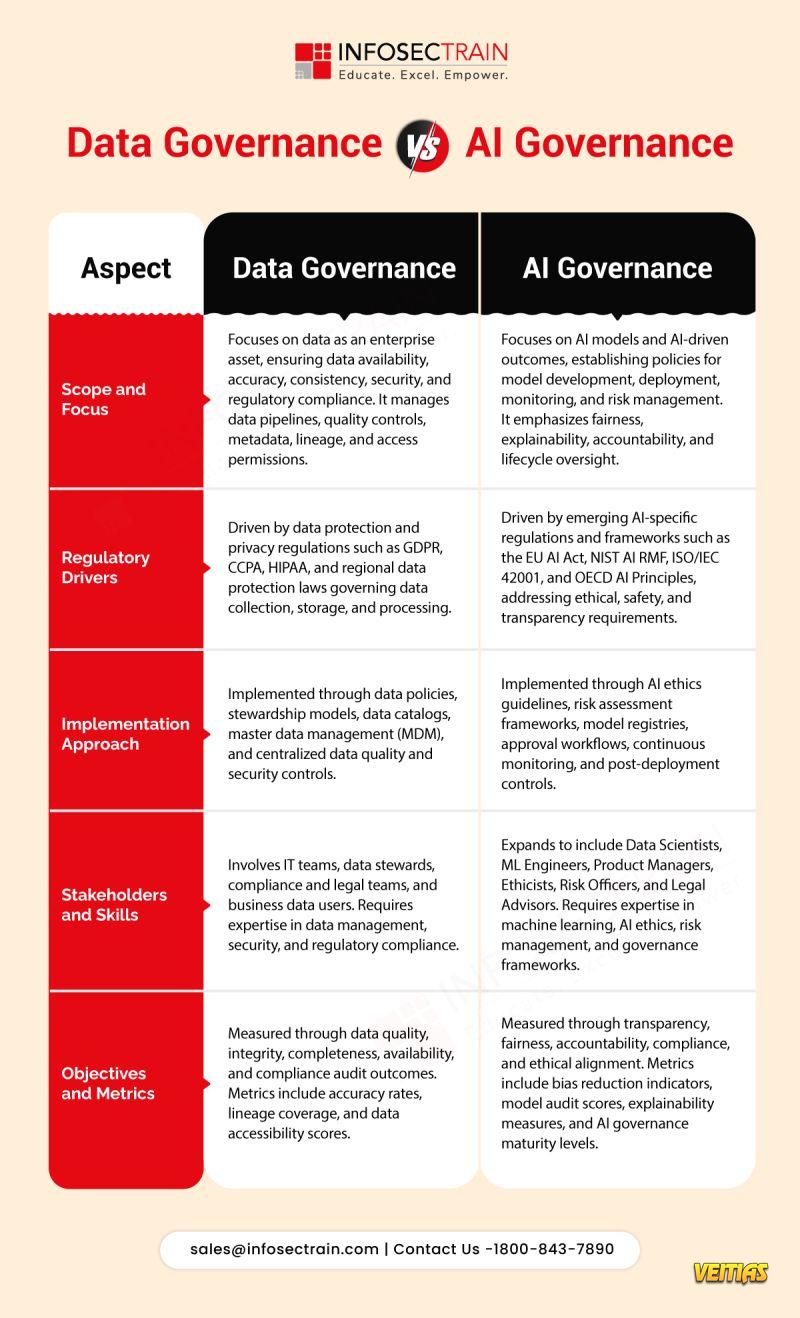
Instructor: Prabh Nair (18+ years of industry experience) The training blends governance, risk, compliance, and AI expertise into a job-ready learning experience.AI governance is no longer optional. InfosecTrain’s 𝗜𝗦𝗢/𝗜𝗘𝗖 𝟰𝟮𝟬𝟬𝟭 𝗟𝗲𝗮𝗱 𝗜𝗺𝗽𝗹𝗲𝗺𝗲𝗻𝘁𝗲𝗿 𝗧𝗿𝗮𝗶𝗻𝗶𝗻𝗴 is a hands-on, expert-led program designed to help professionals implement, manage, and audit 𝗔𝗜 𝗠𝗮𝗻𝗮𝗴𝗲𝗺𝗲𝗻𝘁 𝗦𝘆𝘀𝘁𝗲𝗺𝘀 (𝗔𝗜𝗠𝗦) aligned with the world’s first AI governance standard. This program goes beyond theory - focusing on end-to-end implementation, real AI use cases, and practical readiness for organizational adoption. 👨🏫 Instructor: Prabh Nair (18+ years of industry experience) The training blends governance, risk, compliance, and AI expertise into a job-ready learning experience.0 Comments 0 Shares 2605 Views 0 Reviews - 𝗔𝘀 𝗼𝗿𝗴𝗮𝗻𝗶𝘇𝗮𝘁𝗶𝗼𝗻𝘀 𝘀𝗰𝗮𝗹𝗲 𝗔𝗜 𝗮𝗱𝗼𝗽𝘁𝗶𝗼𝗻, 𝗴𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 𝗶𝘀 𝗻𝗼 𝗹𝗼𝗻𝗴𝗲𝗿 𝗹𝗶𝗺𝗶𝘁𝗲𝗱 𝘁𝗼 𝗱𝗮𝘁𝗮 𝗮𝗹𝗼𝗻𝗲. Understanding the difference between 𝗗𝗮𝘁𝗮 𝗚𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 𝗮𝗻𝗱 𝗔𝗜 𝗚𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 is becoming essential for 𝗿𝗶𝘀𝗸 𝗺𝗮𝗻𝗮𝗴𝗲𝗺𝗲𝗻𝘁, 𝗰𝗼𝗺𝗽𝗹𝗶𝗮𝗻𝗰𝗲, 𝗮𝗻𝗱 𝗿𝗲𝘀𝗽𝗼𝗻𝘀𝗶𝗯𝗹𝗲 𝗶𝗻𝗻𝗼𝘃𝗮𝘁𝗶𝗼𝗻.
𝗗𝗮𝘁𝗮 𝗚𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 𝗳𝗼𝗰𝘂𝘀𝗲𝘀 𝗼𝗻 𝗺𝗮𝗻𝗮𝗴𝗶𝗻𝗴 𝗱𝗮𝘁𝗮 as an enterprise asset through quality, security, lineage, and regulatory controls.
𝗔𝗜 𝗚𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 𝗴𝗼𝗲𝘀 𝗳𝘂𝗿𝘁𝗵𝗲𝗿 𝗯𝘆 𝗮𝗱𝗱𝗿𝗲𝘀𝘀𝗶𝗻𝗴 𝗺𝗼𝗱𝗲𝗹 𝗿𝗶𝘀𝗸,, ethics, explainability, lifecycle monitoring, and emerging global AI regulations.𝗔𝘀 𝗼𝗿𝗴𝗮𝗻𝗶𝘇𝗮𝘁𝗶𝗼𝗻𝘀 𝘀𝗰𝗮𝗹𝗲 𝗔𝗜 𝗮𝗱𝗼𝗽𝘁𝗶𝗼𝗻, 𝗴𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 𝗶𝘀 𝗻𝗼 𝗹𝗼𝗻𝗴𝗲𝗿 𝗹𝗶𝗺𝗶𝘁𝗲𝗱 𝘁𝗼 𝗱𝗮𝘁𝗮 𝗮𝗹𝗼𝗻𝗲. Understanding the difference between 𝗗𝗮𝘁𝗮 𝗚𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 𝗮𝗻𝗱 𝗔𝗜 𝗚𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 is becoming essential for 𝗿𝗶𝘀𝗸 𝗺𝗮𝗻𝗮𝗴𝗲𝗺𝗲𝗻𝘁, 𝗰𝗼𝗺𝗽𝗹𝗶𝗮𝗻𝗰𝗲, 𝗮𝗻𝗱 𝗿𝗲𝘀𝗽𝗼𝗻𝘀𝗶𝗯𝗹𝗲 𝗶𝗻𝗻𝗼𝘃𝗮𝘁𝗶𝗼𝗻. 𝗗𝗮𝘁𝗮 𝗚𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 𝗳𝗼𝗰𝘂𝘀𝗲𝘀 𝗼𝗻 𝗺𝗮𝗻𝗮𝗴𝗶𝗻𝗴 𝗱𝗮𝘁𝗮 as an enterprise asset through quality, security, lineage, and regulatory controls. 𝗔𝗜 𝗚𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 𝗴𝗼𝗲𝘀 𝗳𝘂𝗿𝘁𝗵𝗲𝗿 𝗯𝘆 𝗮𝗱𝗱𝗿𝗲𝘀𝘀𝗶𝗻𝗴 𝗺𝗼𝗱𝗲𝗹 𝗿𝗶𝘀𝗸,, ethics, explainability, lifecycle monitoring, and emerging global AI regulations.0 Comments 0 Shares 2358 Views 0 Reviews - Move beyond dashboards and alerts. InfosecTrain’s 𝙒𝙖𝙯𝙪𝙝 𝙋𝙧𝙖𝙘𝙩𝙞𝙘𝙖𝙡 𝙏𝙧𝙖𝙞𝙣𝙞𝙣𝙜 is a hands-on, real SOC-focused program designed to help you build, detect, and respond to threats using a live Wazuh environment.
This training is built for professionals who want practical SOC experience, not just tool familiarity.
Led by Urvesh Thakkar (6+ years of experience in DFIR & Threat Hunting), the course focuses on real attack simulations, rule creation, and compliance monitoring - just like a production SOC.
𝟮𝟴 𝗠𝗮𝗿 – 𝟭𝟮 𝗔𝗽𝗿 𝟮𝟬𝟮𝟲
𝟬𝟵:𝟬𝟬 – 𝟭𝟯:𝟬𝟬 (𝗜𝗦𝗧) | 𝗪𝗲𝗲𝗸𝗲𝗻𝗱𝘀
𝗪𝗵𝗮𝘁 𝘆𝗼𝘂’𝗹𝗹 𝗴𝗮𝗶𝗻:
24-hour instructor-led, hands-on training
Live Wazuh lab with attack simulations
Custom decoder & rule development
Vulnerability detection & compliance monitoring
Practical exposure to 𝗦𝗜𝗘𝗠 & 𝗫𝗗𝗥 operationsMove beyond dashboards and alerts. InfosecTrain’s 𝙒𝙖𝙯𝙪𝙝 𝙋𝙧𝙖𝙘𝙩𝙞𝙘𝙖𝙡 𝙏𝙧𝙖𝙞𝙣𝙞𝙣𝙜 is a hands-on, real SOC-focused program designed to help you build, detect, and respond to threats using a live Wazuh environment. This training is built for professionals who want practical SOC experience, not just tool familiarity. Led by Urvesh Thakkar (6+ years of experience in DFIR & Threat Hunting), the course focuses on real attack simulations, rule creation, and compliance monitoring - just like a production SOC. 📅 𝟮𝟴 𝗠𝗮𝗿 – 𝟭𝟮 𝗔𝗽𝗿 𝟮𝟬𝟮𝟲 🕘 𝟬𝟵:𝟬𝟬 – 𝟭𝟯:𝟬𝟬 (𝗜𝗦𝗧) | 𝗪𝗲𝗲𝗸𝗲𝗻𝗱𝘀 ✨ 𝗪𝗵𝗮𝘁 𝘆𝗼𝘂’𝗹𝗹 𝗴𝗮𝗶𝗻: 👉 24-hour instructor-led, hands-on training 👉 Live Wazuh lab with attack simulations 👉 Custom decoder & rule development 👉 Vulnerability detection & compliance monitoring 👉 Practical exposure to 𝗦𝗜𝗘𝗠 & 𝗫𝗗𝗥 operations0 Comments 0 Shares 2386 Views 0 Reviews - 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐰𝐨𝐫𝐤𝐬 𝐛𝐞𝐬𝐭 𝐰𝐡𝐞𝐧 𝐢𝐭 𝐬𝐭𝐚𝐫𝐭𝐬 𝐛𝐞𝐟𝐨𝐫𝐞 𝐩𝐫𝐨𝐝𝐮𝐜𝐭𝐢𝐨𝐧.
The 𝐃𝐞𝐯𝐒𝐞𝐜𝐎𝐩𝐬 𝐩𝐢𝐩𝐞𝐥𝐢𝐧𝐞 shows how security must be embedded at every stage, 𝐟𝐫𝐨𝐦 𝐜𝐨𝐝𝐞 𝐜𝐫𝐞𝐚𝐭𝐢𝐨𝐧 𝐭𝐨 𝐜𝐥𝐨𝐮𝐝 𝐨𝐩𝐞𝐫𝐚𝐭𝐢𝐨𝐧𝐬.
By shifting security left, teams catch issues earlier, reduce remediation costs, and deliver software faster without compromising trust.
From secure coding and dependency checks 𝐭𝐨 𝐫𝐮𝐧𝐭𝐢𝐦𝐞 𝐩𝐫𝐨𝐭𝐞𝐜𝐭𝐢𝐨𝐧 𝐚𝐧𝐝 𝐦𝐨𝐧𝐢𝐭𝐨𝐫𝐢𝐧𝐠, 𝐞𝐚𝐜𝐡 𝐬𝐭𝐚𝐠𝐞 𝐩𝐥𝐚𝐲𝐬 𝐚 𝐜𝐫𝐢𝐭𝐢𝐜𝐚𝐥 𝐫𝐨𝐥𝐞 𝐢𝐧 𝐛𝐮𝐢𝐥𝐝𝐢𝐧𝐠 𝐫𝐞𝐬𝐢𝐥𝐢𝐞𝐧𝐭 𝐚𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 𝐚𝐧𝐝 𝐜𝐥𝐨𝐮𝐝 𝐞𝐧𝐯𝐢𝐫𝐨𝐧𝐦𝐞𝐧𝐭𝐬.
𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐰𝐨𝐫𝐤𝐬 𝐛𝐞𝐬𝐭 𝐰𝐡𝐞𝐧 𝐢𝐭 𝐬𝐭𝐚𝐫𝐭𝐬 𝐛𝐞𝐟𝐨𝐫𝐞 𝐩𝐫𝐨𝐝𝐮𝐜𝐭𝐢𝐨𝐧. The 𝐃𝐞𝐯𝐒𝐞𝐜𝐎𝐩𝐬 𝐩𝐢𝐩𝐞𝐥𝐢𝐧𝐞 shows how security must be embedded at every stage, 𝐟𝐫𝐨𝐦 𝐜𝐨𝐝𝐞 𝐜𝐫𝐞𝐚𝐭𝐢𝐨𝐧 𝐭𝐨 𝐜𝐥𝐨𝐮𝐝 𝐨𝐩𝐞𝐫𝐚𝐭𝐢𝐨𝐧𝐬. By shifting security left, teams catch issues earlier, reduce remediation costs, and deliver software faster without compromising trust. From secure coding and dependency checks 𝐭𝐨 𝐫𝐮𝐧𝐭𝐢𝐦𝐞 𝐩𝐫𝐨𝐭𝐞𝐜𝐭𝐢𝐨𝐧 𝐚𝐧𝐝 𝐦𝐨𝐧𝐢𝐭𝐨𝐫𝐢𝐧𝐠, 𝐞𝐚𝐜𝐡 𝐬𝐭𝐚𝐠𝐞 𝐩𝐥𝐚𝐲𝐬 𝐚 𝐜𝐫𝐢𝐭𝐢𝐜𝐚𝐥 𝐫𝐨𝐥𝐞 𝐢𝐧 𝐛𝐮𝐢𝐥𝐝𝐢𝐧𝐠 𝐫𝐞𝐬𝐢𝐥𝐢𝐞𝐧𝐭 𝐚𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 𝐚𝐧𝐝 𝐜𝐥𝐨𝐮𝐝 𝐞𝐧𝐯𝐢𝐫𝐨𝐧𝐦𝐞𝐧𝐭𝐬.0 Comments 0 Shares 3316 Views 0 Reviews - 𝗖𝗖𝗜𝗦𝗢 – 𝗖𝗲𝗿𝘁𝗶𝗳𝗶𝗲𝗱 𝗖𝗵𝗶𝗲𝗳 𝗜𝗻𝗳𝗼𝗿𝗺𝗮𝘁𝗶𝗼𝗻 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗢𝗳𝗳𝗶𝗰𝗲𝗿 𝗧𝗿𝗮𝗶𝗻𝗶𝗻𝗴.
Become the Security Leader Organizations Rely On
Step into executive cybersecurity leadership with InfosecTrain’s 𝗖𝗖𝗜𝗦𝗢 𝗖𝗲𝗿𝘁𝗶𝗳𝗶𝗰𝗮𝘁𝗶𝗼𝗻 𝗧𝗿𝗮𝗶𝗻𝗶𝗻𝗴. This 40-hour, instructor-led program is built for professionals ready to move from technical roles to strategic security leadership.
𝟬𝟳 𝗙𝗲𝗯 – 𝟭𝟱 𝗠𝗮𝗿 𝟮𝟬𝟮𝟲 | 𝟬𝟵:𝟬𝟬–𝟭𝟯:𝟬𝟬 (𝗜𝗦𝗧) | 𝗪𝗲𝗲𝗸𝗲𝗻𝗱𝘀
Instructor: Sanyam Negi (10+ Years Experience)
𝗪𝗵𝗮𝘁 𝗬𝗼𝘂 𝗚𝗲𝘁:
Real-world, CISO-level scenarios
Access to recorded sessions
Training certificate
Leadership-focused security mindset🔐𝗖𝗖𝗜𝗦𝗢 – 𝗖𝗲𝗿𝘁𝗶𝗳𝗶𝗲𝗱 𝗖𝗵𝗶𝗲𝗳 𝗜𝗻𝗳𝗼𝗿𝗺𝗮𝘁𝗶𝗼𝗻 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗢𝗳𝗳𝗶𝗰𝗲𝗿 𝗧𝗿𝗮𝗶𝗻𝗶𝗻𝗴. Become the Security Leader Organizations Rely On Step into executive cybersecurity leadership with InfosecTrain’s 𝗖𝗖𝗜𝗦𝗢 𝗖𝗲𝗿𝘁𝗶𝗳𝗶𝗰𝗮𝘁𝗶𝗼𝗻 𝗧𝗿𝗮𝗶𝗻𝗶𝗻𝗴. This 40-hour, instructor-led program is built for professionals ready to move from technical roles to strategic security leadership. 📅 𝟬𝟳 𝗙𝗲𝗯 – 𝟭𝟱 𝗠𝗮𝗿 𝟮𝟬𝟮𝟲 | 🕘 𝟬𝟵:𝟬𝟬–𝟭𝟯:𝟬𝟬 (𝗜𝗦𝗧) | 𝗪𝗲𝗲𝗸𝗲𝗻𝗱𝘀 👨🏫 Instructor: Sanyam Negi (10+ Years Experience) 📌 𝗪𝗵𝗮𝘁 𝗬𝗼𝘂 𝗚𝗲𝘁: ⭐ Real-world, CISO-level scenarios ⭐ Access to recorded sessions ⭐ Training certificate ⭐ Leadership-focused security mindset0 Comments 0 Shares 4243 Views 0 Reviews - 𝐂𝐡𝐨𝐨𝐬𝐢𝐧𝐠 𝐚 𝐒𝐈𝐄𝐌 𝐢𝐬𝐧’𝐭 𝐚𝐛𝐨𝐮𝐭 𝐰𝐡𝐢𝐜𝐡 𝐭𝐨𝐨𝐥 𝐢𝐬 “𝐛𝐞𝐭𝐭𝐞𝐫.”
𝐈𝐭’𝐬 𝐚𝐛𝐨𝐮𝐭 𝐰𝐡𝐢𝐜𝐡 𝐨𝐧𝐞 𝐟𝐢𝐭𝐬 𝐲𝐨𝐮𝐫 𝐫𝐞𝐚𝐥𝐢𝐭𝐲.
Wazuh gives teams 𝐚𝐧 𝐨𝐩𝐞𝐧-𝐬𝐨𝐮𝐫𝐜𝐞, 𝐟𝐥𝐞𝐱𝐢𝐛𝐥𝐞 𝐒𝐈𝐄𝐌 𝐚𝐧𝐝 𝐗𝐃𝐑 𝐩𝐥𝐚𝐭𝐟𝐨𝐫𝐦 𝐰𝐢𝐭𝐡 𝐬𝐭𝐫𝐨𝐧𝐠 𝐜𝐨𝐦𝐩𝐥𝐢𝐚𝐧𝐜𝐞 𝐜𝐨𝐯𝐞𝐫𝐚𝐠𝐞 𝐚𝐧𝐝 𝐟𝐮𝐥𝐥 𝐜𝐨𝐧𝐭𝐫𝐨𝐥.
Splunk offers a polished, enterprise-grade experience built for scale, speed, and managed operations.
𝐁𝐨𝐭𝐡 𝐬𝐨𝐥𝐯𝐞 𝐫𝐞𝐚𝐥 𝐩𝐫𝐨𝐛𝐥𝐞𝐦𝐬.
The difference lies in budget, skills, and how much control you want over your security stack.
𝐈𝐟 𝐲𝐨𝐮’𝐫𝐞 𝐥𝐨𝐨𝐤𝐢𝐧𝐠 𝐭𝐨 𝐛𝐮𝐢𝐥𝐝 𝐡𝐚𝐧𝐝𝐬-𝐨𝐧 𝐒𝐈𝐄𝐌 𝐬𝐤𝐢𝐥𝐥𝐬 𝐰𝐢𝐭𝐡 𝐖𝐚𝐳𝐮𝐡 𝐚𝐧𝐝 𝐮𝐧𝐝𝐞𝐫𝐬𝐭𝐚𝐧𝐝 𝐡𝐨𝐰 𝐢𝐭 𝐰𝐨𝐫𝐤𝐬 𝐢𝐧 𝐫𝐞𝐚𝐥 𝐒𝐎𝐂 𝐞𝐧𝐯𝐢𝐫𝐨𝐧𝐦𝐞𝐧𝐭𝐬, 𝐬𝐭𝐫𝐮𝐜𝐭𝐮𝐫𝐞𝐝 𝐭𝐫𝐚𝐢𝐧𝐢𝐧𝐠 𝐦𝐚𝐤𝐞𝐬 𝐚𝐥𝐥 𝐭𝐡𝐞 𝐝𝐢𝐟𝐟𝐞𝐫𝐞𝐧𝐜𝐞.𝐂𝐡𝐨𝐨𝐬𝐢𝐧𝐠 𝐚 𝐒𝐈𝐄𝐌 𝐢𝐬𝐧’𝐭 𝐚𝐛𝐨𝐮𝐭 𝐰𝐡𝐢𝐜𝐡 𝐭𝐨𝐨𝐥 𝐢𝐬 “𝐛𝐞𝐭𝐭𝐞𝐫.” 𝐈𝐭’𝐬 𝐚𝐛𝐨𝐮𝐭 𝐰𝐡𝐢𝐜𝐡 𝐨𝐧𝐞 𝐟𝐢𝐭𝐬 𝐲𝐨𝐮𝐫 𝐫𝐞𝐚𝐥𝐢𝐭𝐲. Wazuh gives teams 𝐚𝐧 𝐨𝐩𝐞𝐧-𝐬𝐨𝐮𝐫𝐜𝐞, 𝐟𝐥𝐞𝐱𝐢𝐛𝐥𝐞 𝐒𝐈𝐄𝐌 𝐚𝐧𝐝 𝐗𝐃𝐑 𝐩𝐥𝐚𝐭𝐟𝐨𝐫𝐦 𝐰𝐢𝐭𝐡 𝐬𝐭𝐫𝐨𝐧𝐠 𝐜𝐨𝐦𝐩𝐥𝐢𝐚𝐧𝐜𝐞 𝐜𝐨𝐯𝐞𝐫𝐚𝐠𝐞 𝐚𝐧𝐝 𝐟𝐮𝐥𝐥 𝐜𝐨𝐧𝐭𝐫𝐨𝐥. Splunk offers a polished, enterprise-grade experience built for scale, speed, and managed operations. 𝐁𝐨𝐭𝐡 𝐬𝐨𝐥𝐯𝐞 𝐫𝐞𝐚𝐥 𝐩𝐫𝐨𝐛𝐥𝐞𝐦𝐬. The difference lies in budget, skills, and how much control you want over your security stack. 𝐈𝐟 𝐲𝐨𝐮’𝐫𝐞 𝐥𝐨𝐨𝐤𝐢𝐧𝐠 𝐭𝐨 𝐛𝐮𝐢𝐥𝐝 𝐡𝐚𝐧𝐝𝐬-𝐨𝐧 𝐒𝐈𝐄𝐌 𝐬𝐤𝐢𝐥𝐥𝐬 𝐰𝐢𝐭𝐡 𝐖𝐚𝐳𝐮𝐡 𝐚𝐧𝐝 𝐮𝐧𝐝𝐞𝐫𝐬𝐭𝐚𝐧𝐝 𝐡𝐨𝐰 𝐢𝐭 𝐰𝐨𝐫𝐤𝐬 𝐢𝐧 𝐫𝐞𝐚𝐥 𝐒𝐎𝐂 𝐞𝐧𝐯𝐢𝐫𝐨𝐧𝐦𝐞𝐧𝐭𝐬, 𝐬𝐭𝐫𝐮𝐜𝐭𝐮𝐫𝐞𝐝 𝐭𝐫𝐚𝐢𝐧𝐢𝐧𝐠 𝐦𝐚𝐤𝐞𝐬 𝐚𝐥𝐥 𝐭𝐡𝐞 𝐝𝐢𝐟𝐟𝐞𝐫𝐞𝐧𝐜𝐞.0 Comments 0 Shares 3819 Views 0 Reviews - 𝐖𝐡𝐚𝐭 𝐠𝐞𝐭𝐬 𝐦𝐞𝐚𝐬𝐮𝐫𝐞𝐝 𝐠𝐞𝐭𝐬 𝐦𝐚𝐧𝐚𝐠𝐞𝐝, 𝐞𝐬𝐩𝐞𝐜𝐢𝐚𝐥𝐥𝐲 𝐚𝐭 𝐭𝐡𝐞 𝐂𝐈𝐒𝐎 𝐥𝐞𝐯𝐞𝐥.
Modern security leadership isn’t about counting alerts.
It’s about 𝐭𝐞𝐥𝐥𝐢𝐧𝐠 𝐚 𝐜𝐥𝐞𝐚𝐫, 𝐛𝐮𝐬𝐢𝐧𝐞𝐬𝐬-𝐟𝐨𝐜𝐮𝐬𝐞𝐝 𝐫𝐢𝐬𝐤 𝐬𝐭𝐨𝐫𝐲 𝐭𝐨 𝐭𝐡𝐞 𝐛𝐨𝐚𝐫𝐝.
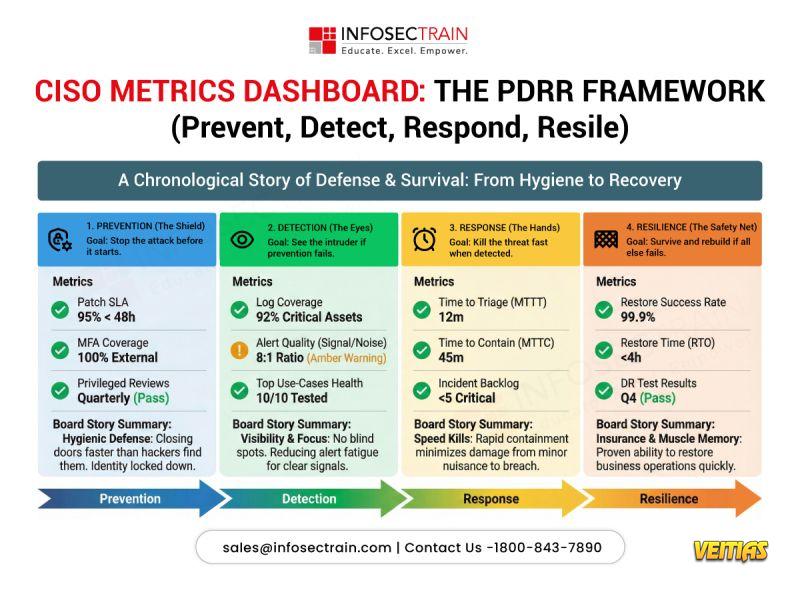
The PDRR framework (𝐏𝐫𝐞𝐯𝐞𝐧𝐭, 𝐃𝐞𝐭𝐞𝐜𝐭, 𝐑𝐞𝐬𝐩𝐨𝐧𝐝, 𝐑𝐞𝐬𝐢𝐥𝐞) helps CISOs align metrics across the entire security lifecycle:
• 𝐏𝐫𝐞𝐯𝐞𝐧𝐭 – Reduce attack opportunities
• 𝐃𝐞𝐭𝐞𝐜𝐭 – Gain early, high-fidelity visibility
• 𝐑𝐞𝐬𝐩𝐨𝐧𝐝 – Contain threats quickly
• 𝐑𝐞𝐬𝐢𝐥𝐞 – Recover and sustain business operations
When metrics follow this structure, 𝐜𝐨𝐧𝐯𝐞𝐫𝐬𝐚𝐭𝐢𝐨𝐧𝐬 𝐬𝐡𝐢𝐟𝐭 𝐟𝐫𝐨𝐦 𝐭𝐨𝐨𝐥𝐬 𝐭𝐨 𝐫𝐢𝐬𝐤, 𝐫𝐞𝐬𝐢𝐥𝐢𝐞𝐧𝐜𝐞, 𝐚𝐧𝐝 𝐨𝐮𝐭𝐜𝐨𝐦𝐞𝐬.
𝐖𝐡𝐚𝐭 𝐠𝐞𝐭𝐬 𝐦𝐞𝐚𝐬𝐮𝐫𝐞𝐝 𝐠𝐞𝐭𝐬 𝐦𝐚𝐧𝐚𝐠𝐞𝐝, 𝐞𝐬𝐩𝐞𝐜𝐢𝐚𝐥𝐥𝐲 𝐚𝐭 𝐭𝐡𝐞 𝐂𝐈𝐒𝐎 𝐥𝐞𝐯𝐞𝐥. Modern security leadership isn’t about counting alerts. It’s about 𝐭𝐞𝐥𝐥𝐢𝐧𝐠 𝐚 𝐜𝐥𝐞𝐚𝐫, 𝐛𝐮𝐬𝐢𝐧𝐞𝐬𝐬-𝐟𝐨𝐜𝐮𝐬𝐞𝐝 𝐫𝐢𝐬𝐤 𝐬𝐭𝐨𝐫𝐲 𝐭𝐨 𝐭𝐡𝐞 𝐛𝐨𝐚𝐫𝐝. The PDRR framework (𝐏𝐫𝐞𝐯𝐞𝐧𝐭, 𝐃𝐞𝐭𝐞𝐜𝐭, 𝐑𝐞𝐬𝐩𝐨𝐧𝐝, 𝐑𝐞𝐬𝐢𝐥𝐞) helps CISOs align metrics across the entire security lifecycle: • 𝐏𝐫𝐞𝐯𝐞𝐧𝐭 – Reduce attack opportunities • 𝐃𝐞𝐭𝐞𝐜𝐭 – Gain early, high-fidelity visibility • 𝐑𝐞𝐬𝐩𝐨𝐧𝐝 – Contain threats quickly • 𝐑𝐞𝐬𝐢𝐥𝐞 – Recover and sustain business operations When metrics follow this structure, 𝐜𝐨𝐧𝐯𝐞𝐫𝐬𝐚𝐭𝐢𝐨𝐧𝐬 𝐬𝐡𝐢𝐟𝐭 𝐟𝐫𝐨𝐦 𝐭𝐨𝐨𝐥𝐬 𝐭𝐨 𝐫𝐢𝐬𝐤, 𝐫𝐞𝐬𝐢𝐥𝐢𝐞𝐧𝐜𝐞, 𝐚𝐧𝐝 𝐨𝐮𝐭𝐜𝐨𝐦𝐞𝐬.0 Comments 0 Shares 6459 Views 0 Reviews
More Stories