- 227 Записей
- 199 Фото
- 0 Видео
- Male
- 14/07/2002
- Читают 1 человек
© 2025 Veitias Social Network Club  Russian
Russian
Недавние обновления
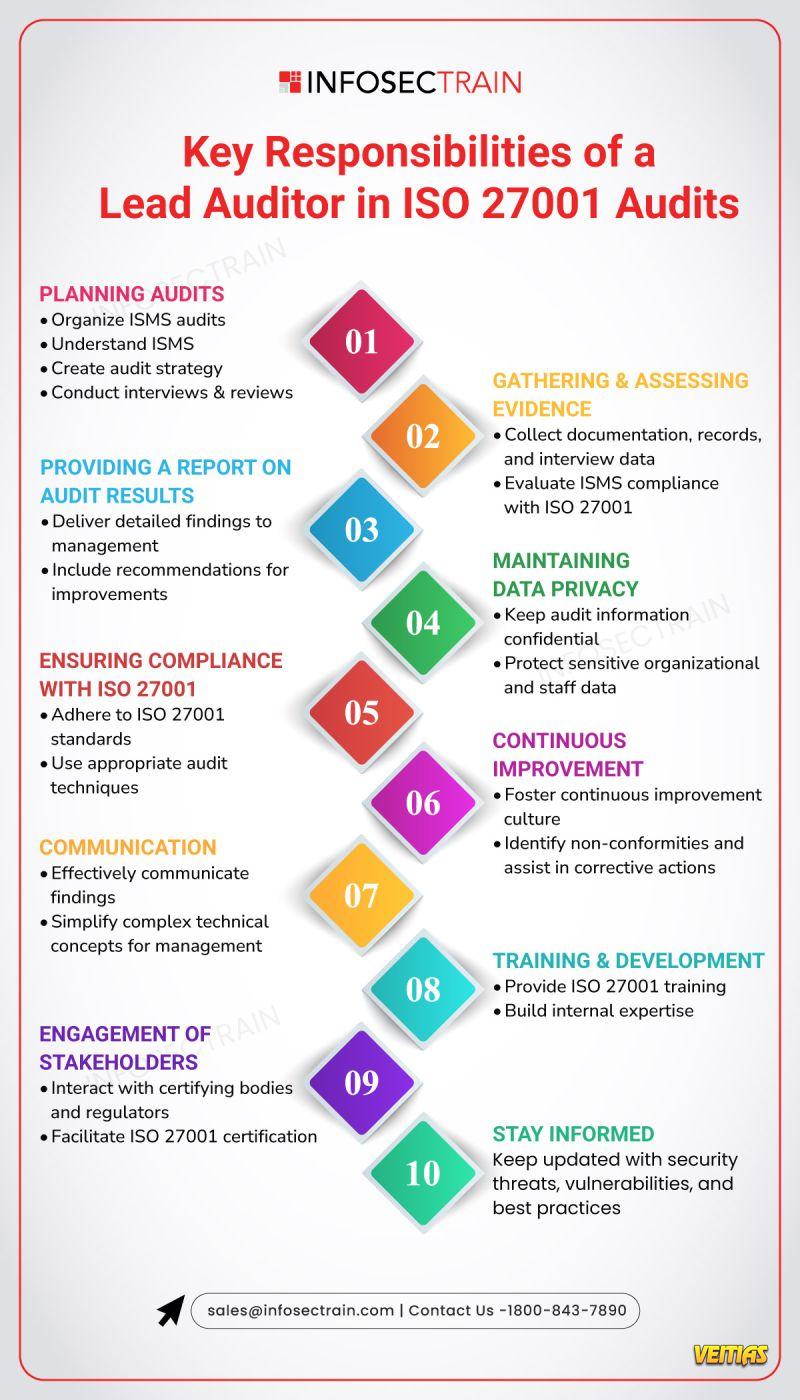
- A Lead Auditor in ISO 27001 audits plays a crucial role in evaluating an organization's Information Security Management System (ISMS). Their key responsibilities include planning and conducting audits in accordance with ISO 27001 standards, assessing the effectiveness of security controls, identifying areas of non-compliance or risk, and ensuring continuous improvement of the ISMS. They lead audit teams, communicate findings to stakeholders, and provide clear documentation and reports that support certification or compliance efforts. Their role is vital in helping organizations maintain robust information security frameworks and meet regulatory requirements.
https://www.infosectrain.com/courses/iso-iec-42001-lead-auditor-training/A Lead Auditor in ISO 27001 audits plays a crucial role in evaluating an organization's Information Security Management System (ISMS). Their key responsibilities include planning and conducting audits in accordance with ISO 27001 standards, assessing the effectiveness of security controls, identifying areas of non-compliance or risk, and ensuring continuous improvement of the ISMS. They lead audit teams, communicate findings to stakeholders, and provide clear documentation and reports that support certification or compliance efforts. Their role is vital in helping organizations maintain robust information security frameworks and meet regulatory requirements. https://www.infosectrain.com/courses/iso-iec-42001-lead-auditor-training/0 Комментарии 0 Поделились 415 Просмотры 0 предпросмотрВойдите, чтобы отмечать, делиться и комментировать! - AI Governance refers to the frameworks, policies, and processes that guide the responsible development, deployment, and use of artificial intelligence technologies. It can be broadly categorized into several types. Technical governance focuses on ensuring transparency, accountability, and fairness in algorithms and data usage. Ethical governance involves establishing moral principles to prevent harm and promote fairness, privacy, and human rights. Regulatory governance includes government and institutional policies, laws, and standards to control AI risks and ensure compliance.AI Governance refers to the frameworks, policies, and processes that guide the responsible development, deployment, and use of artificial intelligence technologies. It can be broadly categorized into several types. Technical governance focuses on ensuring transparency, accountability, and fairness in algorithms and data usage. Ethical governance involves establishing moral principles to prevent harm and promote fairness, privacy, and human rights. Regulatory governance includes government and institutional policies, laws, and standards to control AI risks and ensure compliance.0 Комментарии 0 Поделились 4201 Просмотры 0 предпросмотр
- Free Masterclass on DevSecOps in 2025: Emerging Trends and Future Outlook
Date: 15 Apr (Tue)
Time: 08:30 – 09:30 PM (IST)
Speaker: Santhosh
Free Register Now: https://www.infosectrain.com/events/devsecops-in-2025-emerging-trends-and-future-outlook/
Agenda for the Masterclass
• The Evolution of DevSecOps: Where We Stand Today
• Emerging Trends Shaping DevSecOps in 2025
• Future Insights and Industry Predictions
• Practical Implementations: Case Studies and Success Stories
• Interactive Q&A Session
• Key Takeaways and Closing Thoughts
Free Masterclass on DevSecOps in 2025: Emerging Trends and Future Outlook Date: 15 Apr (Tue) Time: 08:30 – 09:30 PM (IST) Speaker: Santhosh Free Register Now: https://www.infosectrain.com/events/devsecops-in-2025-emerging-trends-and-future-outlook/ Agenda for the Masterclass • The Evolution of DevSecOps: Where We Stand Today • Emerging Trends Shaping DevSecOps in 2025 • Future Insights and Industry Predictions • Practical Implementations: Case Studies and Success Stories • Interactive Q&A Session • Key Takeaways and Closing Thoughts0 Комментарии 0 Поделились 5604 Просмотры 0 предпросмотр - In the ever-evolving world of cybersecurity, having the right tools at your fingertips can make all the difference. Whether you're conducting threat intelligence, malware analysis, or vulnerability assessments, specialized search engines offer unparalleled insights and capabilities. This curated list of 30 powerful cybersecurity search engines is your ultimate resource to streamline investigations, uncover threats, and stay ahead of cyber risks. From scanning open ports to analyzing indicators of compromise (IOCs), these tools are a must-have for security professionals and enthusiasts alike.In the ever-evolving world of cybersecurity, having the right tools at your fingertips can make all the difference. Whether you're conducting threat intelligence, malware analysis, or vulnerability assessments, specialized search engines offer unparalleled insights and capabilities. This curated list of 30 powerful cybersecurity search engines is your ultimate resource to streamline investigations, uncover threats, and stay ahead of cyber risks. From scanning open ports to analyzing indicators of compromise (IOCs), these tools are a must-have for security professionals and enthusiasts alike.0 Комментарии 0 Поделились 2955 Просмотры 0 предпросмотр
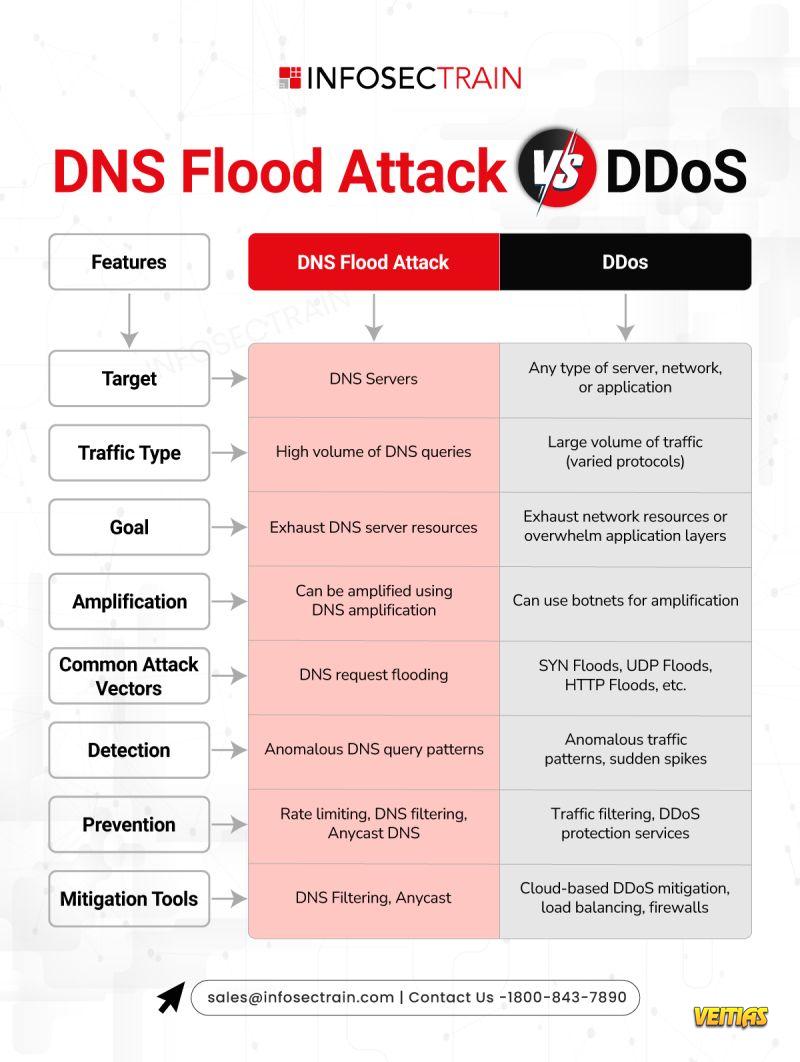
- A DNS Flood Attack is a type of Denial-of-Service (DoS) attack that targets DNS servers by overwhelming them with a high volume of fake DNS requests, exhausting server resources and making domain resolution unavailable for legitimate users. This attack disrupts websites, applications, and online services by overloading the authoritative DNS infrastructure.A DNS Flood Attack is a type of Denial-of-Service (DoS) attack that targets DNS servers by overwhelming them with a high volume of fake DNS requests, exhausting server resources and making domain resolution unavailable for legitimate users. This attack disrupts websites, applications, and online services by overloading the authoritative DNS infrastructure.0 Комментарии 0 Поделились 4374 Просмотры 0 предпросмотр
- Disruptions happen when you least expect them—will your business be ready? Check out this infographic to see how Cloud Computing powers Business Continuity and Disaster Recovery (BCDR), ensuring rapid recovery, secure data, and minimal downtime. Protect your operations, no matter the storm!Disruptions happen when you least expect them—will your business be ready? 🚨 Check out this infographic to see how Cloud Computing powers Business Continuity and Disaster Recovery (BCDR), ensuring rapid recovery, secure data, and minimal downtime. 🌐☁️ Protect your operations, no matter the storm!0 Комментарии 0 Поделились 1911 Просмотры 0 предпросмотр
- The Canvas of Cybersecurity represents a vast and dynamic landscape encompassing various strategies, technologies, and best practices aimed at protecting digital assets. It includes network security, endpoint protection, cloud security, data privacy, risk management, and compliance frameworks that organizations must implement to safeguard against cyber threats. With the rise of AI-driven cyberattacks, ransomware, and phishing schemes, cybersecurity professionals must continuously adapt by leveraging threat intelligence, security analytics, and incident response strategies. Cybersecurity is not just about deploying firewalls or antivirus solutions—it requires a holistic approach that integrates secure coding practices, zero-trust architecture, employee awareness training, and continuous monitoring.The Canvas of Cybersecurity represents a vast and dynamic landscape encompassing various strategies, technologies, and best practices aimed at protecting digital assets. It includes network security, endpoint protection, cloud security, data privacy, risk management, and compliance frameworks that organizations must implement to safeguard against cyber threats. With the rise of AI-driven cyberattacks, ransomware, and phishing schemes, cybersecurity professionals must continuously adapt by leveraging threat intelligence, security analytics, and incident response strategies. Cybersecurity is not just about deploying firewalls or antivirus solutions—it requires a holistic approach that integrates secure coding practices, zero-trust architecture, employee awareness training, and continuous monitoring.0 Комментарии 0 Поделились 7862 Просмотры 0 предпросмотр
- Network security heavily depends on the proper configuration of secure and insecure ports. Insecure ports are those that lack encryption or authentication, making them vulnerable to cyber threats such as unauthorized access, data breaches, and malware attacks. Common insecure ports include FTP (Port 21), Telnet (Port 23), and HTTP (Port 80), which transmit data in plain text, exposing sensitive information to potential attackers. On the other hand, secure ports use encryption and authentication mechanisms to protect data transmission. Examples include HTTPS (Port 443), SSH (Port 22), and FTPS (Port 990), which ensure secure communication over networks. Organizations must implement firewalls, port filtering, and regular security audits to safeguard their infrastructure from cyber threats. By understanding the difference between insecure and secure ports, businesses can enhance their network security and prevent unauthorized access to critical systems.Network security heavily depends on the proper configuration of secure and insecure ports. Insecure ports are those that lack encryption or authentication, making them vulnerable to cyber threats such as unauthorized access, data breaches, and malware attacks. Common insecure ports include FTP (Port 21), Telnet (Port 23), and HTTP (Port 80), which transmit data in plain text, exposing sensitive information to potential attackers. On the other hand, secure ports use encryption and authentication mechanisms to protect data transmission. Examples include HTTPS (Port 443), SSH (Port 22), and FTPS (Port 990), which ensure secure communication over networks. Organizations must implement firewalls, port filtering, and regular security audits to safeguard their infrastructure from cyber threats. By understanding the difference between insecure and secure ports, businesses can enhance their network security and prevent unauthorized access to critical systems.0 Комментарии 0 Поделились 3632 Просмотры 0 предпросмотр
- Join Our Exclusive Webinar: "CIPM in Action: Building a Robust Data Privacy Program"
Are you ready to master data privacy management? Learn how to build and sustain a strong privacy program with our CIPM Masterclass led by industry experts at InfosecTrain!
Date: 28th March (Friday)
Time: 8:00 – 9:00 PM (IST)
Register here: https://www.infosectrain.com/events/cipm-in-action-building-a-robust-data-privacy-program/
Agenda Highlights:
Assess: Data Discovery and Assessments
Protect: Implementing Effective Controls
Sustain: Audit & Training Strategies
Respond: Managing Data Subject Rights & Breach Response
Why CIPM with InfosecTrain
Live Q&A Session
Whether you're a privacy professional, compliance officer, or cybersecurity enthusiast, this masterclass will equip you with practical insights to implement and manage data privacy effectively.
Register now and take the next step toward CIPM certification!📢 Join Our Exclusive Webinar: "CIPM in Action: Building a Robust Data Privacy Program" 🔍 Are you ready to master data privacy management? Learn how to build and sustain a strong privacy program with our CIPM Masterclass led by industry experts at InfosecTrain! 📅 Date: 28th March (Friday) ⏰ Time: 8:00 – 9:00 PM (IST) Register here: https://www.infosectrain.com/events/cipm-in-action-building-a-robust-data-privacy-program/ 🔹 Agenda Highlights: ✅ Assess: Data Discovery and Assessments ✅ Protect: Implementing Effective Controls ✅ Sustain: Audit & Training Strategies ✅ Respond: Managing Data Subject Rights & Breach Response ✅ Why CIPM with InfosecTrain ✅ Live Q&A Session 🚀 Whether you're a privacy professional, compliance officer, or cybersecurity enthusiast, this masterclass will equip you with practical insights to implement and manage data privacy effectively. 🔗 Register now and take the next step toward CIPM certification!WWW.INFOSECTRAIN.COMCIPM in Action: Building a Robust Data Privacy ProgramInfosecTrain offer free masterclass "CIPM in Action: Building a Robust Data Privacy Program" with Jai0 Комментарии 0 Поделились 1743 Просмотры 0 предпросмотр - We're Back and Thrilled to Unveil Our Latest Batch: "𝐂𝐈𝐒𝐒𝐏 𝐎𝐧𝐥𝐢𝐧𝐞 𝐓𝐫𝐚𝐢𝐧𝐢𝐧𝐠 𝐂𝐨𝐮𝐫𝐬𝐞" – Last Few Seats Left, Enroll Now and Master Your Cybersecurity Skills with Expert-Led Training!
Join our 48-hour immersive CISSP training starting March 31st, and learn from Prabh Nair, an industry expert with years of experience in the field of cybersecurity.
Why CISSP? CISSP is the most renowned certification in the information security domain, highly respected globally, and is crucial for those aiming to design, manage, and protect enterprise IT infrastructures.We're Back and Thrilled to Unveil Our Latest Batch: "𝐂𝐈𝐒𝐒𝐏 𝐎𝐧𝐥𝐢𝐧𝐞 𝐓𝐫𝐚𝐢𝐧𝐢𝐧𝐠 𝐂𝐨𝐮𝐫𝐬𝐞" – Last Few Seats Left, Enroll Now and Master Your Cybersecurity Skills with Expert-Led Training! Join our 48-hour immersive CISSP training starting March 31st, and learn from Prabh Nair, an industry expert with years of experience in the field of cybersecurity. Why CISSP? CISSP is the most renowned certification in the information security domain, highly respected globally, and is crucial for those aiming to design, manage, and protect enterprise IT infrastructures.0 Комментарии 0 Поделились 1686 Просмотры 0 предпросмотр
Больше