Red Team Attack Lifecycle
Cyberattacks don’t happen overnight they follow a well-defined lifecycle.
Understanding each phase is critical for building strong defenses. Here’s how attackers operate:
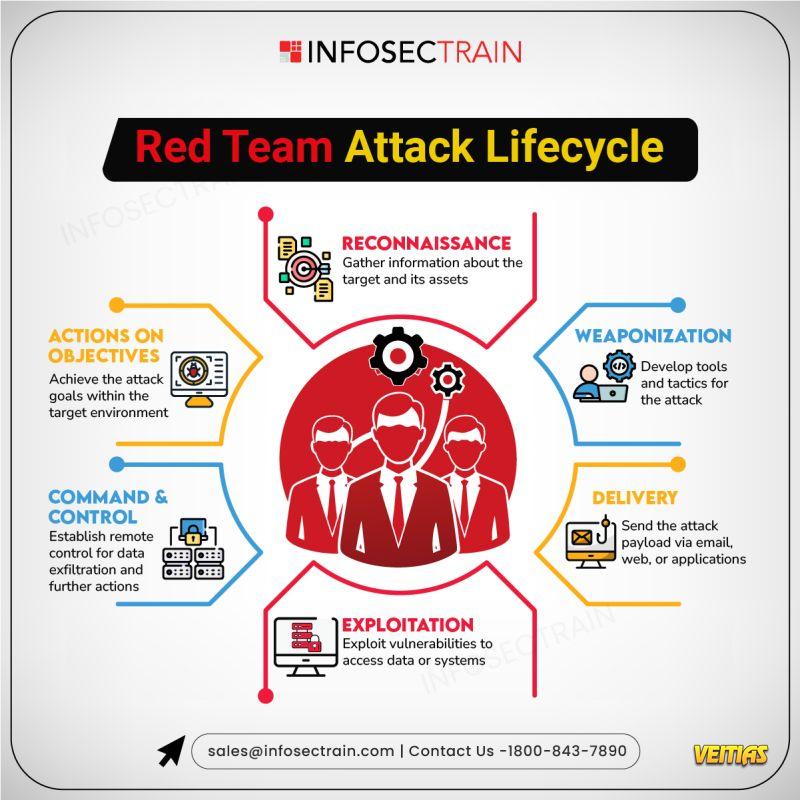
1⃣ Reconnaissance – Gather intel on the target
2⃣ Weaponization – Develop tools & tactics
3⃣ Delivery – Send the attack payload (email, web, apps)
4⃣ Exploitation – Exploit vulnerabilities to gain access
5⃣ Command & Control – Establish remote control for data theft
6⃣ Actions on Objectives – Achieve attack goals inside the target environment
Red Team exercises simulate these steps to test organizational resilience and improve security architecture.
Learn how to defend against real-world threats with Infosec Train’s Red Team & Cybersecurity Training Programs.
#RedTeam #CyberSecurity #EthicalHacking #PenTesting #ThreatHunting #CyberDefense #InfoSec #InfosecTrain
Cyberattacks don’t happen overnight they follow a well-defined lifecycle.
Understanding each phase is critical for building strong defenses. Here’s how attackers operate:
1⃣ Reconnaissance – Gather intel on the target
2⃣ Weaponization – Develop tools & tactics
3⃣ Delivery – Send the attack payload (email, web, apps)
4⃣ Exploitation – Exploit vulnerabilities to gain access
5⃣ Command & Control – Establish remote control for data theft
6⃣ Actions on Objectives – Achieve attack goals inside the target environment
Red Team exercises simulate these steps to test organizational resilience and improve security architecture.
Learn how to defend against real-world threats with Infosec Train’s Red Team & Cybersecurity Training Programs.
#RedTeam #CyberSecurity #EthicalHacking #PenTesting #ThreatHunting #CyberDefense #InfoSec #InfosecTrain
Red Team Attack Lifecycle
Cyberattacks don’t happen overnight they follow a well-defined lifecycle.
Understanding each phase is critical for building strong defenses. Here’s how attackers operate:
1⃣ Reconnaissance – Gather intel on the target
2⃣ Weaponization – Develop tools & tactics
3⃣ Delivery – Send the attack payload (email, web, apps)
4⃣ Exploitation – Exploit vulnerabilities to gain access
5⃣ Command & Control – Establish remote control for data theft
6⃣ Actions on Objectives – Achieve attack goals inside the target environment
💡 Red Team exercises simulate these steps to test organizational resilience and improve security architecture.
👉 Learn how to defend against real-world threats with Infosec Train’s Red Team & Cybersecurity Training Programs.
#RedTeam #CyberSecurity #EthicalHacking #PenTesting #ThreatHunting #CyberDefense #InfoSec #InfosecTrain
0 Comments
0 Shares
3246 Views
0 Reviews