AUTHORIZATION Vs AUTHENTICATION
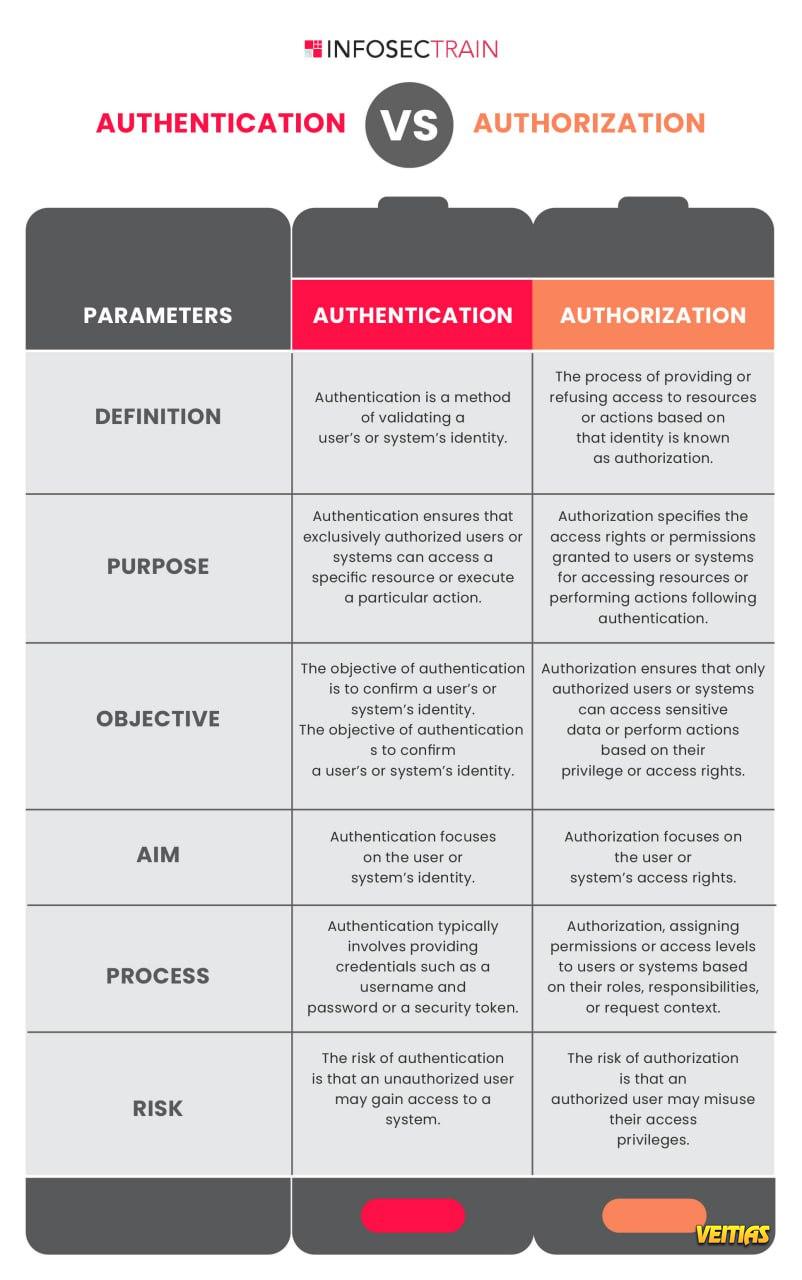
Understanding both authentication and authorization is essential for robust security management.
• Authentication ensures that users are who they claim to be, typically using credentials like usernames and passwords, biometrics, or multi-factor authentication.
• Authorization determines what authenticated users are permitted to do, enforcing policies and permissions to protect sensitive data and resources.
Read Detailed Blog - https://www.infosectrain.com/blog/authentication-vs-authorization/
Together, these processes form the foundation of secure access control, ensuring that only authorized users can perform specific actions within a system. This layered approach is critical for protecting organizational assets and maintaining the integrity of information systems.
Understanding both authentication and authorization is essential for robust security management.
• Authentication ensures that users are who they claim to be, typically using credentials like usernames and passwords, biometrics, or multi-factor authentication.
• Authorization determines what authenticated users are permitted to do, enforcing policies and permissions to protect sensitive data and resources.
Read Detailed Blog - https://www.infosectrain.com/blog/authentication-vs-authorization/
Together, these processes form the foundation of secure access control, ensuring that only authorized users can perform specific actions within a system. This layered approach is critical for protecting organizational assets and maintaining the integrity of information systems.
AUTHORIZATION Vs AUTHENTICATION
Understanding both authentication and authorization is essential for robust security management.
• Authentication ensures that users are who they claim to be, typically using credentials like usernames and passwords, biometrics, or multi-factor authentication.
• Authorization determines what authenticated users are permitted to do, enforcing policies and permissions to protect sensitive data and resources.
Read Detailed Blog - https://www.infosectrain.com/blog/authentication-vs-authorization/
Together, these processes form the foundation of secure access control, ensuring that only authorized users can perform specific actions within a system. This layered approach is critical for protecting organizational assets and maintaining the integrity of information systems.
0 Comments
0 Shares
3067 Views
0 Reviews