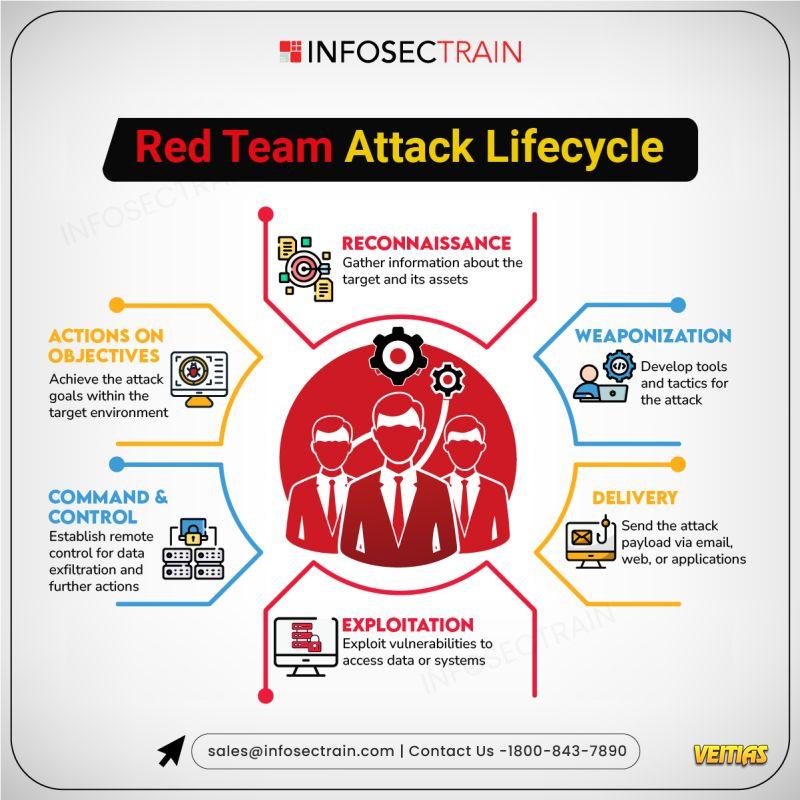
Red Team Attack Lifecycle
InfosecTrain’s latest infographic explores the Red Team Attack Lifecycle, showcasing how adversaries plan, execute, and escalate cyberattacks to test an organization’s defenses. It visually explains each stage of the process, helping security teams strengthen detection, response, and resilience against real-world attack simulations.
Interview Questions for Red Team Expert - https://www.infosectrain.com/blog/interview-questions-for-red-team-expert/
#RedTeam #CyberSecurity #AttackLifecycle #InfoSec #ThreatSimulation #PenTesting #AdversaryEmulation #InfosecTrain #CyberDefense #ITSecurity
InfosecTrain’s latest infographic explores the Red Team Attack Lifecycle, showcasing how adversaries plan, execute, and escalate cyberattacks to test an organization’s defenses. It visually explains each stage of the process, helping security teams strengthen detection, response, and resilience against real-world attack simulations.
Interview Questions for Red Team Expert - https://www.infosectrain.com/blog/interview-questions-for-red-team-expert/
#RedTeam #CyberSecurity #AttackLifecycle #InfoSec #ThreatSimulation #PenTesting #AdversaryEmulation #InfosecTrain #CyberDefense #ITSecurity
Red Team Attack Lifecycle
InfosecTrain’s latest infographic explores the Red Team Attack Lifecycle, showcasing how adversaries plan, execute, and escalate cyberattacks to test an organization’s defenses. It visually explains each stage of the process, helping security teams strengthen detection, response, and resilience against real-world attack simulations.
Interview Questions for Red Team Expert - https://www.infosectrain.com/blog/interview-questions-for-red-team-expert/
#RedTeam #CyberSecurity #AttackLifecycle #InfoSec #ThreatSimulation #PenTesting #AdversaryEmulation #InfosecTrain #CyberDefense #ITSecurity
0 Comentários
0 Compartilhamentos
2729 Visualizações
0 Anterior