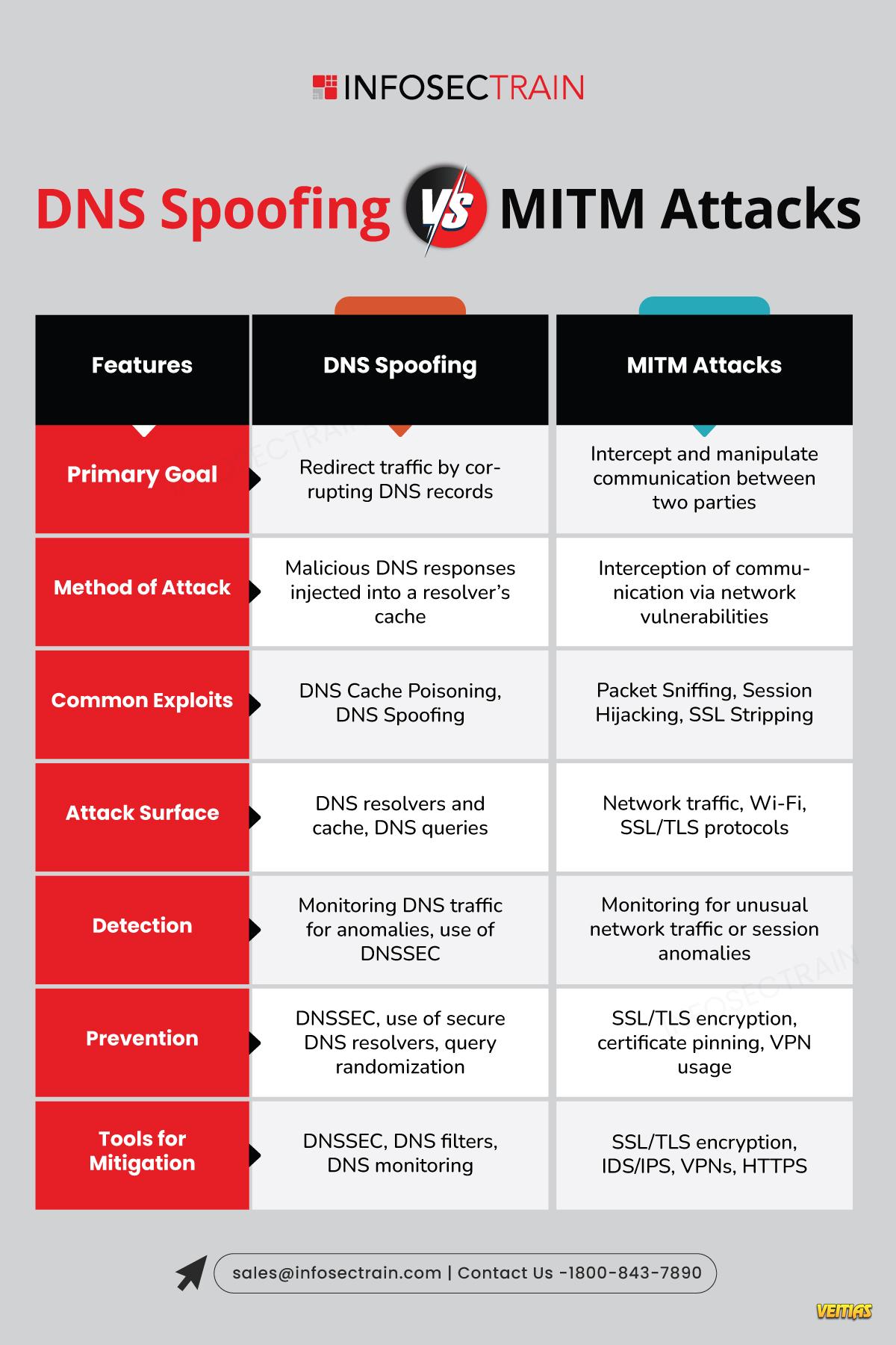
10 Common DNS Attacks for SOC
InfosecTrain’s latest infographic dives into the most common DNS-based attacks that Security Operations Center (SOC) teams must watch out for. It’s a quick, visual guide to understanding how DNS vulnerabilities are exploited and why proactive monitoring is essential in modern cybersecurity defense.
DNS Protocols and Attacks - https://www.infosectrain.com/blog/dns-protocols-and-attacks/
#DNSAttacks #SOCAnalyst #Cybersecurity #BlueTeamOps #ThreatDetection #InfoSec #NetworkSecurity #SOCMonitoring #CyberThreats #DNSDefense #SecurityOps #MalwareAnalysis #infosectrain #learntorise
InfosecTrain’s latest infographic dives into the most common DNS-based attacks that Security Operations Center (SOC) teams must watch out for. It’s a quick, visual guide to understanding how DNS vulnerabilities are exploited and why proactive monitoring is essential in modern cybersecurity defense.
DNS Protocols and Attacks - https://www.infosectrain.com/blog/dns-protocols-and-attacks/
#DNSAttacks #SOCAnalyst #Cybersecurity #BlueTeamOps #ThreatDetection #InfoSec #NetworkSecurity #SOCMonitoring #CyberThreats #DNSDefense #SecurityOps #MalwareAnalysis #infosectrain #learntorise
10 Common DNS Attacks for SOC
InfosecTrain’s latest infographic dives into the most common DNS-based attacks that Security Operations Center (SOC) teams must watch out for. It’s a quick, visual guide to understanding how DNS vulnerabilities are exploited and why proactive monitoring is essential in modern cybersecurity defense.
DNS Protocols and Attacks - https://www.infosectrain.com/blog/dns-protocols-and-attacks/
#DNSAttacks #SOCAnalyst #Cybersecurity #BlueTeamOps #ThreatDetection #InfoSec #NetworkSecurity #SOCMonitoring #CyberThreats #DNSDefense #SecurityOps #MalwareAnalysis #infosectrain #learntorise
0 Σχόλια
0 Μοιράστηκε
6509 Views
0 Προεπισκόπηση