Key Components of Identity and Access Management (IAM) in Cloud Security
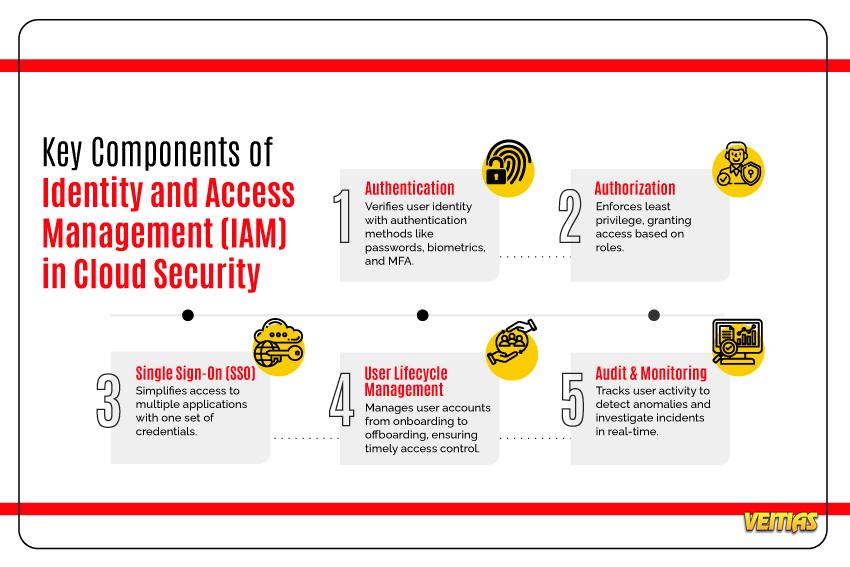
In today’s cloud-first world, protecting access to sensitive data is more crucial than ever. Here's a breakdown of the key IAM components that safeguard your cloud environment:
By strengthening your IAM practices, you can ensure secure, efficient, and seamless access to your cloud resources.
Components of IAM - https://www.infosectrain.com/blog/identity-and-access-management-iam-in-cloud-security/
#CloudSecurity #IAM #CyberSecurity #MFA #SSO #Authorization # AuditAndMonitoring #ZeroTrust #CloudComputing #infosectrain #learntorise
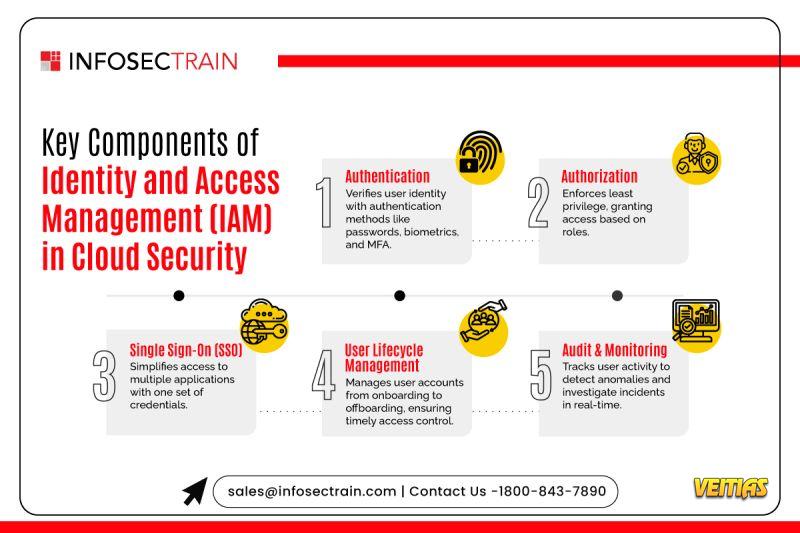
In today’s cloud-first world, protecting access to sensitive data is more crucial than ever. Here's a breakdown of the key IAM components that safeguard your cloud environment:
By strengthening your IAM practices, you can ensure secure, efficient, and seamless access to your cloud resources.
Components of IAM - https://www.infosectrain.com/blog/identity-and-access-management-iam-in-cloud-security/
#CloudSecurity #IAM #CyberSecurity #MFA #SSO #Authorization # AuditAndMonitoring #ZeroTrust #CloudComputing #infosectrain #learntorise
Key Components of Identity and Access Management (IAM) in Cloud Security
In today’s cloud-first world, protecting access to sensitive data is more crucial than ever. Here's a breakdown of the key IAM components that safeguard your cloud environment:
By strengthening your IAM practices, you can ensure secure, efficient, and seamless access to your cloud resources.
Components of IAM - https://www.infosectrain.com/blog/identity-and-access-management-iam-in-cloud-security/
#CloudSecurity #IAM #CyberSecurity #MFA #SSO #Authorization # AuditAndMonitoring #ZeroTrust #CloudComputing #infosectrain #learntorise
0 Commenti
0 condivisioni
3096 Views
0 Anteprima