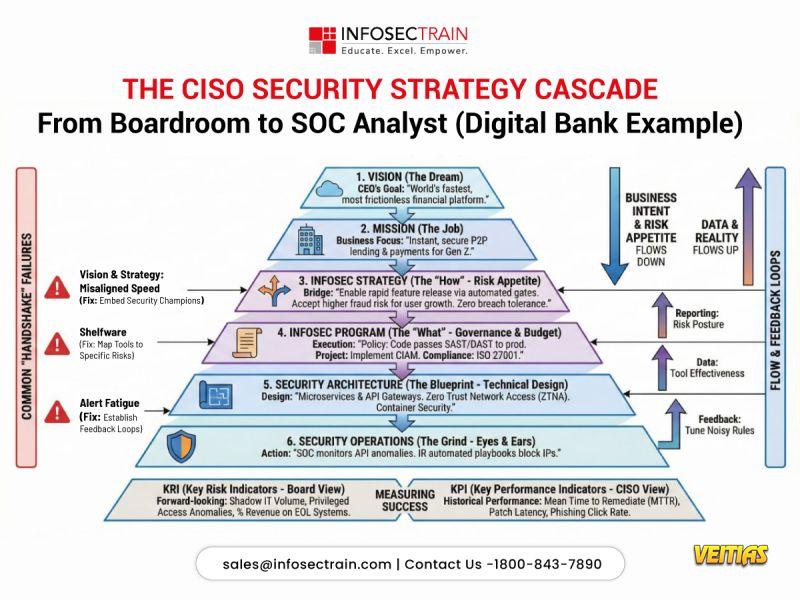
Political Campaign Management Company: Behind the Scenes of Winning Elections
A political campaign management company operates like a theatre production where the candidate is the lead actor, but an entire crew works tirelessly backstage to make the performance flawless. From the moment a candidate decides to run until victory is declared, professional campaign managers, data analysts, field coordinators, and creative teams work around the clock. Let's pull back the curtain and explore what actually happens behind the scenes of winning elections in India.
For more information, visit us at: https://writeupcafe.com/political-campaign-management-company-behind-the-scenes-of-winning-elections
A political campaign management company operates like a theatre production where the candidate is the lead actor, but an entire crew works tirelessly backstage to make the performance flawless. From the moment a candidate decides to run until victory is declared, professional campaign managers, data analysts, field coordinators, and creative teams work around the clock. Let's pull back the curtain and explore what actually happens behind the scenes of winning elections in India.
For more information, visit us at: https://writeupcafe.com/political-campaign-management-company-behind-the-scenes-of-winning-elections
Political Campaign Management Company: Behind the Scenes of Winning Elections
A political campaign management company operates like a theatre production where the candidate is the lead actor, but an entire crew works tirelessly backstage to make the performance flawless. From the moment a candidate decides to run until victory is declared, professional campaign managers, data analysts, field coordinators, and creative teams work around the clock. Let's pull back the curtain and explore what actually happens behind the scenes of winning elections in India.
For more information, visit us at: https://writeupcafe.com/political-campaign-management-company-behind-the-scenes-of-winning-elections