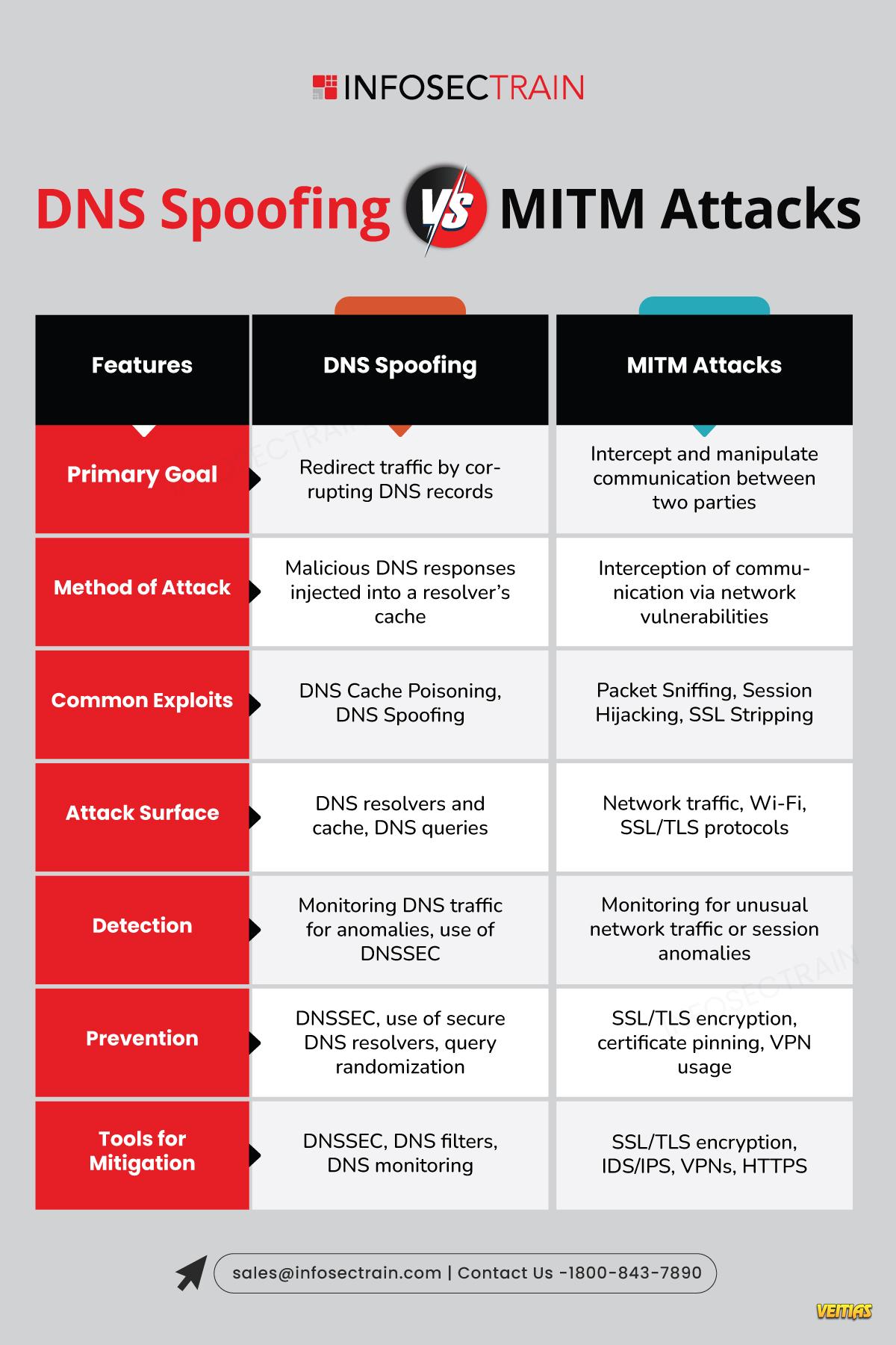
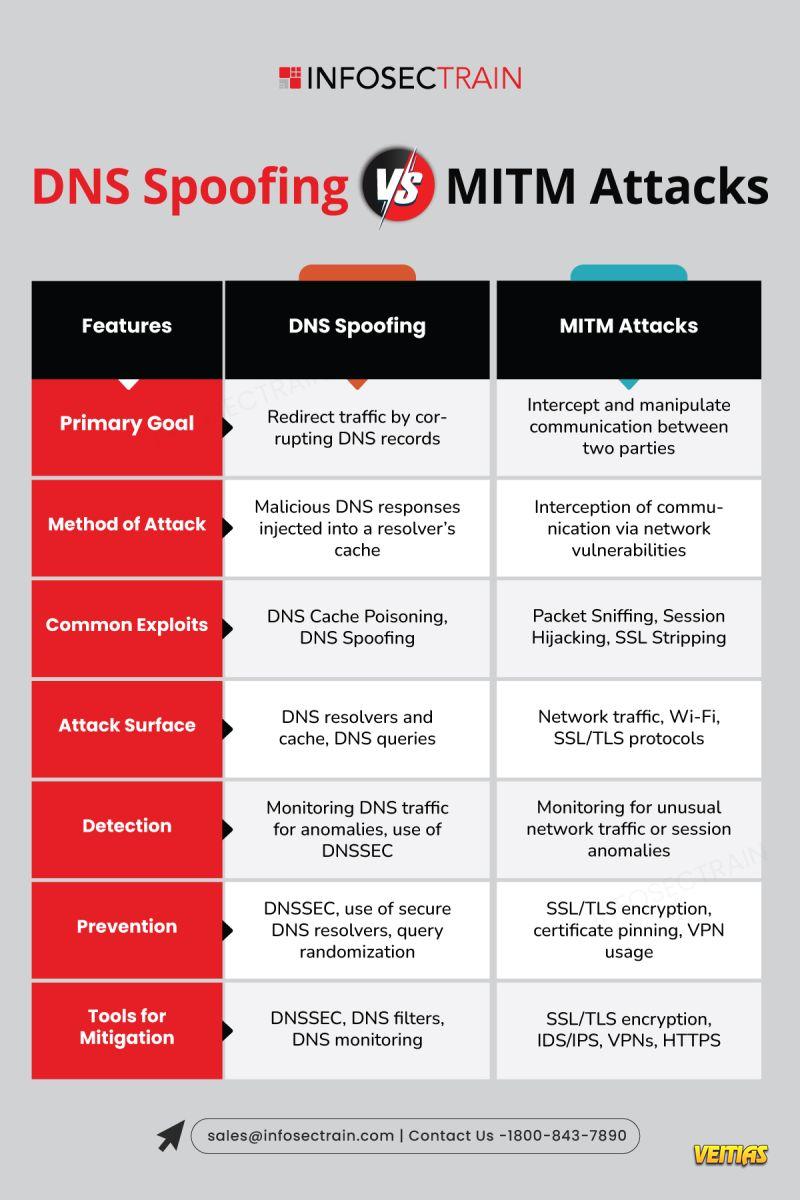
DNS Spoofing vs. MITM Attack
Cybercriminals don’t break in through doors, they sneak in through your internet connection.
Whatever you do online on a daily basis - visiting a website, buying something online or linking to a Wi-Fi network - each may seem harmless, but this is just one way to open serious risks. What you may not realize is you may be giving away sensitive data to a hacker.
This is the key idea of DNS Spoofing & Man-in-the-Middle (MITM) attacks; they are cyber tricks that redirect your traffic or intercept your communication without your knowledge.
Read the detailed breakdown here: https://www.infosectrain.com/blog/dns-spoofing-vs-mitm-attack/
Through awareness of always checking for HTTPS connections, having strong authentication and implementing security measures like encryption and DNSSEC, both individuals and organizations are able to greatly reduce their risk of becoming victim to these attacks.
#CyberSecurity #DNSSpoofing #MITM #DataProtection #InfoSec #CyberAwareness #Encryption #OnlineSafety
Cybercriminals don’t break in through doors, they sneak in through your internet connection.
Whatever you do online on a daily basis - visiting a website, buying something online or linking to a Wi-Fi network - each may seem harmless, but this is just one way to open serious risks. What you may not realize is you may be giving away sensitive data to a hacker.
This is the key idea of DNS Spoofing & Man-in-the-Middle (MITM) attacks; they are cyber tricks that redirect your traffic or intercept your communication without your knowledge.
Read the detailed breakdown here: https://www.infosectrain.com/blog/dns-spoofing-vs-mitm-attack/
Through awareness of always checking for HTTPS connections, having strong authentication and implementing security measures like encryption and DNSSEC, both individuals and organizations are able to greatly reduce their risk of becoming victim to these attacks.
#CyberSecurity #DNSSpoofing #MITM #DataProtection #InfoSec #CyberAwareness #Encryption #OnlineSafety
DNS Spoofing vs. MITM Attack
Cybercriminals don’t break in through doors, they sneak in through your internet connection.
👉 Whatever you do online on a daily basis - visiting a website, buying something online or linking to a Wi-Fi network - each may seem harmless, but this is just one way to open serious risks. What you may not realize is you may be giving away sensitive data to a hacker.
👉 This is the key idea of DNS Spoofing & Man-in-the-Middle (MITM) attacks; they are cyber tricks that redirect your traffic or intercept your communication without your knowledge.
🔗 Read the detailed breakdown here: https://www.infosectrain.com/blog/dns-spoofing-vs-mitm-attack/
✅ Through awareness of always checking for HTTPS connections, having strong authentication and implementing security measures like encryption and DNSSEC, both individuals and organizations are able to greatly reduce their risk of becoming victim to these attacks.
#CyberSecurity #DNSSpoofing #MITM #DataProtection #InfoSec #CyberAwareness #Encryption #OnlineSafety
0 Comentários
0 Compartilhamentos
2635 Visualizações
0 Anterior