What is Endpoint Detection and Response?
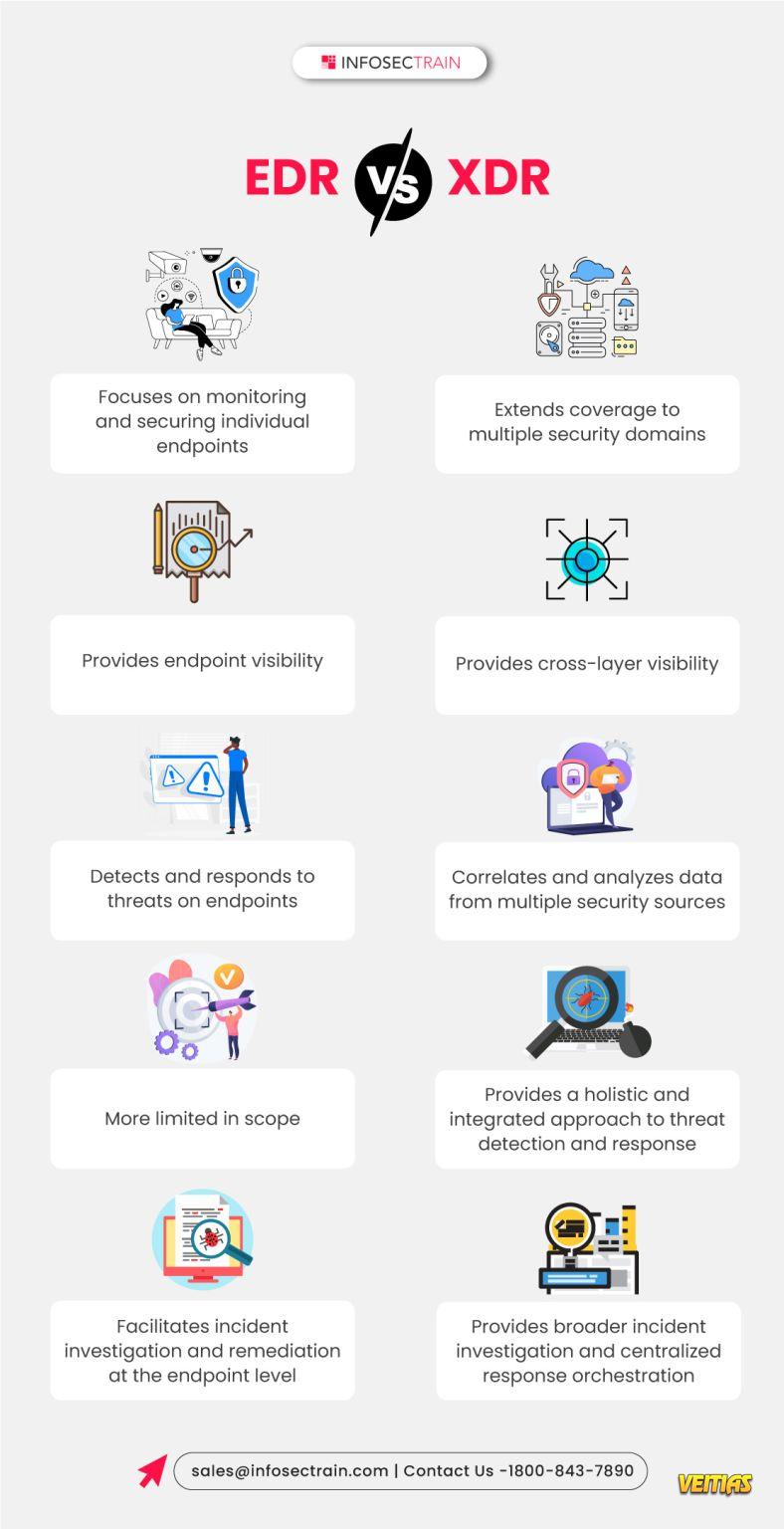
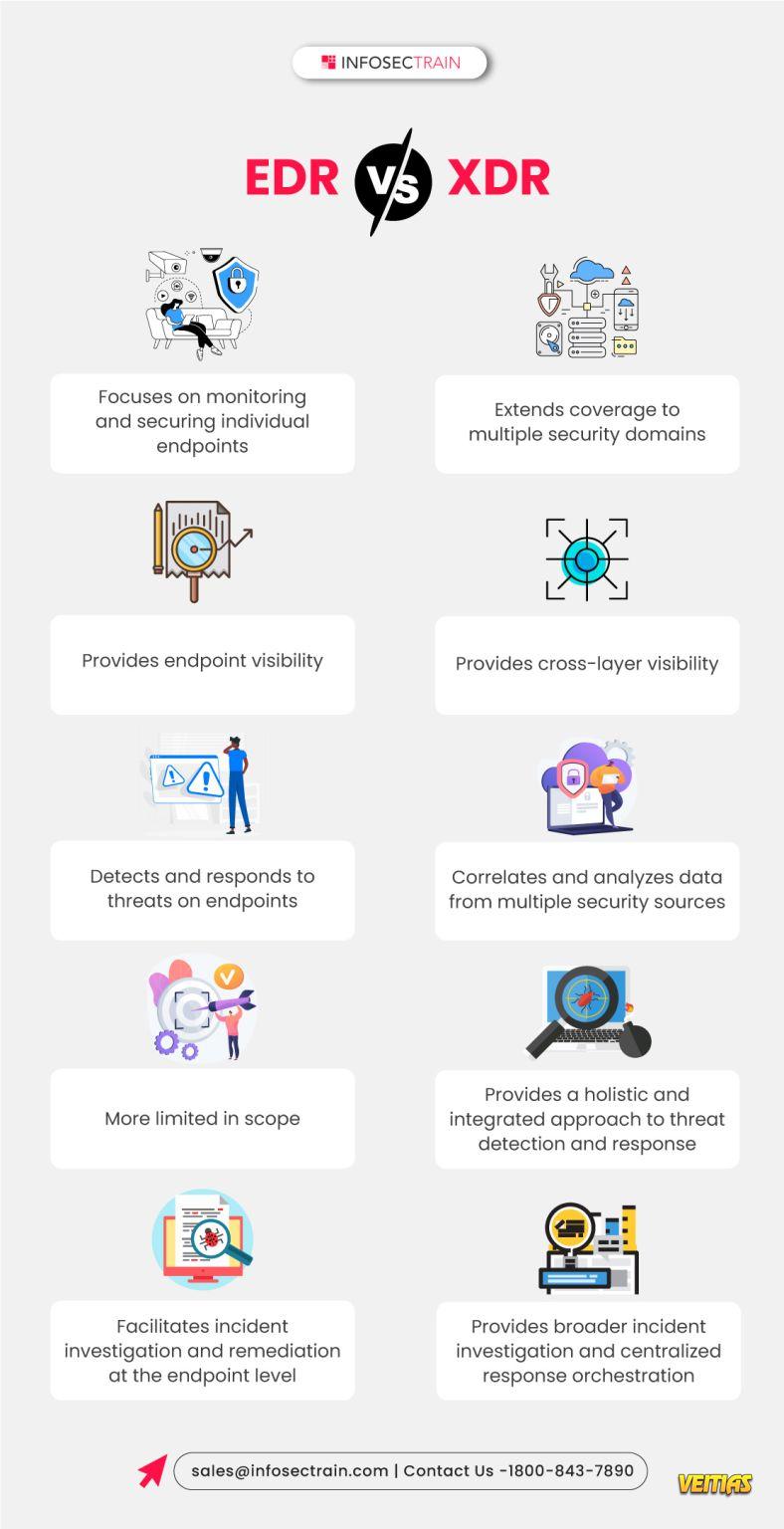
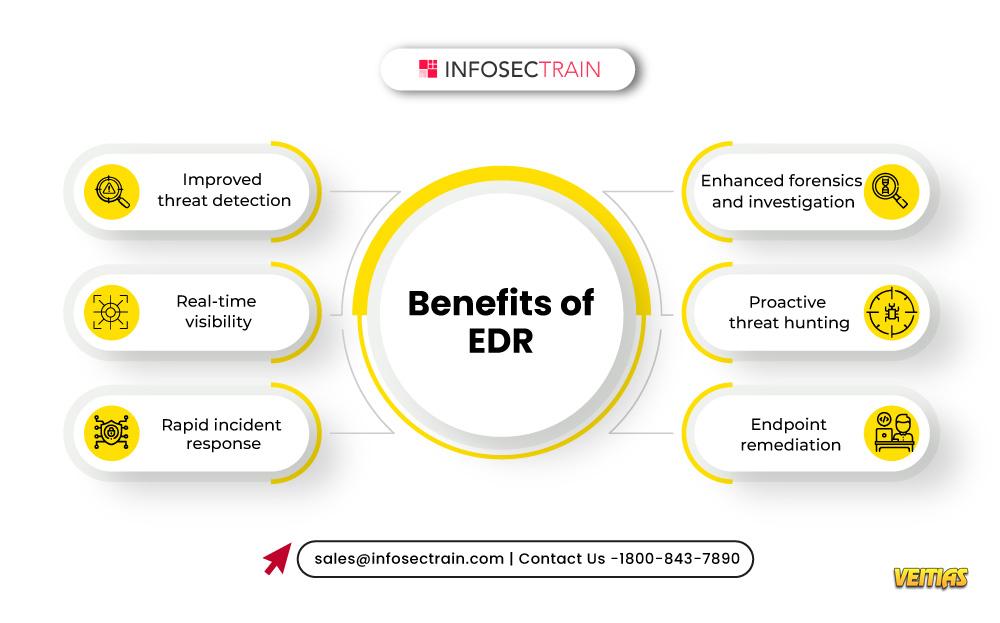
In today's fast-paced digital world, securing your devices from cyber threats is more important than ever. This is where Endpoint Detection and Response (EDR) comes in—think of it as a personal security guard for every device in your organization, from laptops to servers and smartphones.
Unlike traditional antivirus software that primarily looks for known threats, EDR is a more advanced solution that works 24/7 to monitor, detect, and respond to anything that looks suspicious.
Read Here: https://medium.com/@Infosec-Train/what-is-endpoint-detection-and-response-5da698c70c32
#EDR #Cybersecurity #EndpointSecurity #ThreatDetection #InfoSec #CyberDefense #RealTimeSecurity
In today's fast-paced digital world, securing your devices from cyber threats is more important than ever. This is where Endpoint Detection and Response (EDR) comes in—think of it as a personal security guard for every device in your organization, from laptops to servers and smartphones.
Unlike traditional antivirus software that primarily looks for known threats, EDR is a more advanced solution that works 24/7 to monitor, detect, and respond to anything that looks suspicious.
Read Here: https://medium.com/@Infosec-Train/what-is-endpoint-detection-and-response-5da698c70c32
#EDR #Cybersecurity #EndpointSecurity #ThreatDetection #InfoSec #CyberDefense #RealTimeSecurity
What is Endpoint Detection and Response?
In today's fast-paced digital world, securing your devices from cyber threats is more important than ever. This is where Endpoint Detection and Response (EDR) comes in—think of it as a personal security guard for every device in your organization, from laptops to servers and smartphones.
Unlike traditional antivirus software that primarily looks for known threats, EDR is a more advanced solution that works 24/7 to monitor, detect, and respond to anything that looks suspicious.
Read Here: https://medium.com/@Infosec-Train/what-is-endpoint-detection-and-response-5da698c70c32
#EDR #Cybersecurity #EndpointSecurity #ThreatDetection #InfoSec #CyberDefense #RealTimeSecurity
0 Commentarii
0 Distribuiri
3600 Views
0 previzualizare