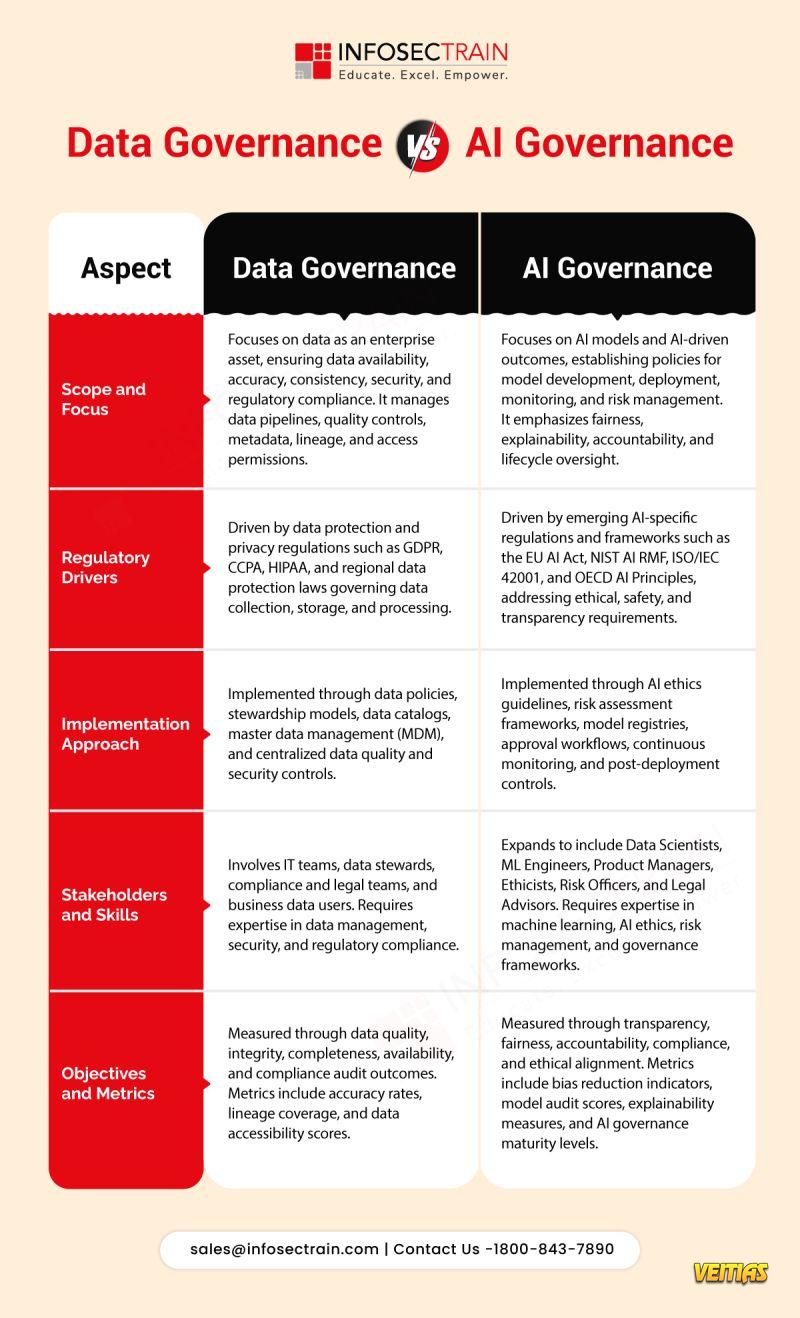
𝗔𝘀 𝗼𝗿𝗴𝗮𝗻𝗶𝘇𝗮𝘁𝗶𝗼𝗻𝘀 𝘀𝗰𝗮𝗹𝗲 𝗔𝗜 𝗮𝗱𝗼𝗽𝘁𝗶𝗼𝗻, 𝗴𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 𝗶𝘀 𝗻𝗼 𝗹𝗼𝗻𝗴𝗲𝗿 𝗹𝗶𝗺𝗶𝘁𝗲𝗱 𝘁𝗼 𝗱𝗮𝘁𝗮 𝗮𝗹𝗼𝗻𝗲. Understanding the difference between 𝗗𝗮𝘁𝗮 𝗚𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 𝗮𝗻𝗱 𝗔𝗜 𝗚𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 is becoming essential for 𝗿𝗶𝘀𝗸 𝗺𝗮𝗻𝗮𝗴𝗲𝗺𝗲𝗻𝘁, 𝗰𝗼𝗺𝗽𝗹𝗶𝗮𝗻𝗰𝗲, 𝗮𝗻𝗱 𝗿𝗲𝘀𝗽𝗼𝗻𝘀𝗶𝗯𝗹𝗲 𝗶𝗻𝗻𝗼𝘃𝗮𝘁𝗶𝗼𝗻.
𝗗𝗮𝘁𝗮 𝗚𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 𝗳𝗼𝗰𝘂𝘀𝗲𝘀 𝗼𝗻 𝗺𝗮𝗻𝗮𝗴𝗶𝗻𝗴 𝗱𝗮𝘁𝗮 as an enterprise asset through quality, security, lineage, and regulatory controls.
𝗔𝗜 𝗚𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 𝗴𝗼𝗲𝘀 𝗳𝘂𝗿𝘁𝗵𝗲𝗿 𝗯𝘆 𝗮𝗱𝗱𝗿𝗲𝘀𝘀𝗶𝗻𝗴 𝗺𝗼𝗱𝗲𝗹 𝗿𝗶𝘀𝗸,, ethics, explainability, lifecycle monitoring, and emerging global AI regulations.
𝗗𝗮𝘁𝗮 𝗚𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 𝗳𝗼𝗰𝘂𝘀𝗲𝘀 𝗼𝗻 𝗺𝗮𝗻𝗮𝗴𝗶𝗻𝗴 𝗱𝗮𝘁𝗮 as an enterprise asset through quality, security, lineage, and regulatory controls.
𝗔𝗜 𝗚𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 𝗴𝗼𝗲𝘀 𝗳𝘂𝗿𝘁𝗵𝗲𝗿 𝗯𝘆 𝗮𝗱𝗱𝗿𝗲𝘀𝘀𝗶𝗻𝗴 𝗺𝗼𝗱𝗲𝗹 𝗿𝗶𝘀𝗸,, ethics, explainability, lifecycle monitoring, and emerging global AI regulations.
𝗔𝘀 𝗼𝗿𝗴𝗮𝗻𝗶𝘇𝗮𝘁𝗶𝗼𝗻𝘀 𝘀𝗰𝗮𝗹𝗲 𝗔𝗜 𝗮𝗱𝗼𝗽𝘁𝗶𝗼𝗻, 𝗴𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 𝗶𝘀 𝗻𝗼 𝗹𝗼𝗻𝗴𝗲𝗿 𝗹𝗶𝗺𝗶𝘁𝗲𝗱 𝘁𝗼 𝗱𝗮𝘁𝗮 𝗮𝗹𝗼𝗻𝗲. Understanding the difference between 𝗗𝗮𝘁𝗮 𝗚𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 𝗮𝗻𝗱 𝗔𝗜 𝗚𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 is becoming essential for 𝗿𝗶𝘀𝗸 𝗺𝗮𝗻𝗮𝗴𝗲𝗺𝗲𝗻𝘁, 𝗰𝗼𝗺𝗽𝗹𝗶𝗮𝗻𝗰𝗲, 𝗮𝗻𝗱 𝗿𝗲𝘀𝗽𝗼𝗻𝘀𝗶𝗯𝗹𝗲 𝗶𝗻𝗻𝗼𝘃𝗮𝘁𝗶𝗼𝗻.
𝗗𝗮𝘁𝗮 𝗚𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 𝗳𝗼𝗰𝘂𝘀𝗲𝘀 𝗼𝗻 𝗺𝗮𝗻𝗮𝗴𝗶𝗻𝗴 𝗱𝗮𝘁𝗮 as an enterprise asset through quality, security, lineage, and regulatory controls.
𝗔𝗜 𝗚𝗼𝘃𝗲𝗿𝗻𝗮𝗻𝗰𝗲 𝗴𝗼𝗲𝘀 𝗳𝘂𝗿𝘁𝗵𝗲𝗿 𝗯𝘆 𝗮𝗱𝗱𝗿𝗲𝘀𝘀𝗶𝗻𝗴 𝗺𝗼𝗱𝗲𝗹 𝗿𝗶𝘀𝗸,, ethics, explainability, lifecycle monitoring, and emerging global AI regulations.
0 التعليقات
0 المشاركات
481 مشاهدة
0 معاينة