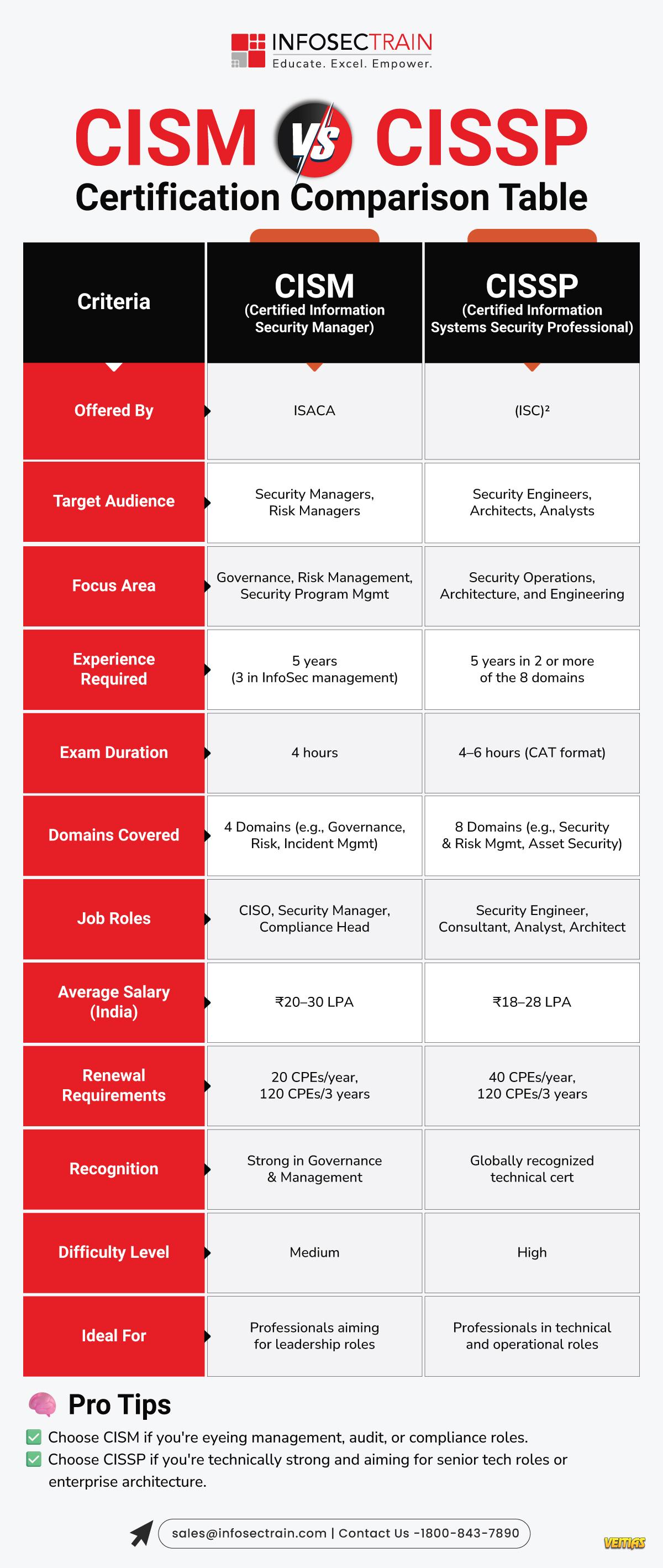
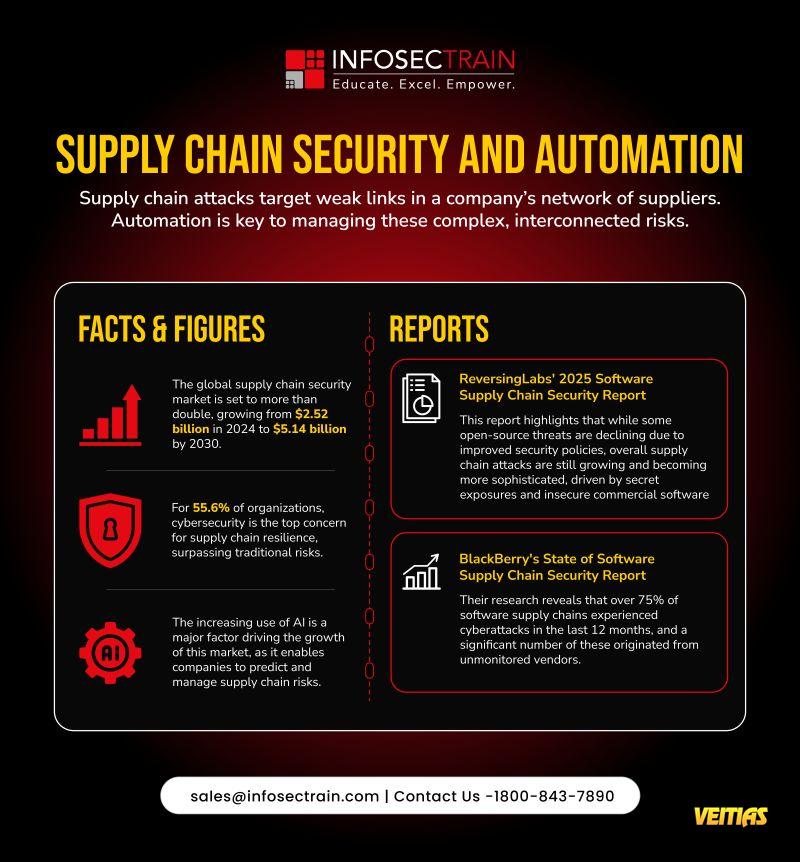
CISM vs CISSP: Certification Comparison Table
This guide highlights differences in focus areas, exam structure, domains, experience requirements, and ideal job roles. Whether you aim to excel in security management (CISM) or master a broad spectrum of security practices (CISSP), this infographic simplifies decision-making. InfosecTrain’s expert-led training programs prepare learners with real-world insights, hands-on practice, and exam-ready resources to boost success. Explore the infographic to choose your perfect cybersecurity path with confidence.
Full Guide For CISM vs CISSP - https://www.infosectrain.com/blog/cism-vs-cissp-where-to-start/
#CISM #CISSP #CyberSecurityCertifications #InfoSec #CyberSecurity #InformationSecurity #ISACA #ISC2 #CyberSecurity Training #ITSecurity #CyberSecurityCareers #CyberSecurityProfessionals #Data Protection #Risk Management #Security Management #Governance #Compliance #CyberAwareness #CyberEducation #InfosecTrain #Upskilling #CyberLearning #TechTraining #learntorise
This guide highlights differences in focus areas, exam structure, domains, experience requirements, and ideal job roles. Whether you aim to excel in security management (CISM) or master a broad spectrum of security practices (CISSP), this infographic simplifies decision-making. InfosecTrain’s expert-led training programs prepare learners with real-world insights, hands-on practice, and exam-ready resources to boost success. Explore the infographic to choose your perfect cybersecurity path with confidence.
Full Guide For CISM vs CISSP - https://www.infosectrain.com/blog/cism-vs-cissp-where-to-start/
#CISM #CISSP #CyberSecurityCertifications #InfoSec #CyberSecurity #InformationSecurity #ISACA #ISC2 #CyberSecurity Training #ITSecurity #CyberSecurityCareers #CyberSecurityProfessionals #Data Protection #Risk Management #Security Management #Governance #Compliance #CyberAwareness #CyberEducation #InfosecTrain #Upskilling #CyberLearning #TechTraining #learntorise
CISM vs CISSP: Certification Comparison Table
This guide highlights differences in focus areas, exam structure, domains, experience requirements, and ideal job roles. Whether you aim to excel in security management (CISM) or master a broad spectrum of security practices (CISSP), this infographic simplifies decision-making. InfosecTrain’s expert-led training programs prepare learners with real-world insights, hands-on practice, and exam-ready resources to boost success. Explore the infographic to choose your perfect cybersecurity path with confidence.
Full Guide For CISM vs CISSP - https://www.infosectrain.com/blog/cism-vs-cissp-where-to-start/
#CISM #CISSP #CyberSecurityCertifications #InfoSec #CyberSecurity #InformationSecurity #ISACA #ISC2 #CyberSecurity Training #ITSecurity #CyberSecurityCareers #CyberSecurityProfessionals #Data Protection #Risk Management #Security Management #Governance #Compliance #CyberAwareness #CyberEducation #InfosecTrain #Upskilling #CyberLearning #TechTraining #learntorise
0 Comments
0 Shares
5068 Views
0 Reviews