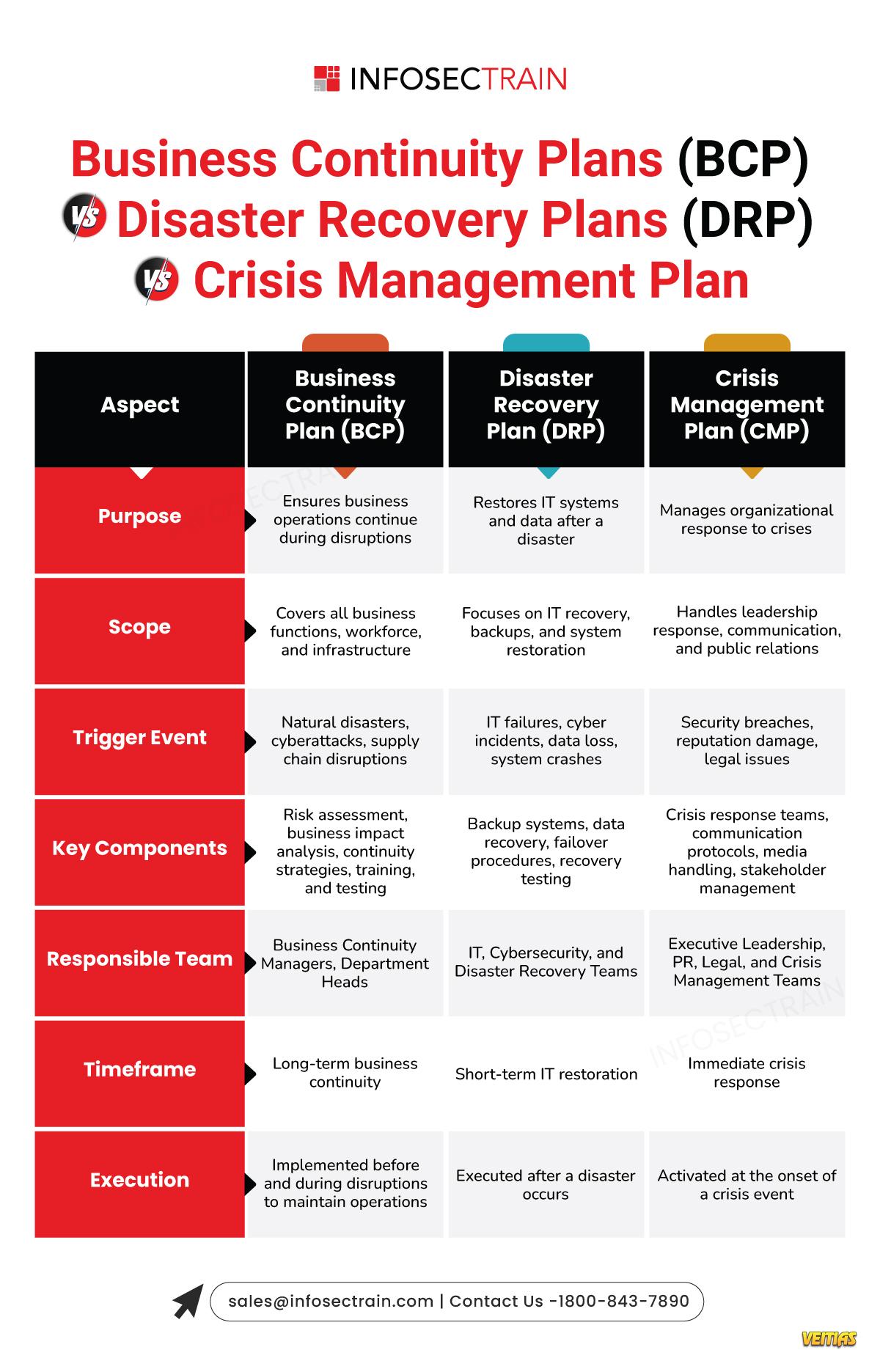
What is ISO 22301 (BCMS) Standard?
ISO 22301 transforms continuity planning into a structured, tested, and trusted system giving your business a real competitive edge.
Read Here: https://www.infosectrain.com/blog/what-is-iso-22301-bcms-standard
#ISO22301 #BusinessContinuity #BCMS #RiskManagement #DisasterRecovery #InfosecTrain #CyberResilience #Compliance #BusinessProtection #OperationalResilience
ISO 22301 transforms continuity planning into a structured, tested, and trusted system giving your business a real competitive edge.
Read Here: https://www.infosectrain.com/blog/what-is-iso-22301-bcms-standard
#ISO22301 #BusinessContinuity #BCMS #RiskManagement #DisasterRecovery #InfosecTrain #CyberResilience #Compliance #BusinessProtection #OperationalResilience
What is ISO 22301 (BCMS) Standard?
ISO 22301 transforms continuity planning into a structured, tested, and trusted system giving your business a real competitive edge.
Read Here: https://www.infosectrain.com/blog/what-is-iso-22301-bcms-standard
#ISO22301 #BusinessContinuity #BCMS #RiskManagement #DisasterRecovery #InfosecTrain #CyberResilience #Compliance #BusinessProtection #OperationalResilience
0 Comments
0 Shares
1959 Views
0 Reviews