Comparing Data Loss Prevention (DLP) and Digital Rights Management (DRM)
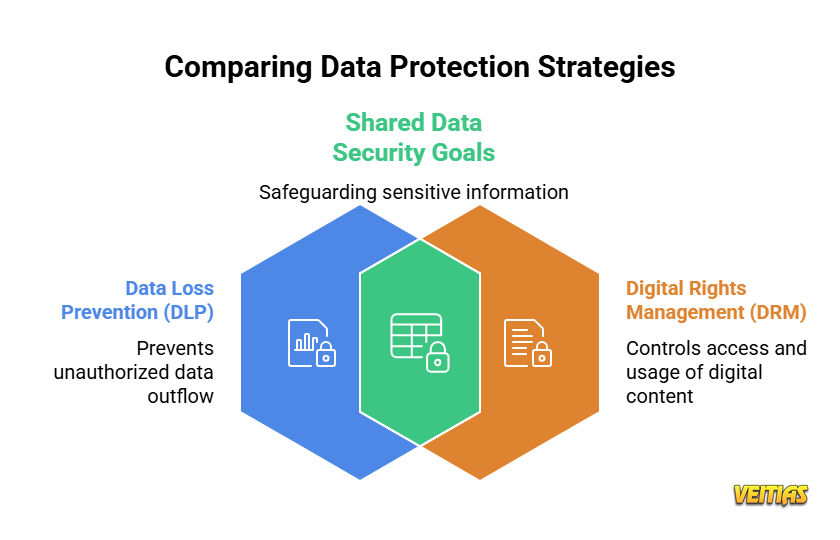
This infographic compares two key data protection strategies; Data Loss Prevention (DLP) and Digital Rights Management (DRM). DLP focuses on preventing unauthorized data outflow, while DRM controls access and usage of digital content. Despite differences, both share the common goal of safeguarding sensitive information and strengthening organizational data security.
#DLP #DRM #DataProtection #CyberSecurity #InfoSec #DataSecurity #AccessControl #Compliance #RiskManagement #Azipirantz
This infographic compares two key data protection strategies; Data Loss Prevention (DLP) and Digital Rights Management (DRM). DLP focuses on preventing unauthorized data outflow, while DRM controls access and usage of digital content. Despite differences, both share the common goal of safeguarding sensitive information and strengthening organizational data security.
#DLP #DRM #DataProtection #CyberSecurity #InfoSec #DataSecurity #AccessControl #Compliance #RiskManagement #Azipirantz
Comparing Data Loss Prevention (DLP) and Digital Rights Management (DRM)
This infographic compares two key data protection strategies; Data Loss Prevention (DLP) and Digital Rights Management (DRM). DLP focuses on preventing unauthorized data outflow, while DRM controls access and usage of digital content. Despite differences, both share the common goal of safeguarding sensitive information and strengthening organizational data security.
#DLP #DRM #DataProtection #CyberSecurity #InfoSec #DataSecurity #AccessControl #Compliance #RiskManagement #Azipirantz
0 Comments
0 Shares
84 Views
0 Reviews