InfoSecTrain provides next-gen Cybersecurity training and certification programs to help professionals and organizations build cyber expertise, enhance skills, and achieve industry-recognized credentials. We deliver tailored, hands-on courses across ethical hacking, penetration testing, ISO compliance, and more empowering learners to stay ahead in an evolving threat landscape.
Recent Updates
- CompTIA Security+ SY0-601 vs SY0-701 Comparison Guide
Are you planning to get certified in cybersecurity? This infographic breaks down the critical differences between the old CompTIA Security+ (SY0-601) and the new (SY0-701) exam domains. Notice the significant increase in Security Operations and Program Management, reflecting the industry's shift toward proactive oversight. Stay ahead of the curve by understanding these updated weightages before you start your prep.
#comptia #securityplus #sy0701 #cybersecurity #infosectrain #certification #itcareerCompTIA Security+ SY0-601 vs SY0-701 Comparison Guide Are you planning to get certified in cybersecurity? This infographic breaks down the critical differences between the old CompTIA Security+ (SY0-601) and the new (SY0-701) exam domains. Notice the significant increase in Security Operations and Program Management, reflecting the industry's shift toward proactive oversight. Stay ahead of the curve by understanding these updated weightages before you start your prep. #comptia #securityplus #sy0701 #cybersecurity #infosectrain #certification #itcareer0 Comments 0 Shares 1374 Views 0 ReviewsPlease log in to like, share and comment! - 0 Comments 0 Shares 692 Views 0 Reviews
- The DevSecOps Pipeline: Securing the Path from Code to Cloud
The modern development lifecycle demands that security is integrated, not added on. By shifting left, organizations can catch hardcoded secrets at the developer's laptop and identify vulnerable libraries during the build phase. This comprehensive pipeline moves through dynamic testing in staging to infrastructure scanning during deployment. Finally, it reaches production with active monitoring and self-protection to ensure a resilient cloud environment. This continuous approach transforms security from a bottleneck into a powerful business enabler.
#DevSecOps #ShiftLeft #CloudSecurity #AppSec #Cybersecurity #InfosecTrain #Infosec
The DevSecOps Pipeline: Securing the Path from Code to Cloud The modern development lifecycle demands that security is integrated, not added on. By shifting left, organizations can catch hardcoded secrets at the developer's laptop and identify vulnerable libraries during the build phase. This comprehensive pipeline moves through dynamic testing in staging to infrastructure scanning during deployment. Finally, it reaches production with active monitoring and self-protection to ensure a resilient cloud environment. This continuous approach transforms security from a bottleneck into a powerful business enabler. #DevSecOps #ShiftLeft #CloudSecurity #AppSec #Cybersecurity #InfosecTrain #Infosec0 Comments 0 Shares 383 Views 0 Reviews - Wazuh vs. Splunk: A Practical Comparison of SIEM Platforms
This visual comparison breaks down the key differences between Wazuh and Splunk to help security teams choose the right SIEM solution. It highlights core aspects such as platform type, licensing cost, search language, ease of setup, compliance support, and enterprise readiness. Wazuh stands out as an open-source SIEM and XDR option with strong community-driven capabilities, while Splunk is positioned as a powerful enterprise-grade data and security analytics platform with advanced features and commercial support. This guide is ideal for SOC teams, security architects, and decision-makers evaluating SIEM tools based on budget, scalability, and operational needs.
#SIEM #XDR #Wazuh #Splunk #CyberSecurity #SOC #ThreatDetection #LogManagement #SecurityAnalytics #Infosectrain
Wazuh vs. Splunk: A Practical Comparison of SIEM Platforms This visual comparison breaks down the key differences between Wazuh and Splunk to help security teams choose the right SIEM solution. It highlights core aspects such as platform type, licensing cost, search language, ease of setup, compliance support, and enterprise readiness. Wazuh stands out as an open-source SIEM and XDR option with strong community-driven capabilities, while Splunk is positioned as a powerful enterprise-grade data and security analytics platform with advanced features and commercial support. This guide is ideal for SOC teams, security architects, and decision-makers evaluating SIEM tools based on budget, scalability, and operational needs. #SIEM #XDR #Wazuh #Splunk #CyberSecurity #SOC #ThreatDetection #LogManagement #SecurityAnalytics #Infosectrain0 Comments 0 Shares 538 Views 0 Reviews - Types of Firewalls Explained: A Practical Security Overview
Firewalls are a foundational component of network security, designed to monitor and control incoming and outgoing traffic based on predefined rules. This visual overview explains the major types of firewalls, including packet filtering, proxy firewalls, stateful multi-layer inspection, unified threat management, next-generation firewalls, NAT firewalls, and virtual firewalls. Understanding these firewall types helps organizations choose the right security controls to protect networks, applications, and data from evolving cyber threats.
#CyberSecurity #NetworkSecurity #Firewalls #InfoSec #SecurityArchitecture #NGFW #UTM #ITSecurity #CyberDefense #Infosectrain
Types of Firewalls Explained: A Practical Security Overview Firewalls are a foundational component of network security, designed to monitor and control incoming and outgoing traffic based on predefined rules. This visual overview explains the major types of firewalls, including packet filtering, proxy firewalls, stateful multi-layer inspection, unified threat management, next-generation firewalls, NAT firewalls, and virtual firewalls. Understanding these firewall types helps organizations choose the right security controls to protect networks, applications, and data from evolving cyber threats. #CyberSecurity #NetworkSecurity #Firewalls #InfoSec #SecurityArchitecture #NGFW #UTM #ITSecurity #CyberDefense #Infosectrain0 Comments 0 Shares 174 Views 0 Reviews - Types of Firewalls Explained: A Practical Security Overview
Firewalls play a critical role in protecting networks by monitoring and controlling incoming and outgoing traffic based on predefined security rules. This visual overview explains the major types of firewalls, including packet filtering, proxy firewalls, stateful inspection, unified threat management (UTM), next-generation firewalls (NGFW), NAT firewalls, and virtual firewalls. Understanding these firewall types helps organizations choose the right security controls to defend against modern cyber threats across on-premises, cloud, and hybrid environments.
#FirewallSecurity #NetworkSecurity #CyberSecurity #NGFW #UTMFirewall #PacketFiltering #ProxyFirewall #StatefulInspection #CloudSecurity #InfoSecTypes of Firewalls Explained: A Practical Security Overview Firewalls play a critical role in protecting networks by monitoring and controlling incoming and outgoing traffic based on predefined security rules. This visual overview explains the major types of firewalls, including packet filtering, proxy firewalls, stateful inspection, unified threat management (UTM), next-generation firewalls (NGFW), NAT firewalls, and virtual firewalls. Understanding these firewall types helps organizations choose the right security controls to defend against modern cyber threats across on-premises, cloud, and hybrid environments. #FirewallSecurity #NetworkSecurity #CyberSecurity #NGFW #UTMFirewall #PacketFiltering #ProxyFirewall #StatefulInspection #CloudSecurity #InfoSec0 Comments 0 Shares 94 Views 0 Reviews - Differences between active attack and passive attack
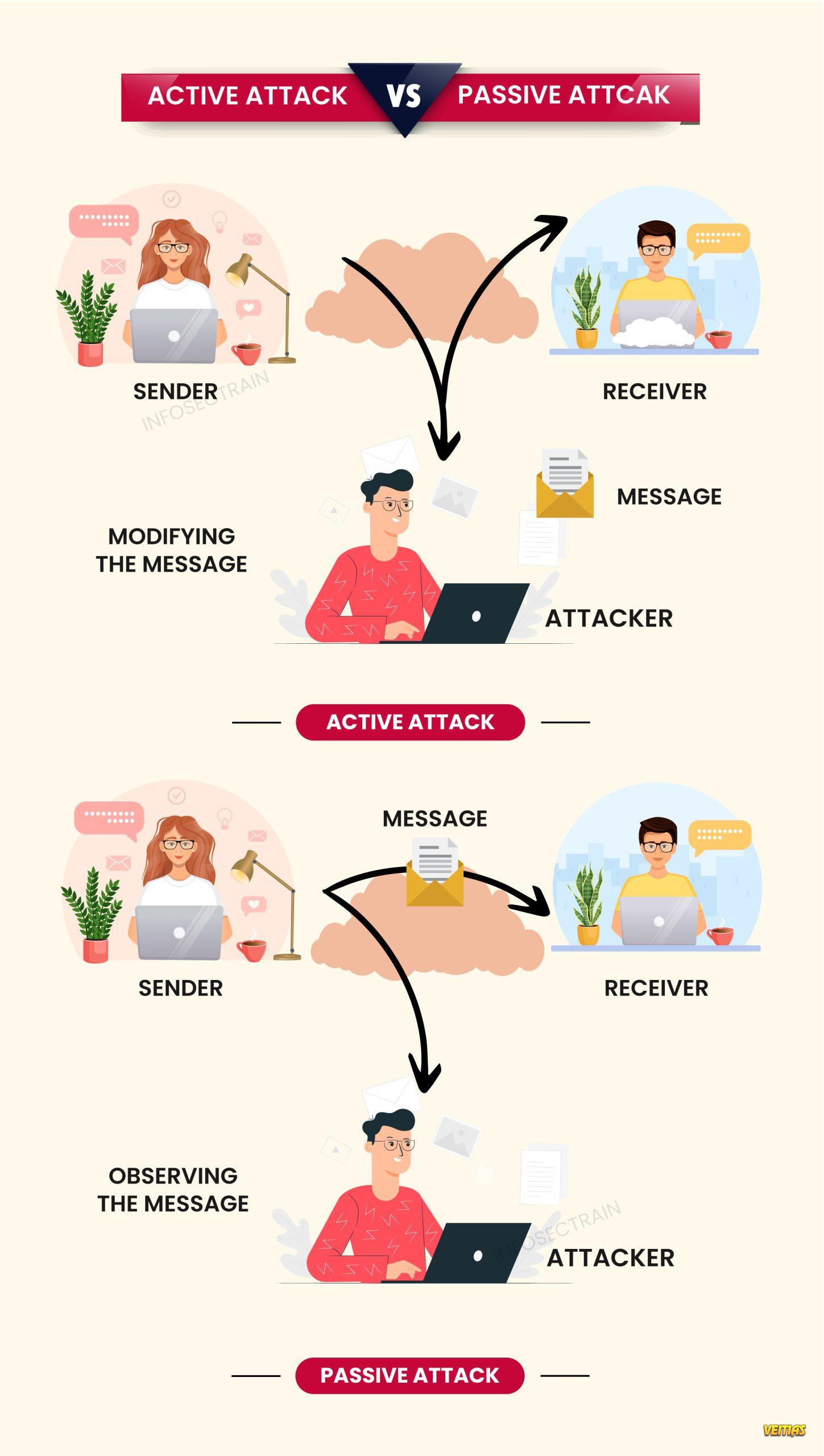
Active and passive attacks represent two fundamental threat categories in cybersecurity. An active attack involves modifying, disrupting, or destroying data and systems, such as malware injection, denial-of-service attacks, or message tampering. In contrast, a passive attack focuses on silently monitoring or intercepting information without altering it, commonly through eavesdropping or traffic analysis. Understanding the differences between these attacks helps security professionals design stronger detection, prevention, and response strategies to protect sensitive data and ensure system integrity.
#CyberSecurity #ActiveAttack #PassiveAttack #NetworkSecurity #InfoSec #CyberThreats #SecurityAwareness #EthicalHacking #DataProtection #CyberRiskDifferences between active attack and passive attack Active and passive attacks represent two fundamental threat categories in cybersecurity. An active attack involves modifying, disrupting, or destroying data and systems, such as malware injection, denial-of-service attacks, or message tampering. In contrast, a passive attack focuses on silently monitoring or intercepting information without altering it, commonly through eavesdropping or traffic analysis. Understanding the differences between these attacks helps security professionals design stronger detection, prevention, and response strategies to protect sensitive data and ensure system integrity. #CyberSecurity #ActiveAttack #PassiveAttack #NetworkSecurity #InfoSec #CyberThreats #SecurityAwareness #EthicalHacking #DataProtection #CyberRisk0 Comments 0 Shares 217 Views 0 Reviews - Cloud Computing vs Edge Computing: Key Differences Explained
This infographic explains the fundamental differences between Cloud Computing and Edge Computing. It highlights where computation takes place, how data is processed, and why edge computing is critical for low-latency, real-time applications, while cloud computing remains ideal for centralized processing, scalability, and large-scale data analytics.
#CloudComputing #EdgeComputing #CloudVsEdge #DistributedSystems #IoTArchitecture #LowLatency #DigitalTransformation #ITInfrastructure #NetworkComputing #TechExplainedCloud Computing vs Edge Computing: Key Differences Explained This infographic explains the fundamental differences between Cloud Computing and Edge Computing. It highlights where computation takes place, how data is processed, and why edge computing is critical for low-latency, real-time applications, while cloud computing remains ideal for centralized processing, scalability, and large-scale data analytics. #CloudComputing #EdgeComputing #CloudVsEdge #DistributedSystems #IoTArchitecture #LowLatency #DigitalTransformation #ITInfrastructure #NetworkComputing #TechExplained0 Comments 0 Shares 138 Views 0 Reviews - Black Box vs Grey Box vs White Box Penetration Testing Explained
This infographic explains the three main types of penetration testing: Black Box, Grey Box, and White Box testing. It highlights how each approach differs based on the tester’s level of knowledge about the system, helping organizations choose the right testing method to identify security vulnerabilities, strengthen defenses, and improve overall cybersecurity posture.
#PenetrationTesting #BlackBoxTesting #GreyBoxTesting #WhiteBoxTesting #CyberSecurity #EthicalHacking #SecurityTesting #VulnerabilityAssessment #AppSecurity #NetworkSecurityBlack Box vs Grey Box vs White Box Penetration Testing Explained This infographic explains the three main types of penetration testing: Black Box, Grey Box, and White Box testing. It highlights how each approach differs based on the tester’s level of knowledge about the system, helping organizations choose the right testing method to identify security vulnerabilities, strengthen defenses, and improve overall cybersecurity posture. #PenetrationTesting #BlackBoxTesting #GreyBoxTesting #WhiteBoxTesting #CyberSecurity #EthicalHacking #SecurityTesting #VulnerabilityAssessment #AppSecurity #NetworkSecurity0 Comments 0 Shares 181 Views 0 Reviews - Cyber Attack vs Data Breach: Understanding the Key Differences
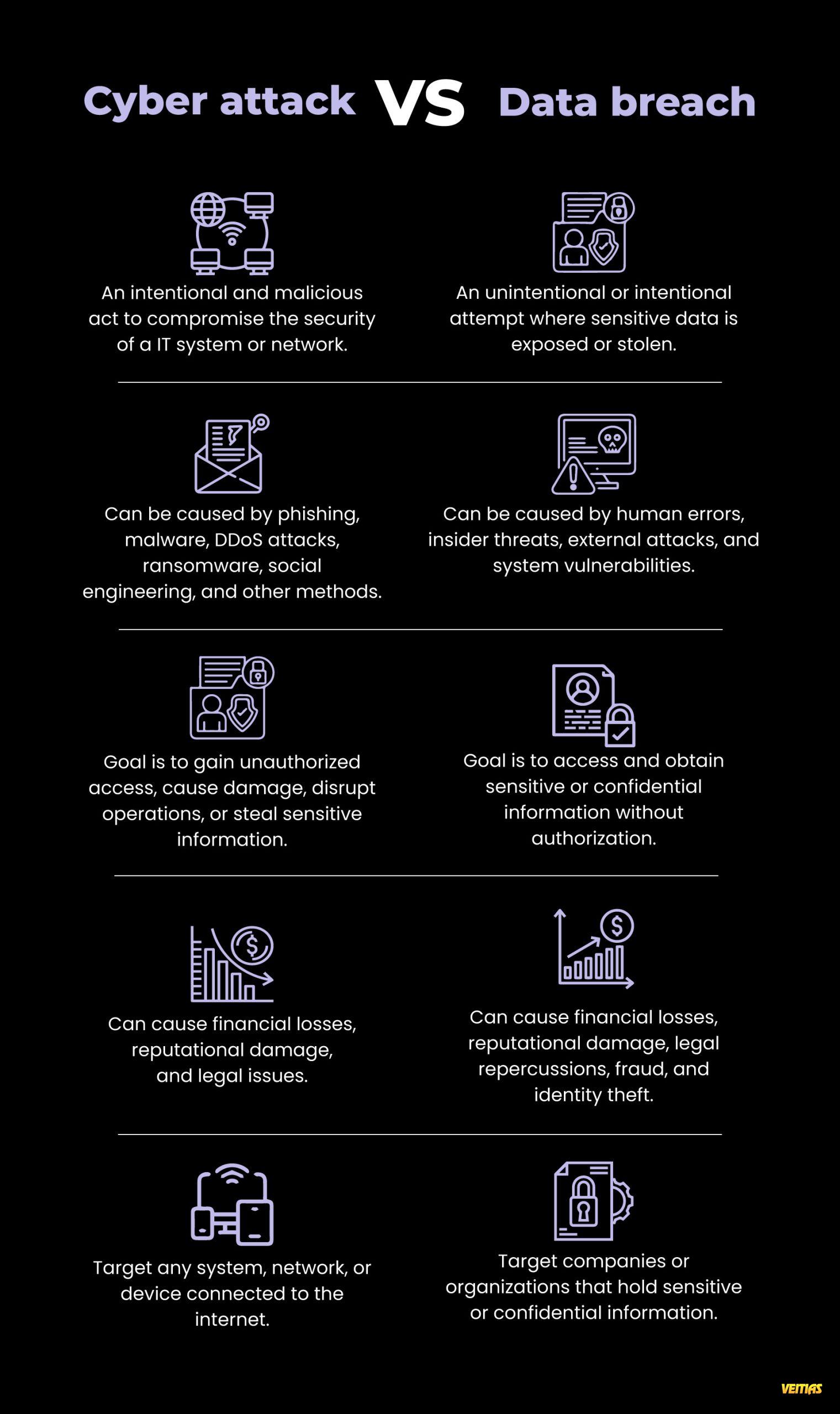
This infographic explains the clear differences between a cyber attack and a data breach by comparing intent, causes, objectives, impact, and targets. A cyber attack is a deliberate and malicious attempt to compromise systems, disrupt operations, or gain unauthorized access, often through phishing, malware, ransomware, or DDoS attacks. A data breach, on the other hand, focuses on the exposure or theft of sensitive data, which can occur due to human error, insider threats, system vulnerabilities, or external attacks. Understanding these distinctions helps organizations strengthen security strategies, improve incident response, and reduce financial, legal, and reputational risks.
#CyberAttack #DataBreach #CyberSecurity #InformationSecurity #RiskManagement #IncidentResponse #DataProtection #NetworkSecurity #Compliance #ThreatAwarenessCyber Attack vs Data Breach: Understanding the Key Differences This infographic explains the clear differences between a cyber attack and a data breach by comparing intent, causes, objectives, impact, and targets. A cyber attack is a deliberate and malicious attempt to compromise systems, disrupt operations, or gain unauthorized access, often through phishing, malware, ransomware, or DDoS attacks. A data breach, on the other hand, focuses on the exposure or theft of sensitive data, which can occur due to human error, insider threats, system vulnerabilities, or external attacks. Understanding these distinctions helps organizations strengthen security strategies, improve incident response, and reduce financial, legal, and reputational risks. #CyberAttack #DataBreach #CyberSecurity #InformationSecurity #RiskManagement #IncidentResponse #DataProtection #NetworkSecurity #Compliance #ThreatAwareness0 Comments 0 Shares 153 Views 0 Reviews
More Stories