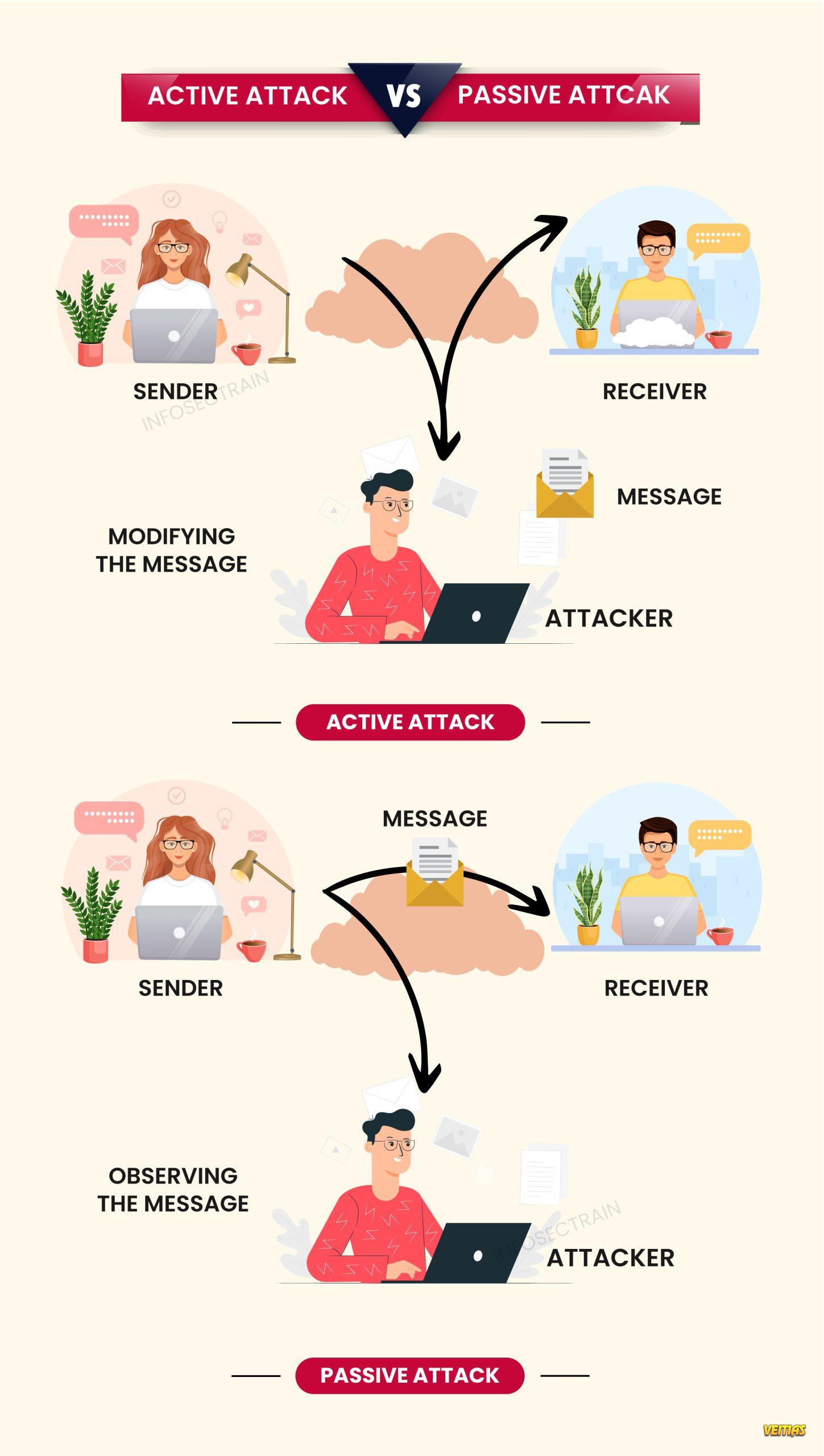
Differences between active attack and passive attack
Active and passive attacks represent two fundamental threat categories in cybersecurity. An active attack involves modifying, disrupting, or destroying data and systems, such as malware injection, denial-of-service attacks, or message tampering. In contrast, a passive attack focuses on silently monitoring or intercepting information without altering it, commonly through eavesdropping or traffic analysis. Understanding the differences between these attacks helps security professionals design stronger detection, prevention, and response strategies to protect sensitive data and ensure system integrity.
#CyberSecurity #ActiveAttack #PassiveAttack #NetworkSecurity #InfoSec #CyberThreats #SecurityAwareness #EthicalHacking #DataProtection #CyberRisk
Active and passive attacks represent two fundamental threat categories in cybersecurity. An active attack involves modifying, disrupting, or destroying data and systems, such as malware injection, denial-of-service attacks, or message tampering. In contrast, a passive attack focuses on silently monitoring or intercepting information without altering it, commonly through eavesdropping or traffic analysis. Understanding the differences between these attacks helps security professionals design stronger detection, prevention, and response strategies to protect sensitive data and ensure system integrity.
#CyberSecurity #ActiveAttack #PassiveAttack #NetworkSecurity #InfoSec #CyberThreats #SecurityAwareness #EthicalHacking #DataProtection #CyberRisk
Differences between active attack and passive attack
Active and passive attacks represent two fundamental threat categories in cybersecurity. An active attack involves modifying, disrupting, or destroying data and systems, such as malware injection, denial-of-service attacks, or message tampering. In contrast, a passive attack focuses on silently monitoring or intercepting information without altering it, commonly through eavesdropping or traffic analysis. Understanding the differences between these attacks helps security professionals design stronger detection, prevention, and response strategies to protect sensitive data and ensure system integrity.
#CyberSecurity #ActiveAttack #PassiveAttack #NetworkSecurity #InfoSec #CyberThreats #SecurityAwareness #EthicalHacking #DataProtection #CyberRisk
0 Comments
0 Shares
223 Views
0 Reviews