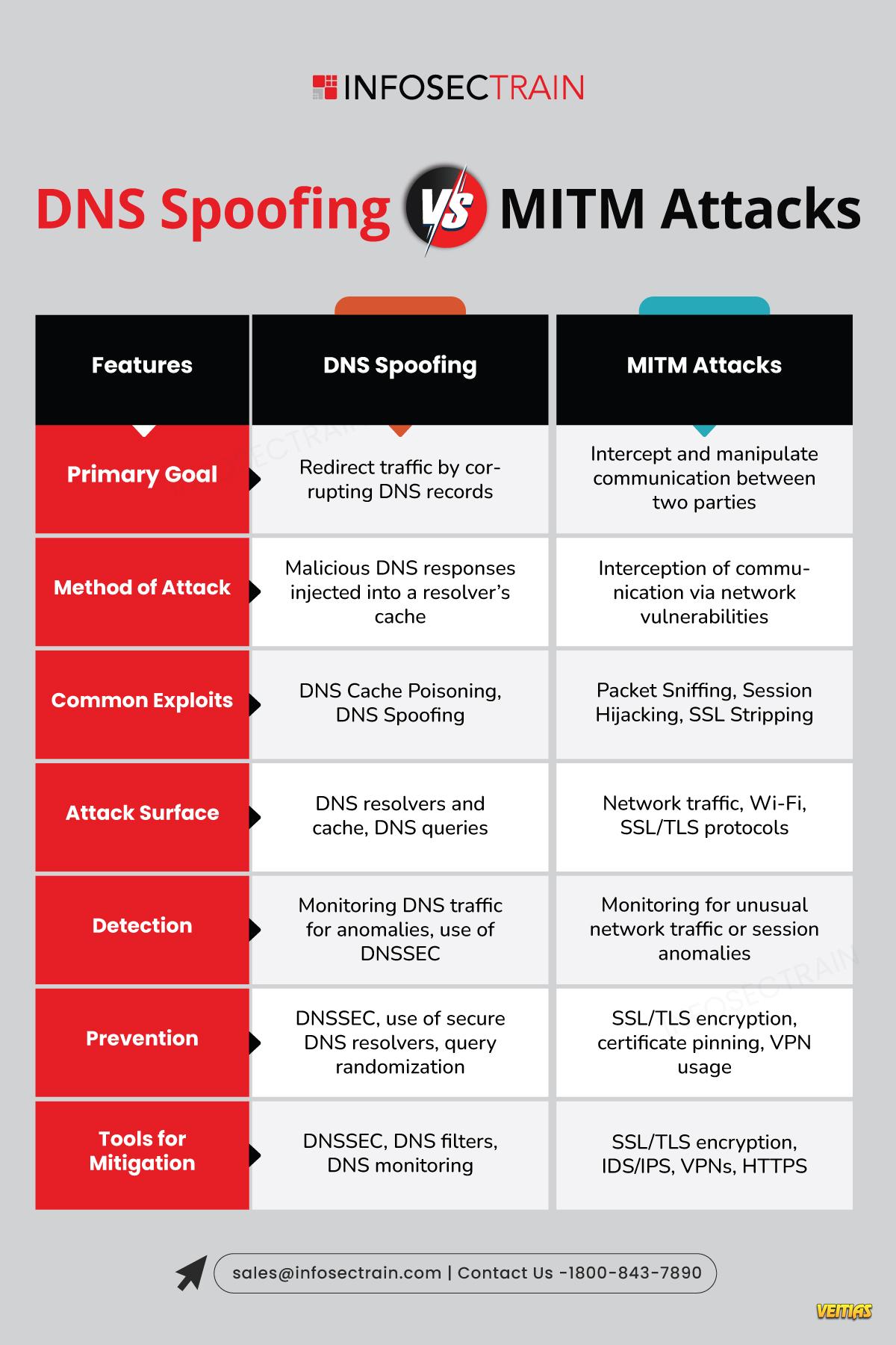
Think Your Internal Network Is Safe? Think Again. LLMNR Might Be Your Silent Weak Spot!
Most teams overlook it… but LLMNR (Link-Local Multicast Name Resolution) is one of the easiest ways attackers steal credentials inside internal networks.
In this video, we break down:
What LLMNR is & why it exists
How attackers abuse it for credential harvesting
Real-world techniques like MitM + spoofing
How SOC teams and defenders can detect & prevent LLMNR attacks
Watch Here: https://youtu.be/tw0Q_oIt0kg?si=Np1tX65Q7gL2daEG
#LLMNR #NetworkSecurity #InfosecTrain #EthicalHacking #ResponderTool #ManInTheMiddleAttack #CredentialHarvesting #CyberSecurityTraining #RedTeam #BlueTeam
Most teams overlook it… but LLMNR (Link-Local Multicast Name Resolution) is one of the easiest ways attackers steal credentials inside internal networks.
In this video, we break down:
What LLMNR is & why it exists
How attackers abuse it for credential harvesting
Real-world techniques like MitM + spoofing
How SOC teams and defenders can detect & prevent LLMNR attacks
Watch Here: https://youtu.be/tw0Q_oIt0kg?si=Np1tX65Q7gL2daEG
#LLMNR #NetworkSecurity #InfosecTrain #EthicalHacking #ResponderTool #ManInTheMiddleAttack #CredentialHarvesting #CyberSecurityTraining #RedTeam #BlueTeam
Think Your Internal Network Is Safe? Think Again. LLMNR Might Be Your Silent Weak Spot!
Most teams overlook it… but LLMNR (Link-Local Multicast Name Resolution) is one of the easiest ways attackers steal credentials inside internal networks.
In this video, we break down:
🔹 What LLMNR is & why it exists
🔹 How attackers abuse it for credential harvesting
🔹 Real-world techniques like MitM + spoofing
🔹 How SOC teams and defenders can detect & prevent LLMNR attacks
Watch Here: https://youtu.be/tw0Q_oIt0kg?si=Np1tX65Q7gL2daEG
#LLMNR #NetworkSecurity #InfosecTrain #EthicalHacking #ResponderTool #ManInTheMiddleAttack #CredentialHarvesting #CyberSecurityTraining #RedTeam #BlueTeam

0 Commentarii
0 Distribuiri
4461 Views
0 previzualizare