Traditional Cybersecurity vs. AI-Powered Cybersecurity
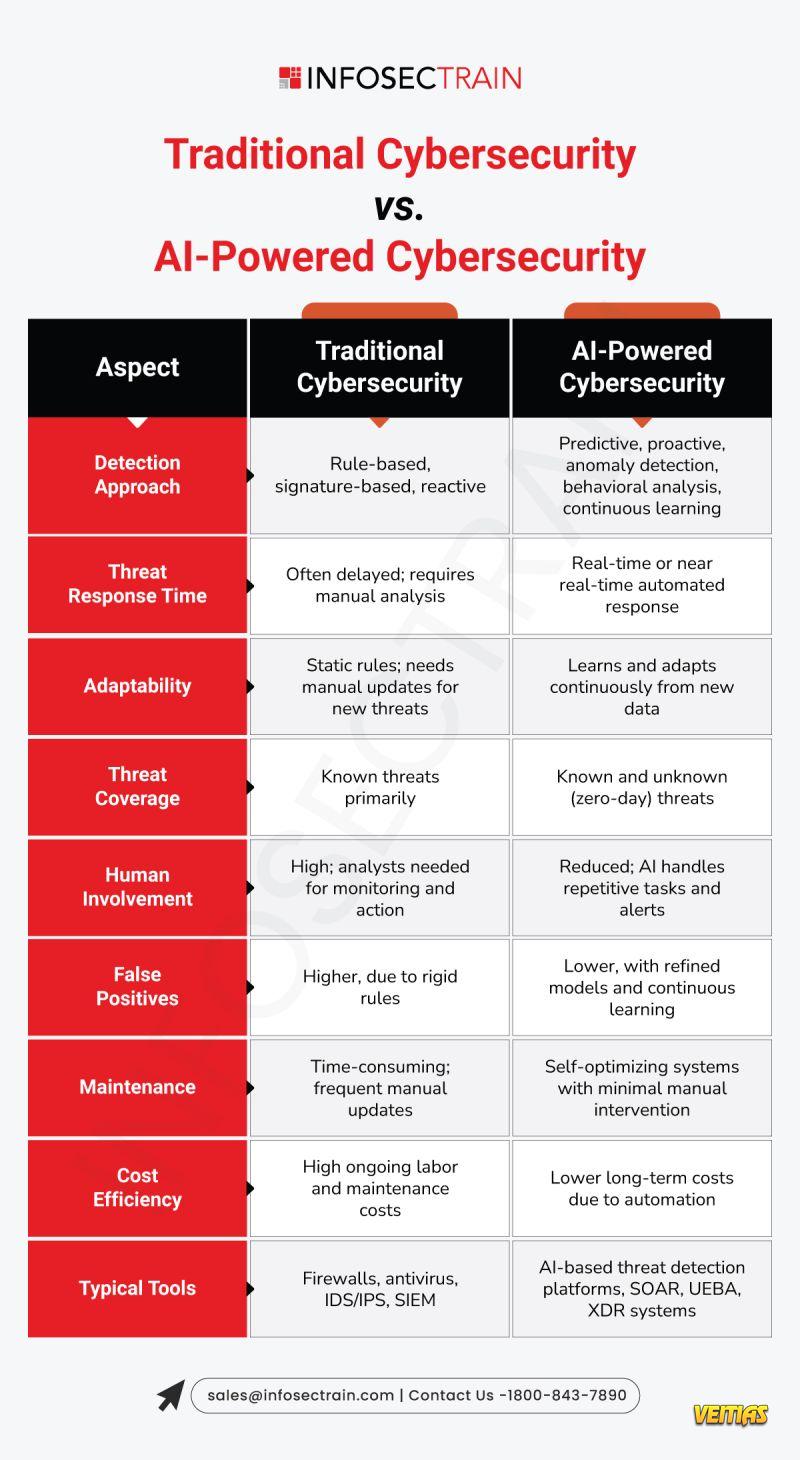
Organizations have been dependent on traditional security tools (firewalls, antivirus software, IDS/IPS) for a long time. Although they are usually doing their jobs to some extent, for the most part they are reactive; that is, they rely on detecting, alerting and responding to attacks AFTER they have already started.
Today’s cyber threats look very different. Attackers are faster, smarter, and using more automation to outsmart detection.
AI-powered cybersecurity will change this paradigm.
Using AI and machine learning, modern security can:
Detect anomalous behavior when it occurs
Anticipate and defend against zero-day exploits
Automate incident response and implement remediation activities automatically, mitigating time to respond.
Join InfosecTrain expert-led session to gain valuable insights and boost your skills. Don't miss this opportunity to learn and grow—register now to secure your spot!:
https://www.infosectrain.com/events/
Traditional cybersecurity is like a guard with a checklist, while AI-powered security is a guard that learns and adapts every second.
#AIinSecurity #CyberDefense #ThreatDetection #InfoSec #MachineLearning #FutureOfCybersecurity #infosectrain
Traditional Cybersecurity vs. AI-Powered Cybersecurity
Organizations have been dependent on traditional security tools (firewalls, antivirus software, IDS/IPS) for a long time. Although they are usually doing their jobs to some extent, for the most part they are reactive; that is, they rely on detecting, alerting and responding to attacks AFTER they have already started.
Today’s cyber threats look very different. Attackers are faster, smarter, and using more automation to outsmart detection.
AI-powered cybersecurity will change this paradigm.
✨ Using AI and machine learning, modern security can:
✅ Detect anomalous behavior when it occurs
✅ Anticipate and defend against zero-day exploits
✅ Automate incident response and implement remediation activities automatically, mitigating time to respond.
Join InfosecTrain expert-led session to gain valuable insights and boost your skills. Don't miss this opportunity to learn and grow—register now to secure your spot!: https://www.infosectrain.com/events/
Traditional cybersecurity is like a guard with a checklist, while AI-powered security is a guard that learns and adapts every second.
#AIinSecurity #CyberDefense #ThreatDetection #InfoSec #MachineLearning #FutureOfCybersecurity #infosectrain