Spear Phishing and How to Prevent It?
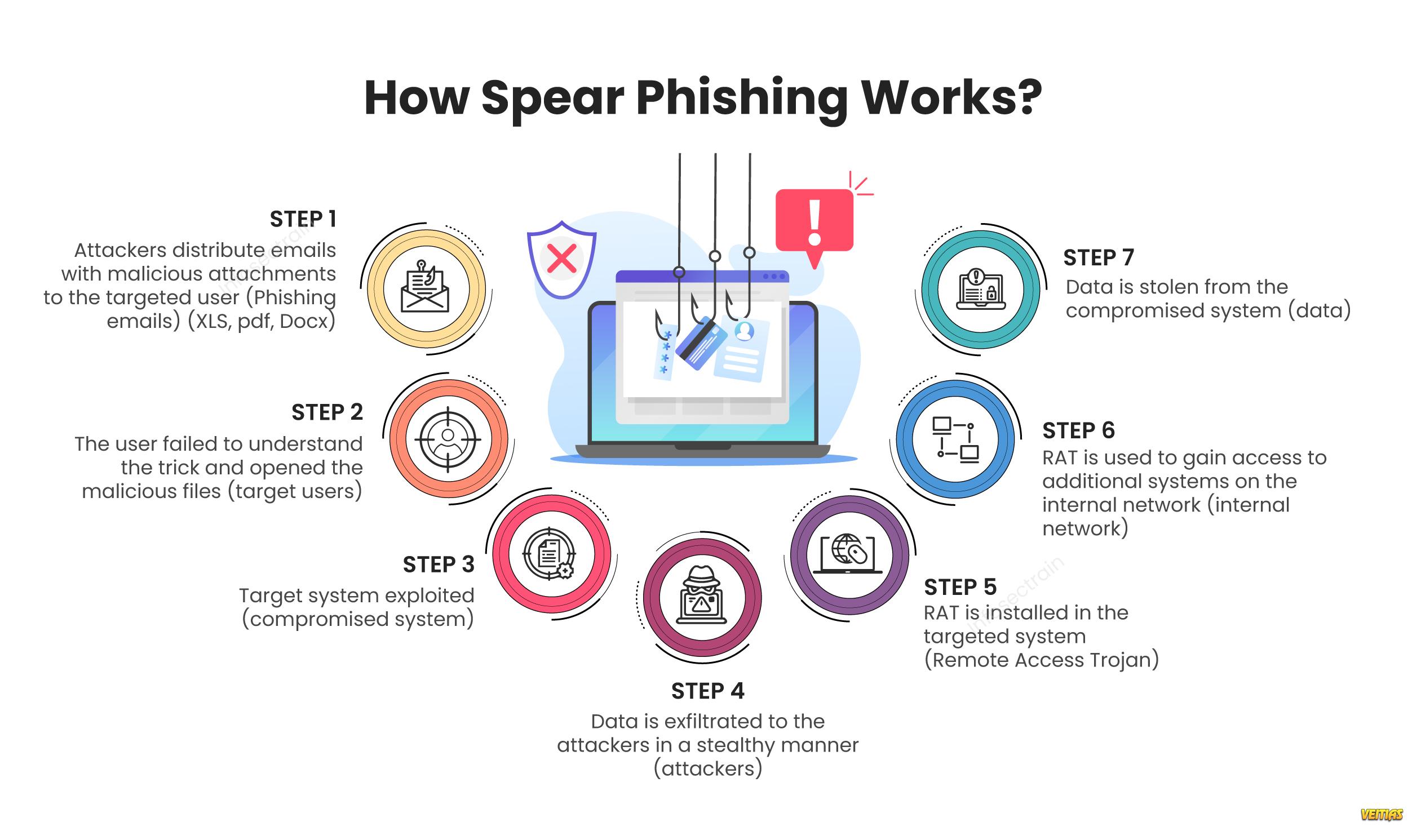
Spear phishing is a targeted attempt to steal sensitive information, such as login credentials or financial information, from specific individuals by posing as a trusted organization. In this blog post, we will look into what spear phishing is, how it works, and most importantly, how you can protect yourself and your organization from falling victim to such attacks. Stay vigilant, stay informed, and prioritize cybersecurity to protect your digital assets from spear phishing and other cyber threats.
Read Here: https://medium.com/@Infosec-Train/spear-phishing-and-how-to-prevent-it-f102423909a9
Learn how to spot and protect yourself from these deceptive scams with our video. Watch Now https://www.youtube.com/watch?v=ChQb_8f3r1M
Don’t forget to subscribe for more cybersecurity tips and tutorials! https://www.youtube.com/@InfosecTrain
Stay safe and keep your defenses strong!
#CyberSecurity #SpearPhishing #PhishingPrevention #CyberAwareness #InfoSec #EmailSecurity #MFA #DataProtection #CyberThreats #StaySafeOnline #infosectrain #learntorise
Spear phishing is a targeted attempt to steal sensitive information, such as login credentials or financial information, from specific individuals by posing as a trusted organization. In this blog post, we will look into what spear phishing is, how it works, and most importantly, how you can protect yourself and your organization from falling victim to such attacks. Stay vigilant, stay informed, and prioritize cybersecurity to protect your digital assets from spear phishing and other cyber threats.
Read Here: https://medium.com/@Infosec-Train/spear-phishing-and-how-to-prevent-it-f102423909a9
Learn how to spot and protect yourself from these deceptive scams with our video. Watch Now https://www.youtube.com/watch?v=ChQb_8f3r1M
Don’t forget to subscribe for more cybersecurity tips and tutorials! https://www.youtube.com/@InfosecTrain
Stay safe and keep your defenses strong!
#CyberSecurity #SpearPhishing #PhishingPrevention #CyberAwareness #InfoSec #EmailSecurity #MFA #DataProtection #CyberThreats #StaySafeOnline #infosectrain #learntorise
Spear Phishing and How to Prevent It?
Spear phishing is a targeted attempt to steal sensitive information, such as login credentials or financial information, from specific individuals by posing as a trusted organization. In this blog post, we will look into what spear phishing is, how it works, and most importantly, how you can protect yourself and your organization from falling victim to such attacks. Stay vigilant, stay informed, and prioritize cybersecurity to protect your digital assets from spear phishing and other cyber threats.
Read Here: https://medium.com/@Infosec-Train/spear-phishing-and-how-to-prevent-it-f102423909a9
Learn how to spot and protect yourself from these deceptive scams with our video. Watch Now 👉 https://www.youtube.com/watch?v=ChQb_8f3r1M
Don’t forget to subscribe for more cybersecurity tips and tutorials! 👉https://www.youtube.com/@InfosecTrain
Stay safe and keep your defenses strong!
#CyberSecurity #SpearPhishing #PhishingPrevention #CyberAwareness #InfoSec #EmailSecurity #MFA #DataProtection #CyberThreats #StaySafeOnline #infosectrain #learntorise
0 Comentários
0 Compartilhamentos
9338 Visualizações
0 Anterior