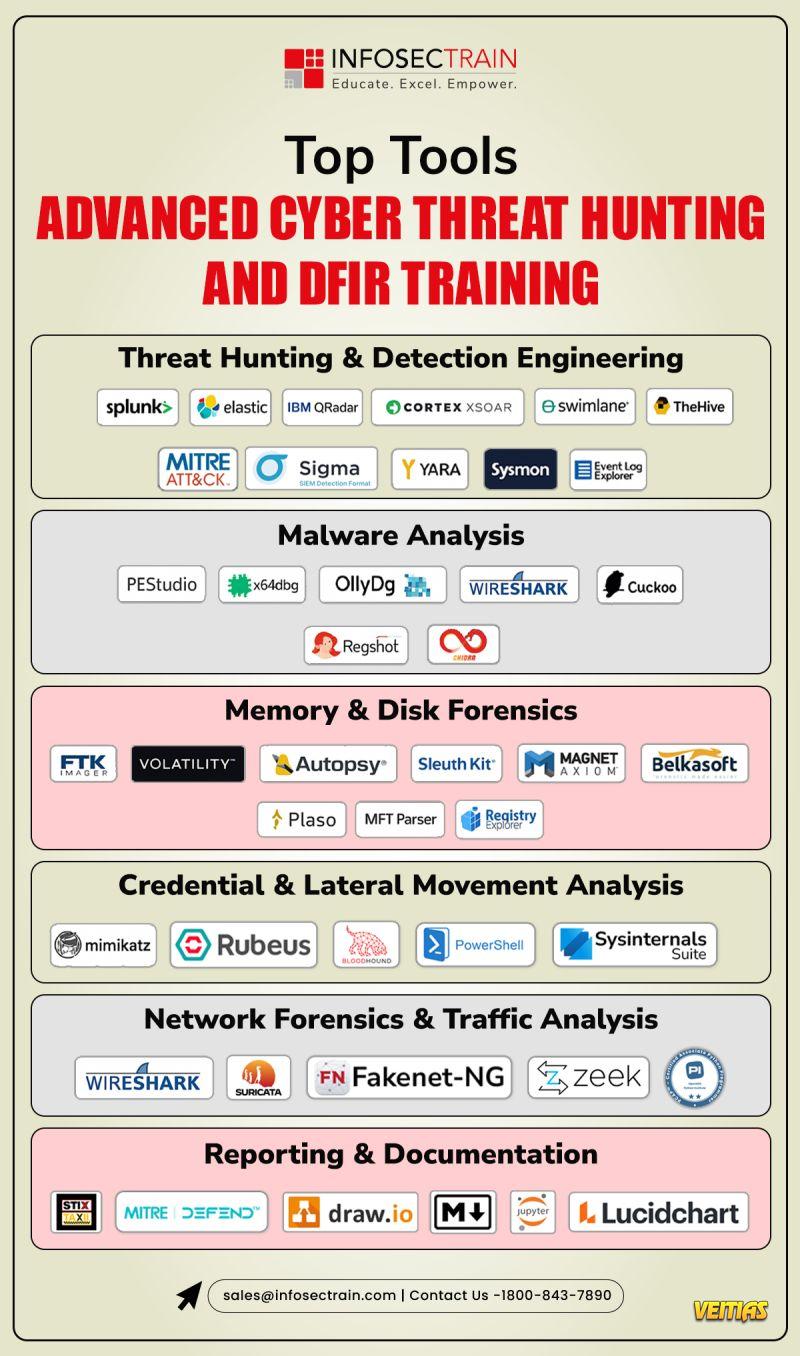
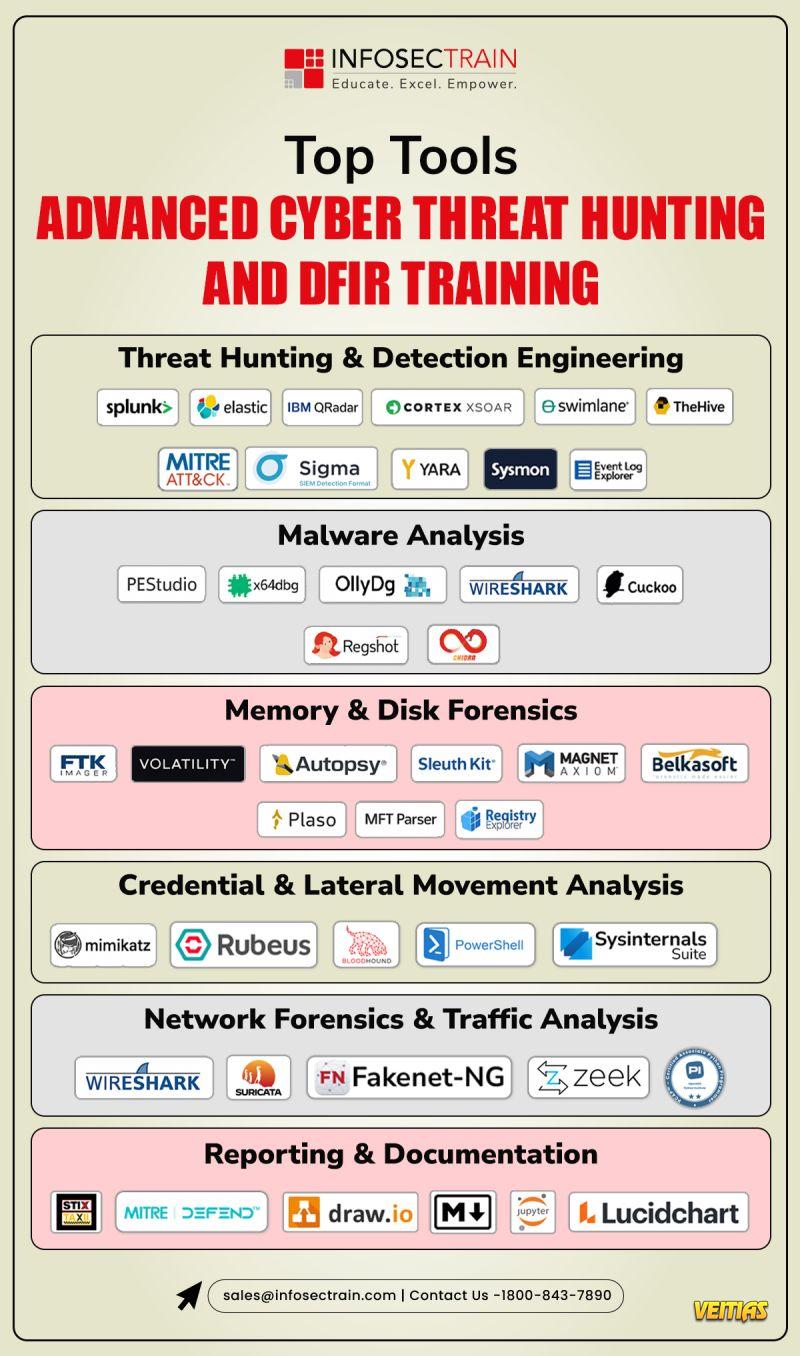
𝐂𝐡𝐨𝐨𝐬𝐢𝐧𝐠 𝐚 𝐒𝐈𝐄𝐌 𝐢𝐬𝐧’𝐭 𝐚𝐛𝐨𝐮𝐭 𝐰𝐡𝐢𝐜𝐡 𝐭𝐨𝐨𝐥 𝐢𝐬 “𝐛𝐞𝐭𝐭𝐞𝐫.”
𝐈𝐭’𝐬 𝐚𝐛𝐨𝐮𝐭 𝐰𝐡𝐢𝐜𝐡 𝐨𝐧𝐞 𝐟𝐢𝐭𝐬 𝐲𝐨𝐮𝐫 𝐫𝐞𝐚𝐥𝐢𝐭𝐲.
Wazuh gives teams 𝐚𝐧 𝐨𝐩𝐞𝐧-𝐬𝐨𝐮𝐫𝐜𝐞, 𝐟𝐥𝐞𝐱𝐢𝐛𝐥𝐞 𝐒𝐈𝐄𝐌 𝐚𝐧𝐝 𝐗𝐃𝐑 𝐩𝐥𝐚𝐭𝐟𝐨𝐫𝐦 𝐰𝐢𝐭𝐡 𝐬𝐭𝐫𝐨𝐧𝐠 𝐜𝐨𝐦𝐩𝐥𝐢𝐚𝐧𝐜𝐞 𝐜𝐨𝐯𝐞𝐫𝐚𝐠𝐞 𝐚𝐧𝐝 𝐟𝐮𝐥𝐥 𝐜𝐨𝐧𝐭𝐫𝐨𝐥.
Splunk offers a polished, enterprise-grade experience built for scale, speed, and managed operations.
𝐁𝐨𝐭𝐡 𝐬𝐨𝐥𝐯𝐞 𝐫𝐞𝐚𝐥 𝐩𝐫𝐨𝐛𝐥𝐞𝐦𝐬.
The difference lies in budget, skills, and how much control you want over your security stack.
𝐈𝐟 𝐲𝐨𝐮’𝐫𝐞 𝐥𝐨𝐨𝐤𝐢𝐧𝐠 𝐭𝐨 𝐛𝐮𝐢𝐥𝐝 𝐡𝐚𝐧𝐝𝐬-𝐨𝐧 𝐒𝐈𝐄𝐌 𝐬𝐤𝐢𝐥𝐥𝐬 𝐰𝐢𝐭𝐡 𝐖𝐚𝐳𝐮𝐡 𝐚𝐧𝐝 𝐮𝐧𝐝𝐞𝐫𝐬𝐭𝐚𝐧𝐝 𝐡𝐨𝐰 𝐢𝐭 𝐰𝐨𝐫𝐤𝐬 𝐢𝐧 𝐫𝐞𝐚𝐥 𝐒𝐎𝐂 𝐞𝐧𝐯𝐢𝐫𝐨𝐧𝐦𝐞𝐧𝐭𝐬, 𝐬𝐭𝐫𝐮𝐜𝐭𝐮𝐫𝐞𝐝 𝐭𝐫𝐚𝐢𝐧𝐢𝐧𝐠 𝐦𝐚𝐤𝐞𝐬 𝐚𝐥𝐥 𝐭𝐡𝐞 𝐝𝐢𝐟𝐟𝐞𝐫𝐞𝐧𝐜𝐞.
𝐈𝐭’𝐬 𝐚𝐛𝐨𝐮𝐭 𝐰𝐡𝐢𝐜𝐡 𝐨𝐧𝐞 𝐟𝐢𝐭𝐬 𝐲𝐨𝐮𝐫 𝐫𝐞𝐚𝐥𝐢𝐭𝐲.
Wazuh gives teams 𝐚𝐧 𝐨𝐩𝐞𝐧-𝐬𝐨𝐮𝐫𝐜𝐞, 𝐟𝐥𝐞𝐱𝐢𝐛𝐥𝐞 𝐒𝐈𝐄𝐌 𝐚𝐧𝐝 𝐗𝐃𝐑 𝐩𝐥𝐚𝐭𝐟𝐨𝐫𝐦 𝐰𝐢𝐭𝐡 𝐬𝐭𝐫𝐨𝐧𝐠 𝐜𝐨𝐦𝐩𝐥𝐢𝐚𝐧𝐜𝐞 𝐜𝐨𝐯𝐞𝐫𝐚𝐠𝐞 𝐚𝐧𝐝 𝐟𝐮𝐥𝐥 𝐜𝐨𝐧𝐭𝐫𝐨𝐥.
Splunk offers a polished, enterprise-grade experience built for scale, speed, and managed operations.
𝐁𝐨𝐭𝐡 𝐬𝐨𝐥𝐯𝐞 𝐫𝐞𝐚𝐥 𝐩𝐫𝐨𝐛𝐥𝐞𝐦𝐬.
The difference lies in budget, skills, and how much control you want over your security stack.
𝐈𝐟 𝐲𝐨𝐮’𝐫𝐞 𝐥𝐨𝐨𝐤𝐢𝐧𝐠 𝐭𝐨 𝐛𝐮𝐢𝐥𝐝 𝐡𝐚𝐧𝐝𝐬-𝐨𝐧 𝐒𝐈𝐄𝐌 𝐬𝐤𝐢𝐥𝐥𝐬 𝐰𝐢𝐭𝐡 𝐖𝐚𝐳𝐮𝐡 𝐚𝐧𝐝 𝐮𝐧𝐝𝐞𝐫𝐬𝐭𝐚𝐧𝐝 𝐡𝐨𝐰 𝐢𝐭 𝐰𝐨𝐫𝐤𝐬 𝐢𝐧 𝐫𝐞𝐚𝐥 𝐒𝐎𝐂 𝐞𝐧𝐯𝐢𝐫𝐨𝐧𝐦𝐞𝐧𝐭𝐬, 𝐬𝐭𝐫𝐮𝐜𝐭𝐮𝐫𝐞𝐝 𝐭𝐫𝐚𝐢𝐧𝐢𝐧𝐠 𝐦𝐚𝐤𝐞𝐬 𝐚𝐥𝐥 𝐭𝐡𝐞 𝐝𝐢𝐟𝐟𝐞𝐫𝐞𝐧𝐜𝐞.
𝐂𝐡𝐨𝐨𝐬𝐢𝐧𝐠 𝐚 𝐒𝐈𝐄𝐌 𝐢𝐬𝐧’𝐭 𝐚𝐛𝐨𝐮𝐭 𝐰𝐡𝐢𝐜𝐡 𝐭𝐨𝐨𝐥 𝐢𝐬 “𝐛𝐞𝐭𝐭𝐞𝐫.”
𝐈𝐭’𝐬 𝐚𝐛𝐨𝐮𝐭 𝐰𝐡𝐢𝐜𝐡 𝐨𝐧𝐞 𝐟𝐢𝐭𝐬 𝐲𝐨𝐮𝐫 𝐫𝐞𝐚𝐥𝐢𝐭𝐲.
Wazuh gives teams 𝐚𝐧 𝐨𝐩𝐞𝐧-𝐬𝐨𝐮𝐫𝐜𝐞, 𝐟𝐥𝐞𝐱𝐢𝐛𝐥𝐞 𝐒𝐈𝐄𝐌 𝐚𝐧𝐝 𝐗𝐃𝐑 𝐩𝐥𝐚𝐭𝐟𝐨𝐫𝐦 𝐰𝐢𝐭𝐡 𝐬𝐭𝐫𝐨𝐧𝐠 𝐜𝐨𝐦𝐩𝐥𝐢𝐚𝐧𝐜𝐞 𝐜𝐨𝐯𝐞𝐫𝐚𝐠𝐞 𝐚𝐧𝐝 𝐟𝐮𝐥𝐥 𝐜𝐨𝐧𝐭𝐫𝐨𝐥.
Splunk offers a polished, enterprise-grade experience built for scale, speed, and managed operations.
𝐁𝐨𝐭𝐡 𝐬𝐨𝐥𝐯𝐞 𝐫𝐞𝐚𝐥 𝐩𝐫𝐨𝐛𝐥𝐞𝐦𝐬.
The difference lies in budget, skills, and how much control you want over your security stack.
𝐈𝐟 𝐲𝐨𝐮’𝐫𝐞 𝐥𝐨𝐨𝐤𝐢𝐧𝐠 𝐭𝐨 𝐛𝐮𝐢𝐥𝐝 𝐡𝐚𝐧𝐝𝐬-𝐨𝐧 𝐒𝐈𝐄𝐌 𝐬𝐤𝐢𝐥𝐥𝐬 𝐰𝐢𝐭𝐡 𝐖𝐚𝐳𝐮𝐡 𝐚𝐧𝐝 𝐮𝐧𝐝𝐞𝐫𝐬𝐭𝐚𝐧𝐝 𝐡𝐨𝐰 𝐢𝐭 𝐰𝐨𝐫𝐤𝐬 𝐢𝐧 𝐫𝐞𝐚𝐥 𝐒𝐎𝐂 𝐞𝐧𝐯𝐢𝐫𝐨𝐧𝐦𝐞𝐧𝐭𝐬, 𝐬𝐭𝐫𝐮𝐜𝐭𝐮𝐫𝐞𝐝 𝐭𝐫𝐚𝐢𝐧𝐢𝐧𝐠 𝐦𝐚𝐤𝐞𝐬 𝐚𝐥𝐥 𝐭𝐡𝐞 𝐝𝐢𝐟𝐟𝐞𝐫𝐞𝐧𝐜𝐞.
0 Commenti
0 condivisioni
2175 Views
0 Anteprima