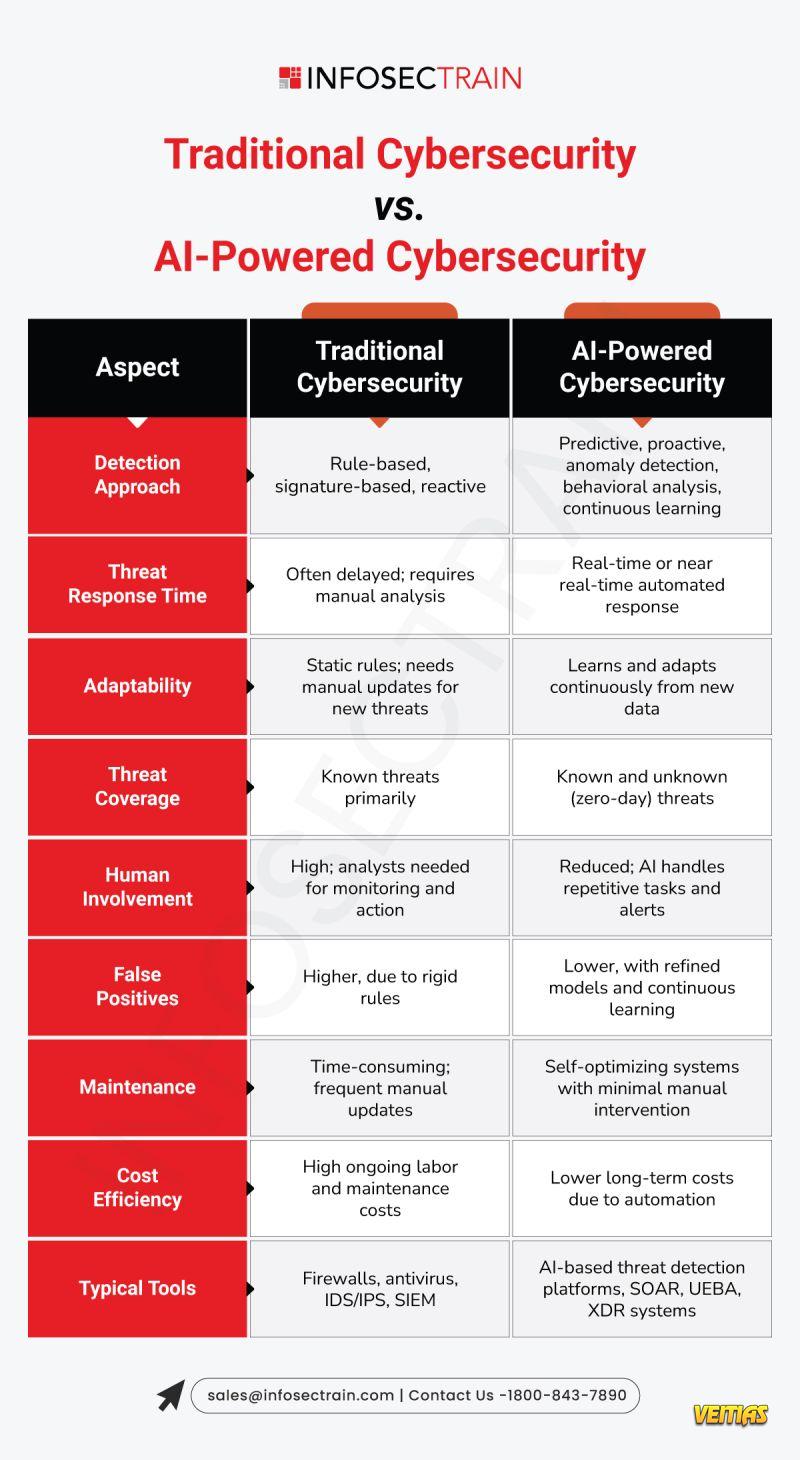
Dock Cushion Seals
DockTechnik offer a range of Loading Bay Dock Shelters including the Dock Cushion Seals. Our Services include Dock Cushion Seals Service, Repairs, Sales and Design.
About Company-
Dock Technik are the leading supplier of loading bay services and systems in the UK. Dock Technik believe loading bay equipment is essential to the effective, efficient and safe handling of goods.
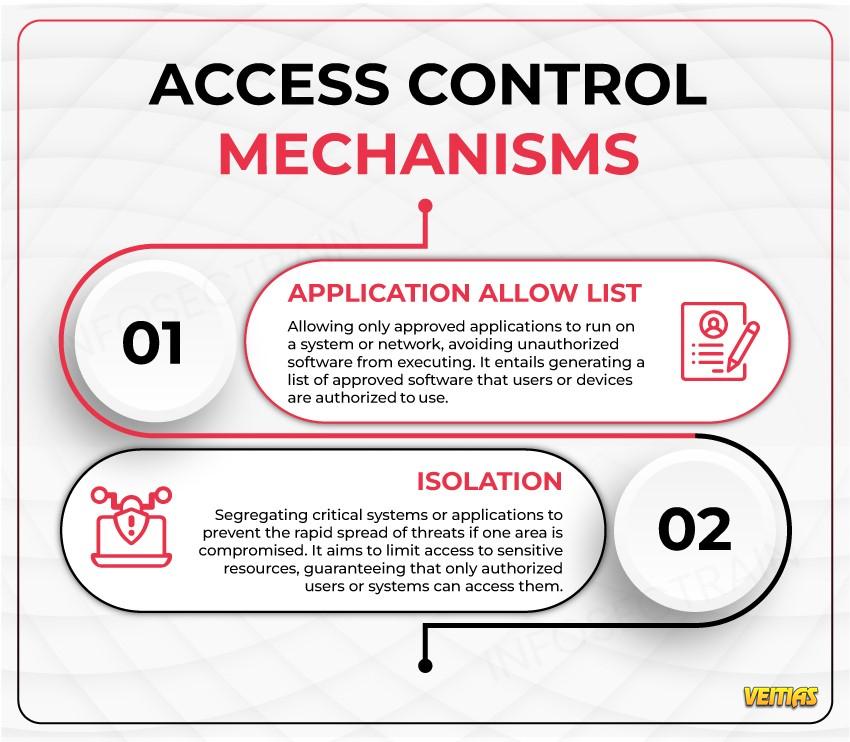
Dock Technik offer a full range of loading bay solutions and products including Service, Repair & Call Out, Design and Installation and a range of loading bay products and services including Industrial Doors, Dock Levellers, Dock Shelters, Scissor Lifting Tables, Load Houses, Dock Buffers, Wheel alignment guides, Loading Bay Lighting, PVC Strip Curtains, Loading Bay Pest Proofing, Loading Bay Safety & associated accessories and equipment. Dock Technik aim to ensure the loading and unloading process is safe and effective to enable the distribution network to operate seamlessly.
Dock Technik offer a unique one stop shop for loading systems products and solutions throughout the United Kingdom - 24/7.
Click Here For More Info:- https://www.docktechnik.com/dockcushionseals
Social Media Profile Links-
https://www.linkedin.com/company/docktechnik/
https://www.facebook.com/DOCKTECHNIK
https://www.instagram.com/docktechnik/
DockTechnik offer a range of Loading Bay Dock Shelters including the Dock Cushion Seals. Our Services include Dock Cushion Seals Service, Repairs, Sales and Design.
About Company-
Dock Technik are the leading supplier of loading bay services and systems in the UK. Dock Technik believe loading bay equipment is essential to the effective, efficient and safe handling of goods.
Dock Technik offer a full range of loading bay solutions and products including Service, Repair & Call Out, Design and Installation and a range of loading bay products and services including Industrial Doors, Dock Levellers, Dock Shelters, Scissor Lifting Tables, Load Houses, Dock Buffers, Wheel alignment guides, Loading Bay Lighting, PVC Strip Curtains, Loading Bay Pest Proofing, Loading Bay Safety & associated accessories and equipment. Dock Technik aim to ensure the loading and unloading process is safe and effective to enable the distribution network to operate seamlessly.
Dock Technik offer a unique one stop shop for loading systems products and solutions throughout the United Kingdom - 24/7.
Click Here For More Info:- https://www.docktechnik.com/dockcushionseals
Social Media Profile Links-
https://www.linkedin.com/company/docktechnik/
https://www.facebook.com/DOCKTECHNIK
https://www.instagram.com/docktechnik/
Dock Cushion Seals
DockTechnik offer a range of Loading Bay Dock Shelters including the Dock Cushion Seals. Our Services include Dock Cushion Seals Service, Repairs, Sales and Design.
About Company-
Dock Technik are the leading supplier of loading bay services and systems in the UK. Dock Technik believe loading bay equipment is essential to the effective, efficient and safe handling of goods.
Dock Technik offer a full range of loading bay solutions and products including Service, Repair & Call Out, Design and Installation and a range of loading bay products and services including Industrial Doors, Dock Levellers, Dock Shelters, Scissor Lifting Tables, Load Houses, Dock Buffers, Wheel alignment guides, Loading Bay Lighting, PVC Strip Curtains, Loading Bay Pest Proofing, Loading Bay Safety & associated accessories and equipment. Dock Technik aim to ensure the loading and unloading process is safe and effective to enable the distribution network to operate seamlessly.
Dock Technik offer a unique one stop shop for loading systems products and solutions throughout the United Kingdom - 24/7.
Click Here For More Info:- https://www.docktechnik.com/dockcushionseals
Social Media Profile Links-
https://www.linkedin.com/company/docktechnik/
https://www.facebook.com/DOCKTECHNIK
https://www.instagram.com/docktechnik/
0 Commentaires
0 Parts
2803 Vue
0 Aperçu