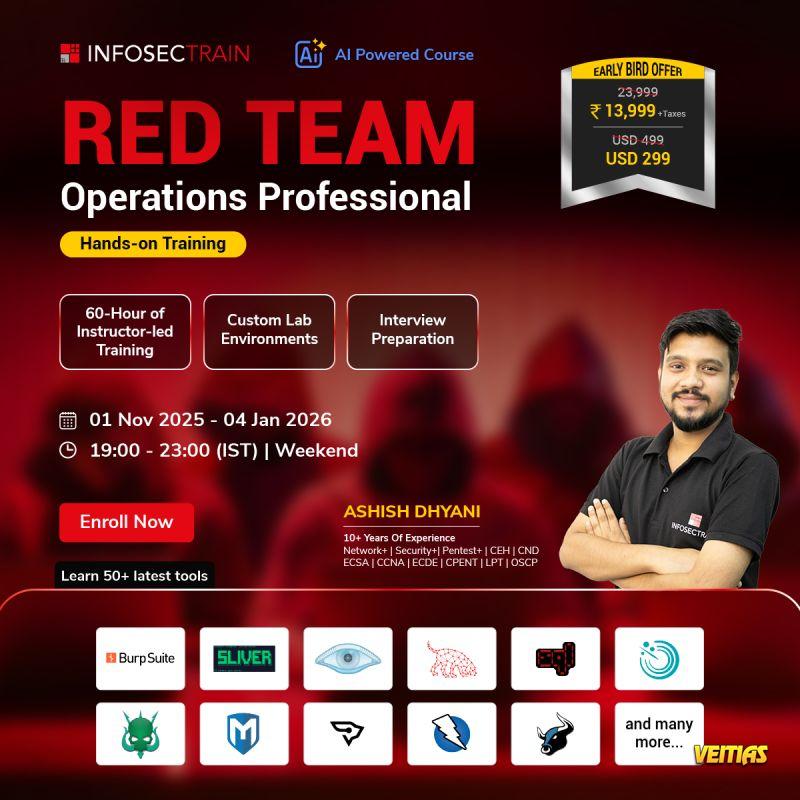
Red Teaming & Penetration Testing Complete Training Course
What you’ll learn:
Foundations of offensive security
Deep dive into penetration testing
Types of penetration testing
Deep dive into red teaming
Role of the Blue Team
Key differences & practical applications
When to choose Pen Test vs Red Team
Watch Here: https://youtu.be/YMACCMLe8XI?si=nKapsUQrZvpVOtcD
#RedTeaming #PenetrationTesting #CyberSecurity #OffensiveSecurity #BlueTeam #InfoSec #EthicalHacking #SecurityTesting #InfosecTrain
What you’ll learn:
Foundations of offensive security
Deep dive into penetration testing
Types of penetration testing
Deep dive into red teaming
Role of the Blue Team
Key differences & practical applications
When to choose Pen Test vs Red Team
Watch Here: https://youtu.be/YMACCMLe8XI?si=nKapsUQrZvpVOtcD
#RedTeaming #PenetrationTesting #CyberSecurity #OffensiveSecurity #BlueTeam #InfoSec #EthicalHacking #SecurityTesting #InfosecTrain
Red Teaming & Penetration Testing Complete Training Course
🎯 What you’ll learn:
✅ Foundations of offensive security
✅ Deep dive into penetration testing
✅ Types of penetration testing
✅ Deep dive into red teaming
✅ Role of the Blue Team
✅ Key differences & practical applications
✅ When to choose Pen Test vs Red Team
Watch Here: https://youtu.be/YMACCMLe8XI?si=nKapsUQrZvpVOtcD
#RedTeaming #PenetrationTesting #CyberSecurity #OffensiveSecurity #BlueTeam #InfoSec #EthicalHacking #SecurityTesting #InfosecTrain

0 Commentarios
0 Acciones
2543 Views
0 Vista previa