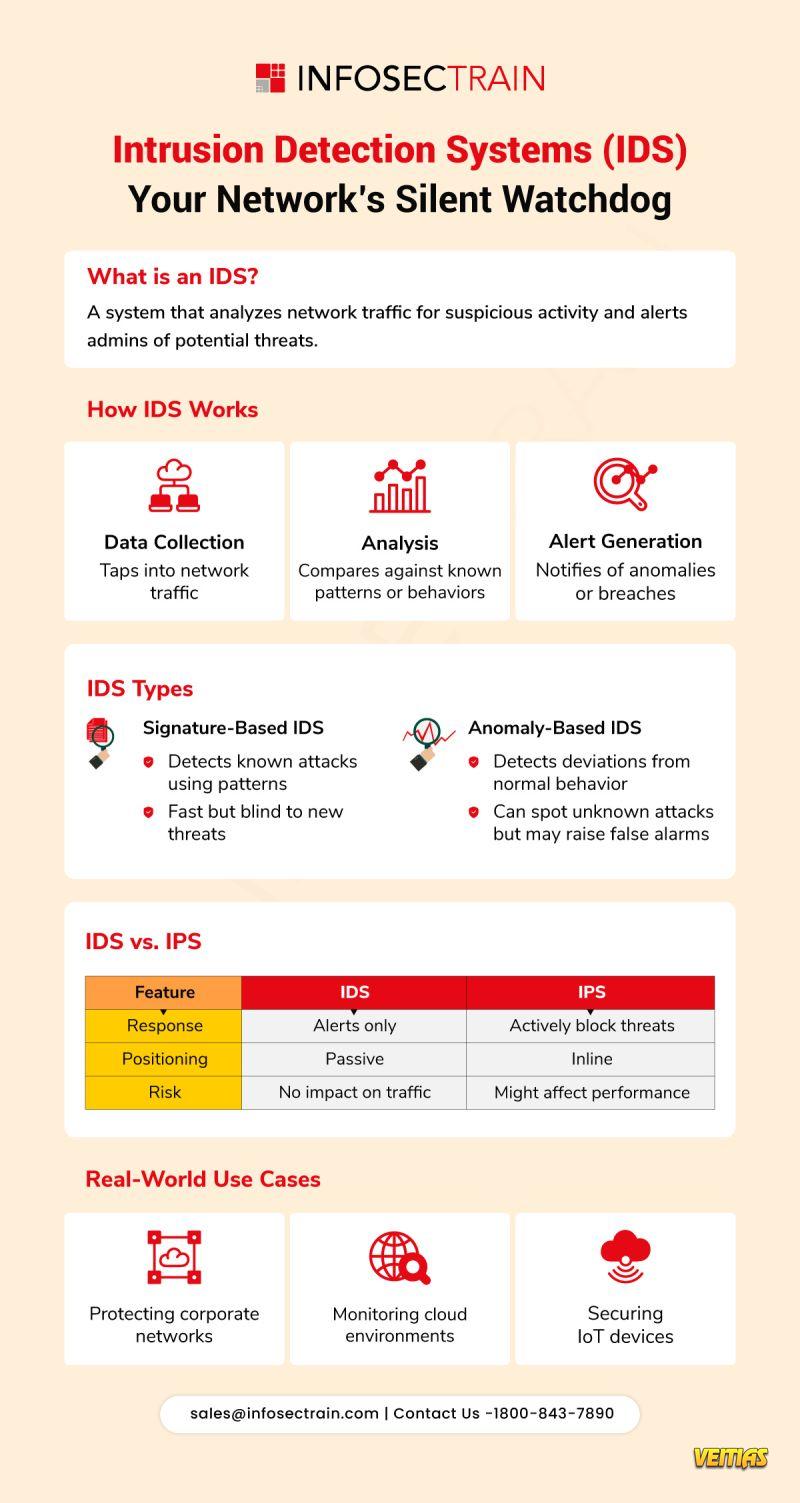
Intrusion Detection Systems (IDS): Your Network’s Silent Watchdog
Monitors traffic. Spots threats. Alerts fast.
An IDS keeps a constant eye on your network — even when you’re not!
Types of IDS
Signature-Based: Fast but blind to new threats
Anomaly-Based: Detects unknowns, may raise false alarms
IDS vs. IPS
IDS = Alerts only
IPS = Blocks threats
Where It’s Used:
Corporate Networks | Cloud Environments | IoT Devices
Stay informed. Stay secure. Learn more with InfosecTrain https://www.infosectrain.com/events/
#IDS #IntrusionDetection #CyberSecurity #NetworkSecurity #InfoSec #InfosecTrain #IPS #ThreatDetection #SIEM #CyberDefense #IoTSecurity #RedTeam #BlueTeam #SecurityTools
Monitors traffic. Spots threats. Alerts fast.
An IDS keeps a constant eye on your network — even when you’re not!
Types of IDS
Signature-Based: Fast but blind to new threats
Anomaly-Based: Detects unknowns, may raise false alarms
IDS vs. IPS
IDS = Alerts only
IPS = Blocks threats
Where It’s Used:
Corporate Networks | Cloud Environments | IoT Devices
Stay informed. Stay secure. Learn more with InfosecTrain https://www.infosectrain.com/events/
#IDS #IntrusionDetection #CyberSecurity #NetworkSecurity #InfoSec #InfosecTrain #IPS #ThreatDetection #SIEM #CyberDefense #IoTSecurity #RedTeam #BlueTeam #SecurityTools
Intrusion Detection Systems (IDS): Your Network’s Silent Watchdog
Monitors traffic. Spots threats. Alerts fast. ⚡
An IDS keeps a constant eye on your network — even when you’re not! 👀
⚙️ Types of IDS
🔸 Signature-Based: Fast but blind to new threats
🔸 Anomaly-Based: Detects unknowns, may raise false alarms
⚔️ IDS vs. IPS
🔹 IDS = Alerts only 🔔
🔹 IPS = Blocks threats 🔐
📌 Where It’s Used:
🏢 Corporate Networks | ☁️ Cloud Environments | 📡 IoT Devices
🔍 Stay informed. Stay secure. Learn more with InfosecTrain https://www.infosectrain.com/events/
#IDS #IntrusionDetection #CyberSecurity #NetworkSecurity #InfoSec #InfosecTrain #IPS #ThreatDetection #SIEM #CyberDefense #IoTSecurity #RedTeam #BlueTeam #SecurityTools
0 Comentários
0 Compartilhamentos
5317 Visualizações
0 Anterior