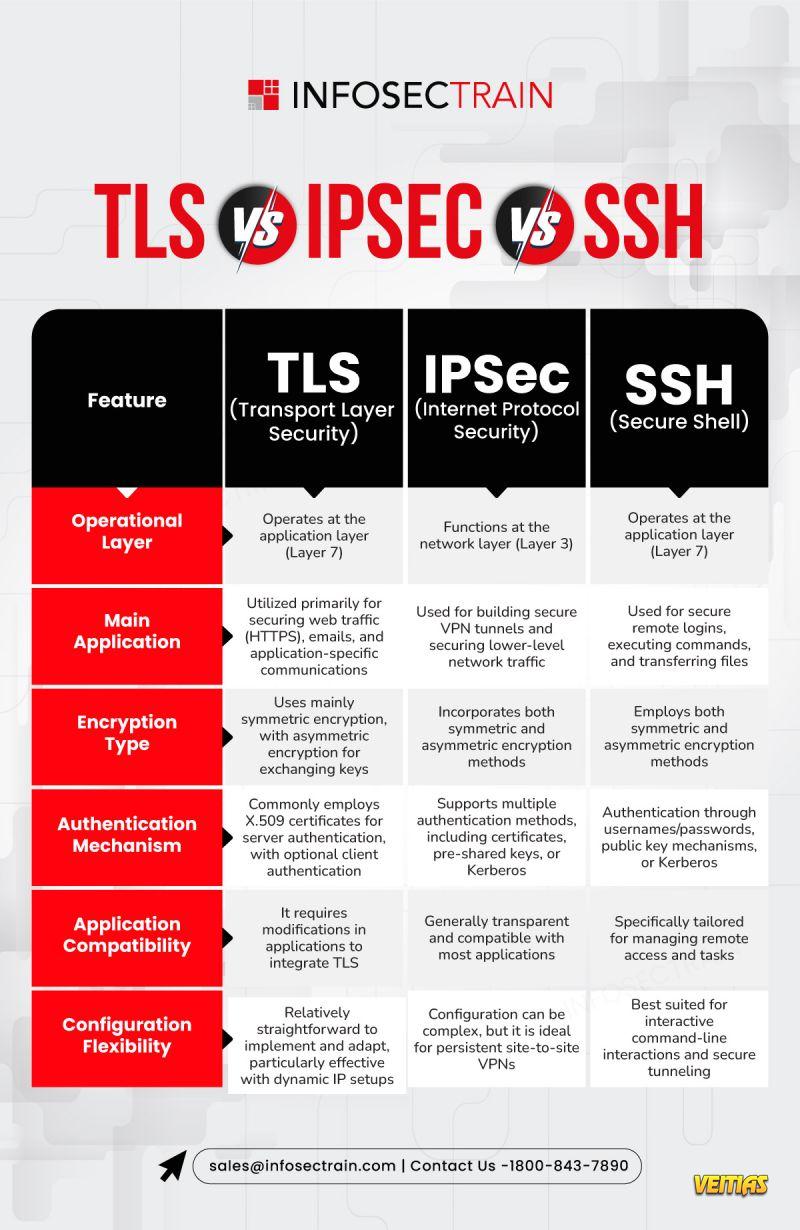
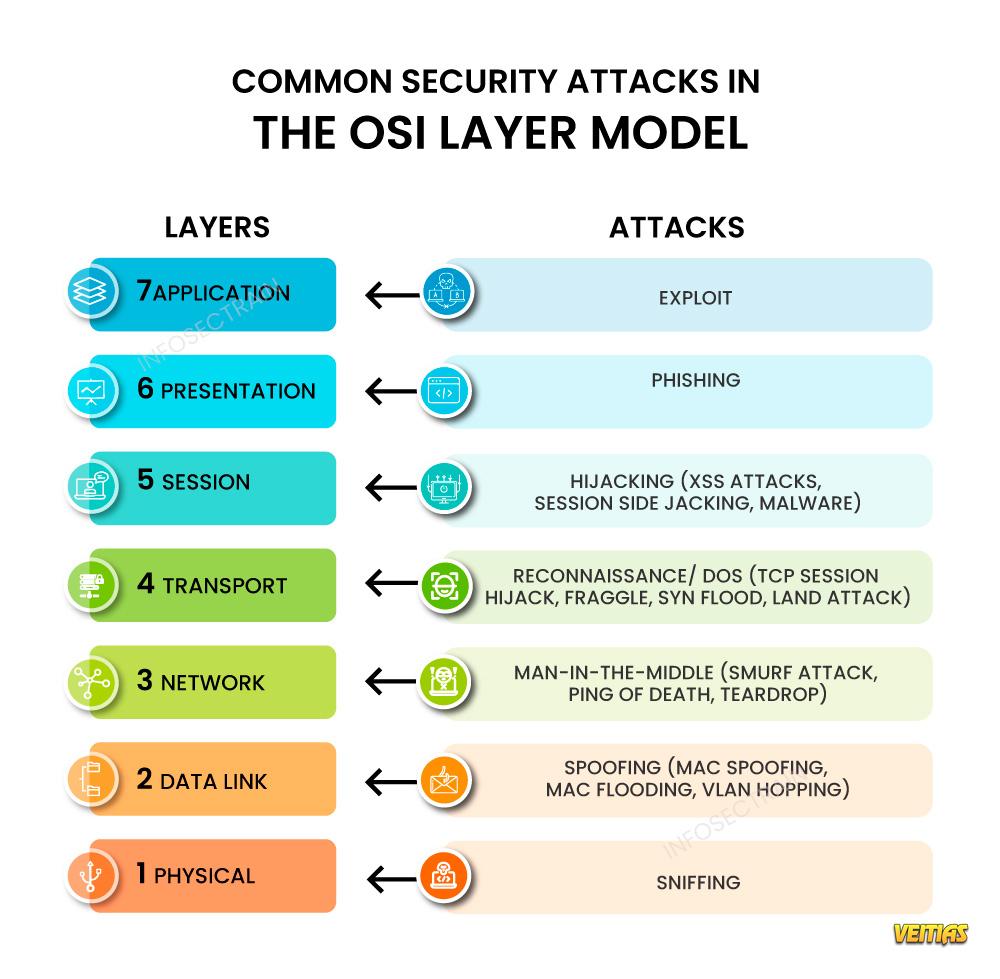
Common Security Attacks in the OSI Model
Have you considered how cyber-attacks target various layers of your network? Here’s a look at some common vulnerabilities:
Application Layer : This layer is susceptible to exploits where attackers leverage software vulnerabilities.
Presentation Layer : Phishing attacks can deceive users into disclosing sensitive information, putting data security at risk.
Session Layer : Be cautious of hijacking, where attackers can take control of user sessions, gaining unauthorized access.
Transport Layer : Reconnaissance attacks collect information about your system, often paving the way for larger and more damaging assaults.
Network Layer : MITM (Man-in-the-Middle) attacks can intercept communications between systems, enabling eavesdropping and data theft.
Data Link Layer : Spoofing allows attackers to masquerade as legitimate devices on your network, circumventing security protocols.
Physical Layer : Attacks such as cable tapping and physical device tampering can compromise the integrity of your network infrastructure.
Read more:
https://www.infosectrain.com/blog/common-security-attacks-in-the-osi-layer-model/
Recognizing these threats is essential for fortifying defenses against cyber-attacks. Stay vigilant!
#SecurityAttacks #OSIMode #CyberSecurity #NetworkSecurity #DataProtection #InfoSec #CyberThreats #Malware #PenetrationTesting #NetworkDefense #ApplicationSecurity #ThreatDetection #VulnerabilityManagement #infosectrainCommon Security Attacks in the OSI Model
Have you considered how cyber-attacks target various layers of your network? Here’s a look at some common vulnerabilities:
Application Layer : This layer is susceptible to exploits where attackers leverage software vulnerabilities.
Presentation Layer : Phishing attacks can deceive users into disclosing sensitive information, putting data security at risk.
Session Layer : Be cautious of hijacking, where attackers can take control of user sessions, gaining unauthorized access.
Transport Layer : Reconnaissance attacks collect information about your system, often paving the way for larger and more damaging assaults.
Network Layer : MITM (Man-in-the-Middle) attacks can intercept communications between systems, enabling eavesdropping and data theft.
Data Link Layer : Spoofing allows attackers to masquerade as legitimate devices on your network, circumventing security protocols.
Physical Layer : Attacks such as cable tapping and physical device tampering can compromise the integrity of your network infrastructure.
Read more: https://www.infosectrain.com/blog/common-security-attacks-in-the-osi-layer-model/
Recognizing these threats is essential for fortifying defenses against cyber-attacks. Stay vigilant!
#SecurityAttacks #OSIMode #CyberSecurity #NetworkSecurity #DataProtection #InfoSec #CyberThreats #Malware #PenetrationTesting #NetworkDefense #ApplicationSecurity #ThreatDetection #VulnerabilityManagement #infosectrain