How Does a CSRF Attack Work? Protect Your Web Applications!
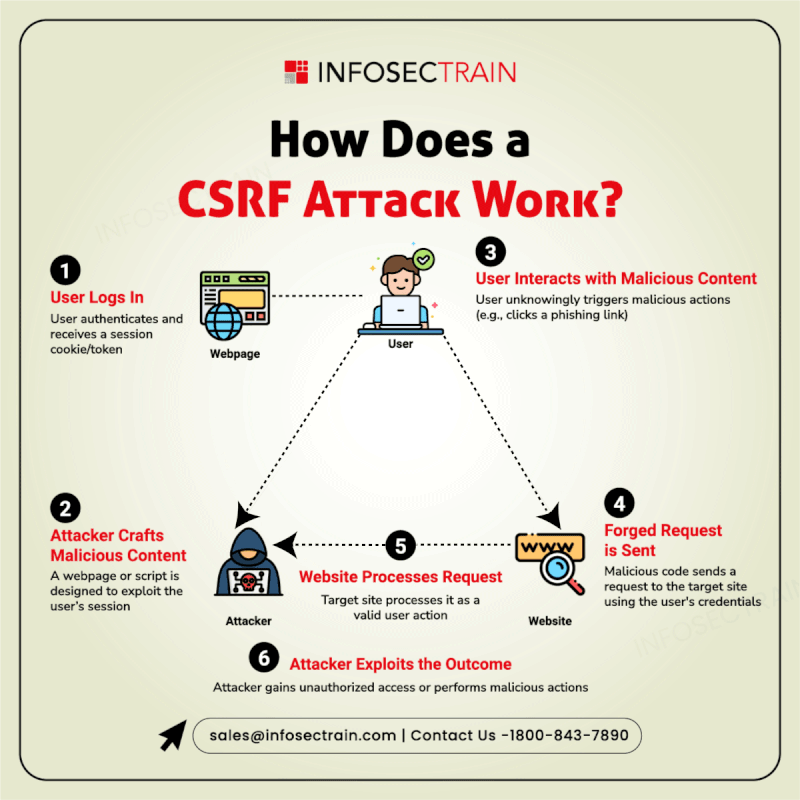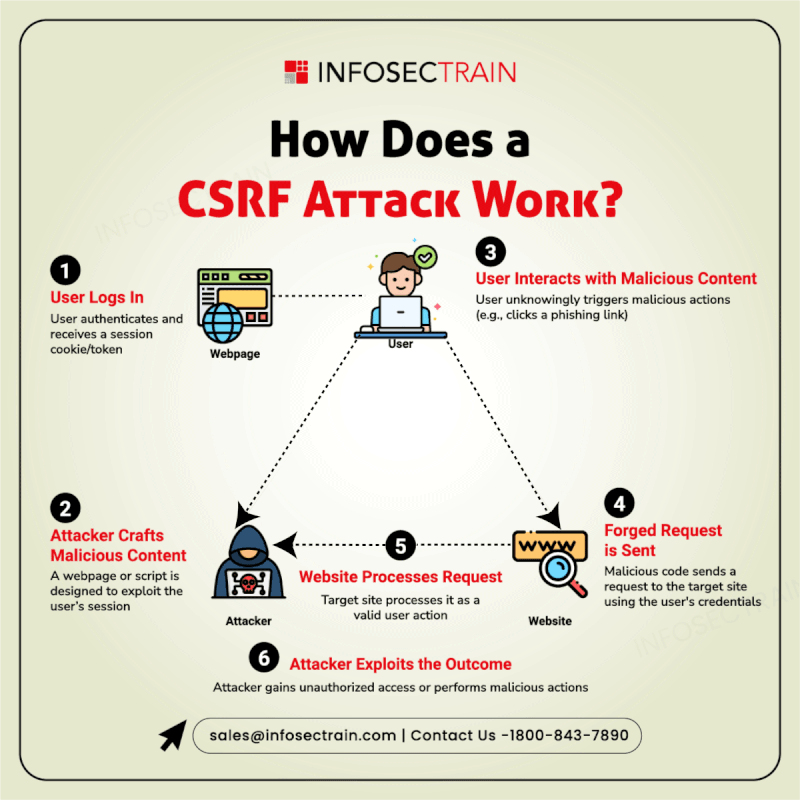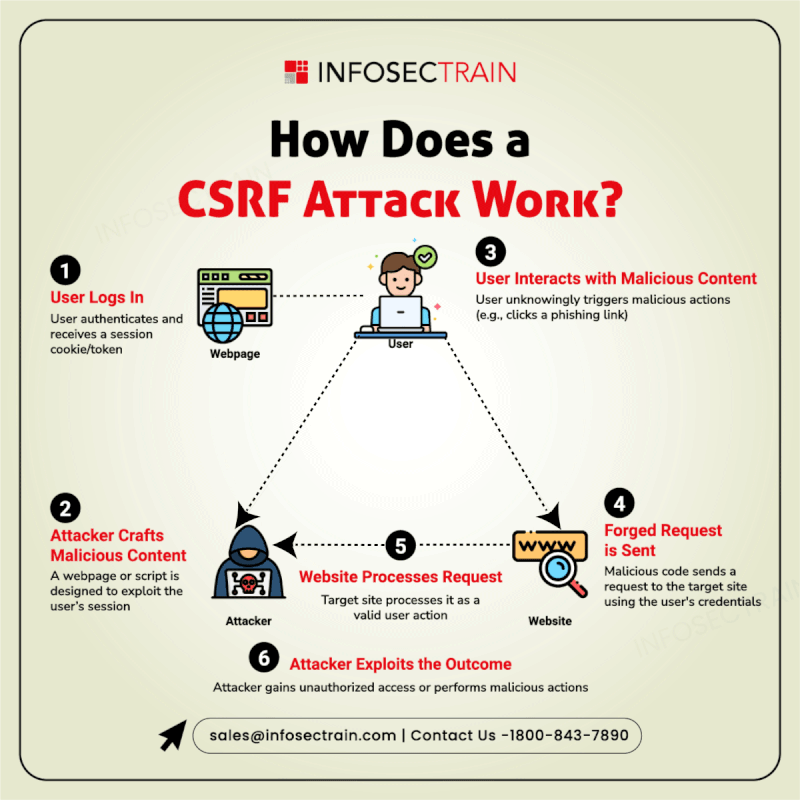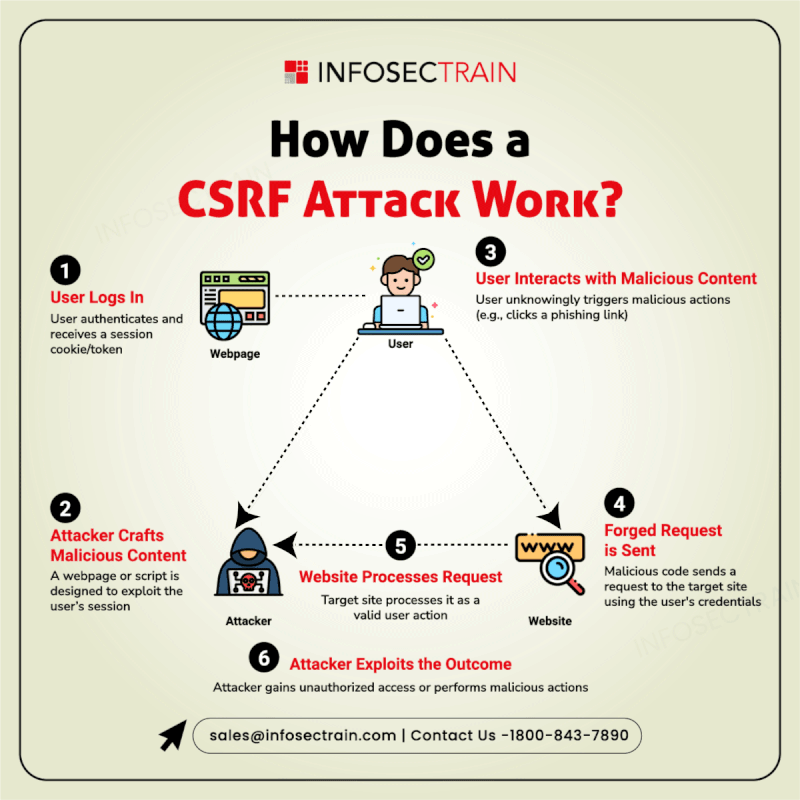
A Cross-Site Request Forgery (CSRF) attack tricks users into unknowingly executing malicious actions on a trusted website where they are authenticated. InfosecTrain’s latest infographic explains the attack process:
More Info: https://www.infosectrain.com/blog/what-is-owasp-zed-attack-proxy-zap/
Prevent CSRF attacks with security best practices and expert training from InfosecTrain!
#CSRF #CyberSecurity #WebSecurity #Hackers #Phishing #Attack #Security Awareness #SecureCoding #WebAppSecurity #infosectrain #learntorise
A Cross-Site Request Forgery (CSRF) attack tricks users into unknowingly executing malicious actions on a trusted website where they are authenticated. InfosecTrain’s latest infographic explains the attack process:
More Info: https://www.infosectrain.com/blog/what-is-owasp-zed-attack-proxy-zap/
Prevent CSRF attacks with security best practices and expert training from InfosecTrain!
#CSRF #CyberSecurity #WebSecurity #Hackers #Phishing #Attack #Security Awareness #SecureCoding #WebAppSecurity #infosectrain #learntorise
How Does a CSRF Attack Work? Protect Your Web Applications!
A Cross-Site Request Forgery (CSRF) attack tricks users into unknowingly executing malicious actions on a trusted website where they are authenticated. InfosecTrain’s latest infographic explains the attack process:
More Info: https://www.infosectrain.com/blog/what-is-owasp-zed-attack-proxy-zap/
Prevent CSRF attacks with security best practices and expert training from InfosecTrain!
#CSRF #CyberSecurity #WebSecurity #Hackers #Phishing #Attack #Security Awareness #SecureCoding #WebAppSecurity #infosectrain #learntorise
0 Commentarios
0 Acciones
13700 Views
0 Vista previa