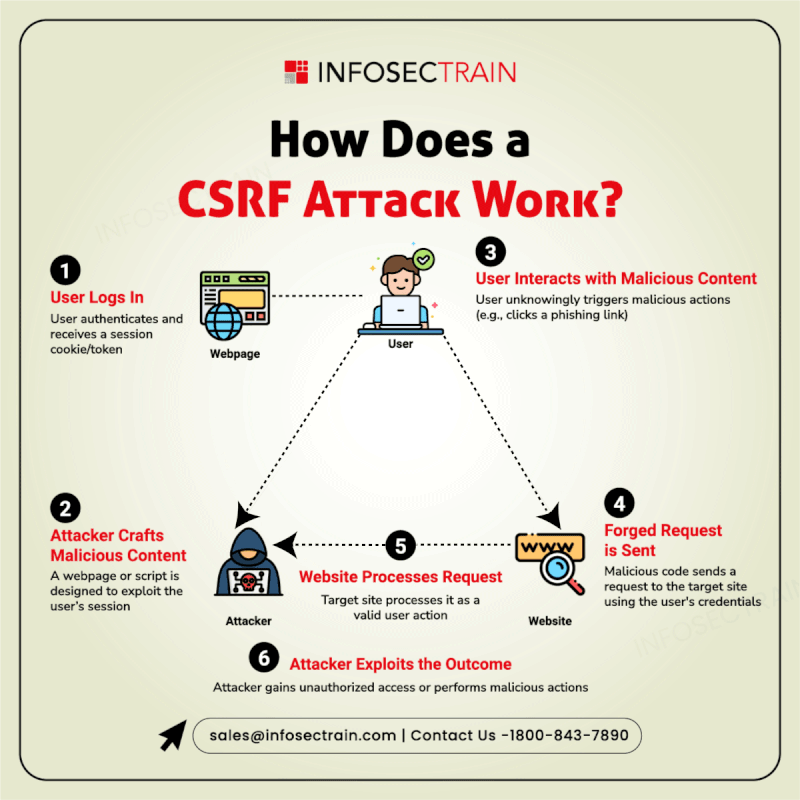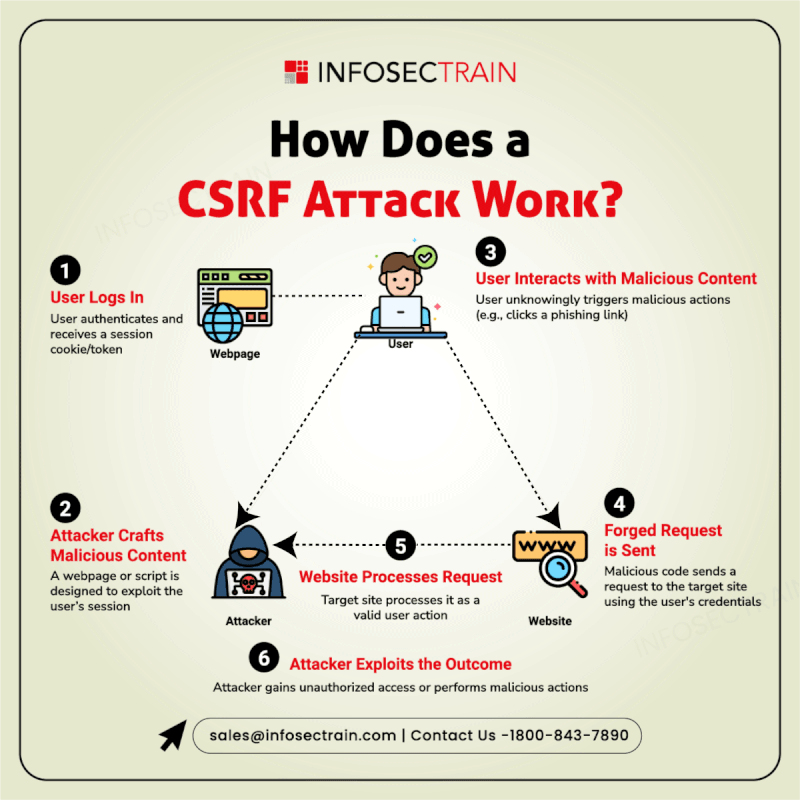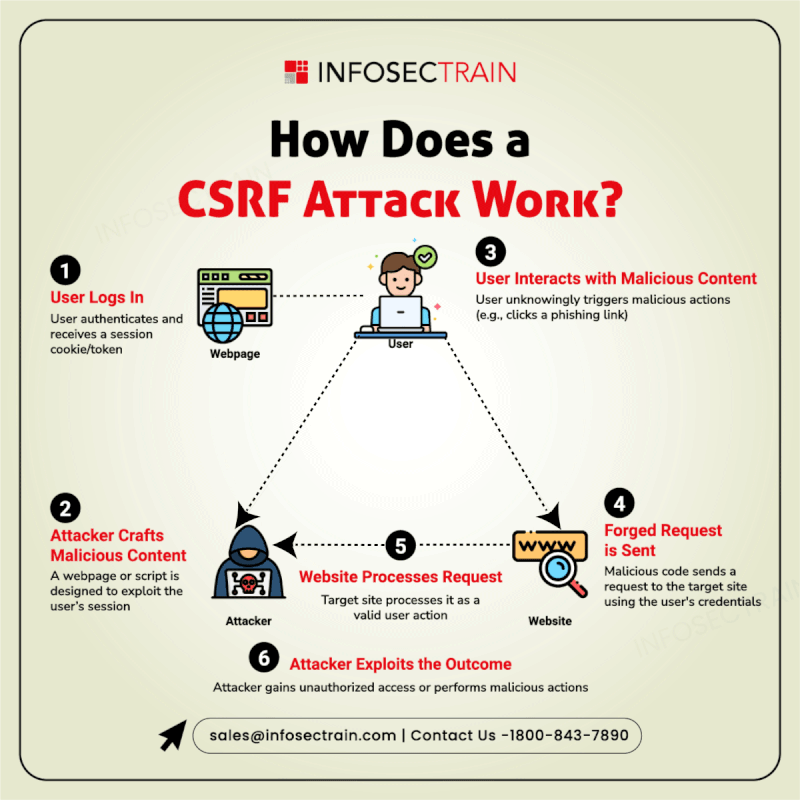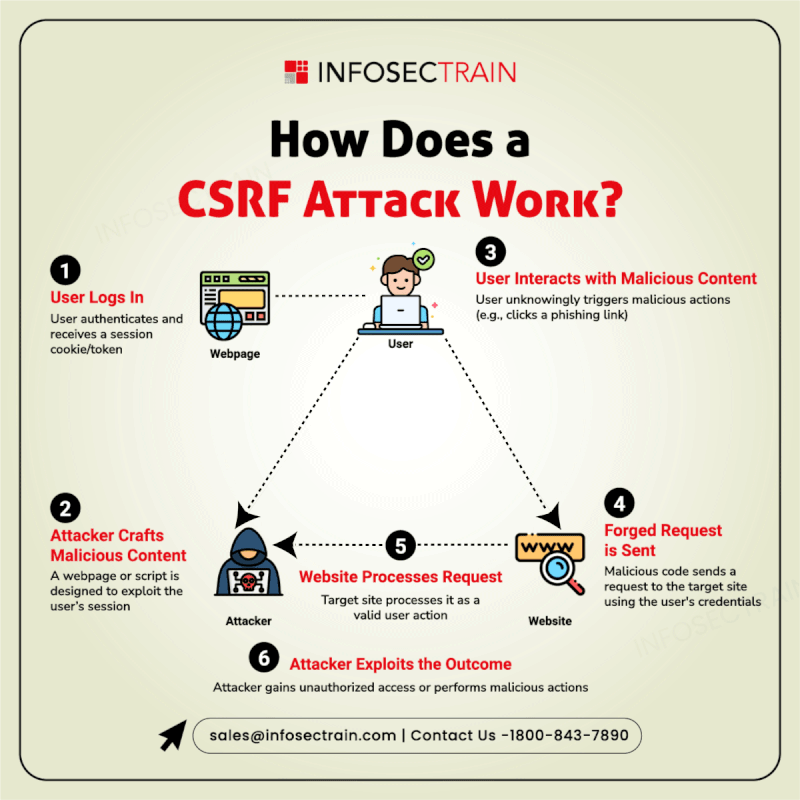
Secure Your Code from the Inside Out!
When it comes to application security, one method isn’t enough. Learn how to strengthen your defenses with the three essential AppSec testing techniques every development team should know:
SAST – Analyze source code before execution
DAST – Simulate real-world attacks on running apps
IAST – Get real-time insights by combining both!
Know the difference. Apply the right method. Secure smarter.
Read more here: https://www.infosectrain.com/blog/sast-vs-dast-vs-iast/
#AppSec #SAST #DAST #IAST #SoftwareSecurity #SDLC #CyberSecurity #ApplicationSecurity #SecureCode #DevSecOps #InfoSec #InfosecTrain #CodeSecure #VulnerabilityTesting #WebAppSecurity
When it comes to application security, one method isn’t enough. Learn how to strengthen your defenses with the three essential AppSec testing techniques every development team should know:
SAST – Analyze source code before execution
DAST – Simulate real-world attacks on running apps
IAST – Get real-time insights by combining both!
Know the difference. Apply the right method. Secure smarter.
Read more here: https://www.infosectrain.com/blog/sast-vs-dast-vs-iast/
#AppSec #SAST #DAST #IAST #SoftwareSecurity #SDLC #CyberSecurity #ApplicationSecurity #SecureCode #DevSecOps #InfoSec #InfosecTrain #CodeSecure #VulnerabilityTesting #WebAppSecurity
Secure Your Code from the Inside Out!
When it comes to application security, one method isn’t enough. Learn how to strengthen your defenses with the three essential AppSec testing techniques every development team should know:
✅ SAST – Analyze source code before execution
✅ DAST – Simulate real-world attacks on running apps
✅ IAST – Get real-time insights by combining both!
Know the difference. Apply the right method. Secure smarter.
Read more here: https://www.infosectrain.com/blog/sast-vs-dast-vs-iast/
#AppSec #SAST #DAST #IAST #SoftwareSecurity #SDLC #CyberSecurity #ApplicationSecurity #SecureCode #DevSecOps #InfoSec #InfosecTrain #CodeSecure #VulnerabilityTesting #WebAppSecurity
0 Comments
0 Shares
4901 Views
0 Reviews