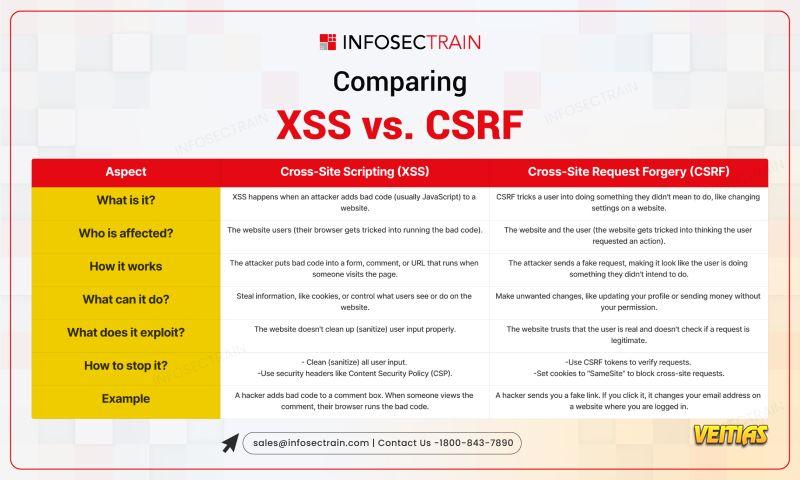
Both XSS (Cross-Site Scripting) and CSRF (Cross-Site Request Forgery) are common web vulnerabilities, but they work in very different ways. Understanding their key differences is critical for secure coding practices! Check out this infographic to understand XSS vs CSRF Linkedin Sales Solutions Generate sales and close deals with Linkedin Sales Navigator
More Info: - https://www.infosectrain.com/blog/top-tools-for-website-security-audit/
#XSS #CSRF #WebSecurity #Cyber Security #SecureCoding #InfosecTrain #OWASP #CyberThreats #WebVulnerabilities
More Info: - https://www.infosectrain.com/blog/top-tools-for-website-security-audit/
#XSS #CSRF #WebSecurity #Cyber Security #SecureCoding #InfosecTrain #OWASP #CyberThreats #WebVulnerabilities
Both XSS (Cross-Site Scripting) and CSRF (Cross-Site Request Forgery) are common web vulnerabilities, but they work in very different ways. Understanding their key differences is critical for secure coding practices! Check out this infographic to understand XSS vs CSRF Linkedin Sales Solutions Generate sales and close deals with Linkedin Sales Navigator
More Info: - https://www.infosectrain.com/blog/top-tools-for-website-security-audit/
#XSS #CSRF #WebSecurity #Cyber Security #SecureCoding #InfosecTrain #OWASP #CyberThreats #WebVulnerabilities
0 Kommentare
0 Anteile
5649 Ansichten
0 Vorschau