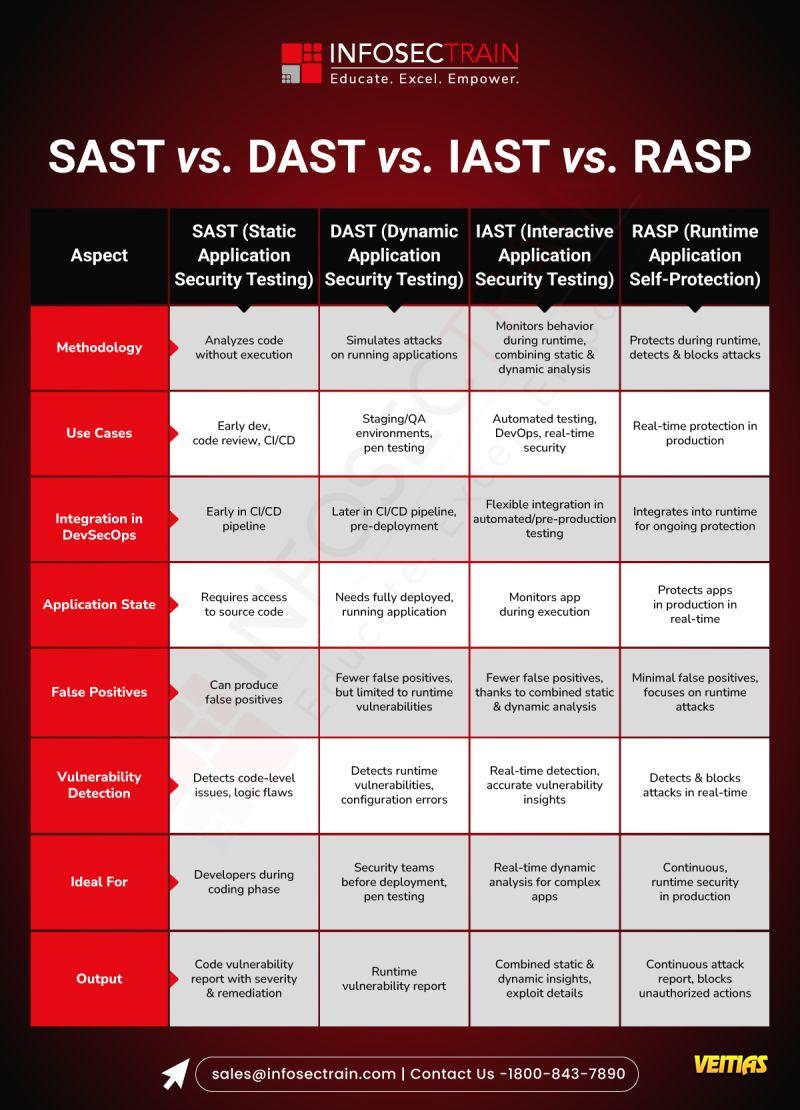
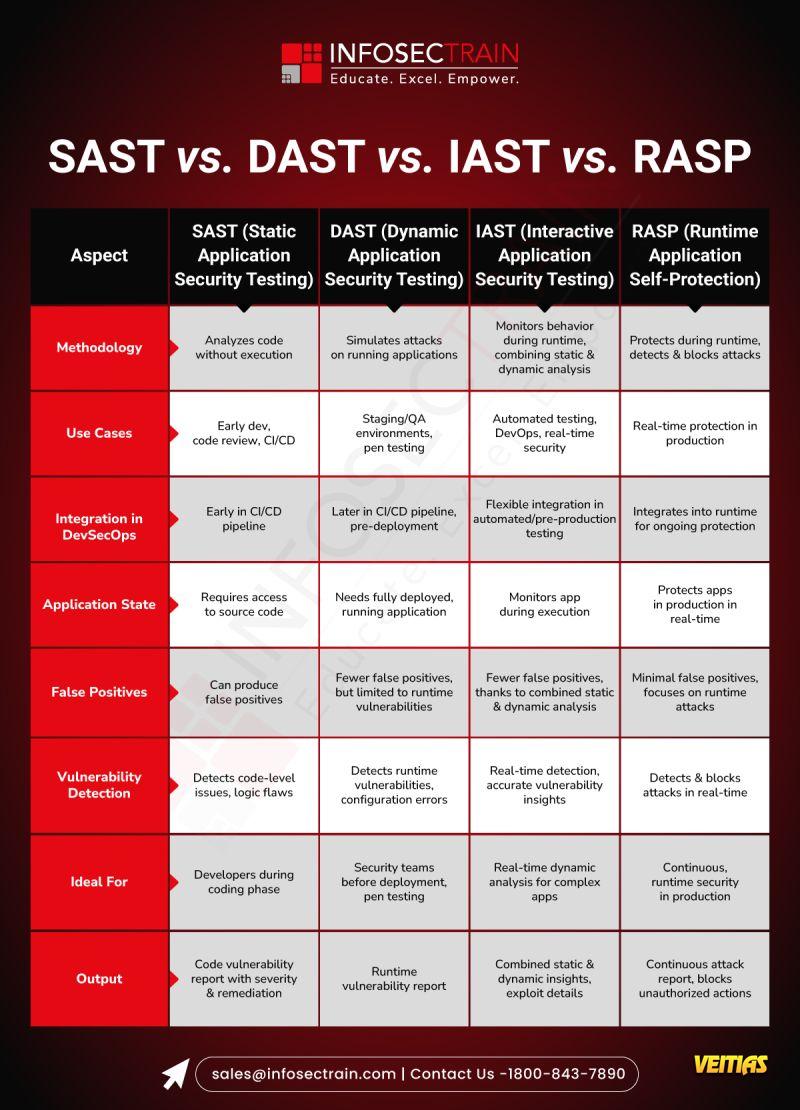
SAST, DAST, IAST, and RASP are application security testing methods used throughout the software lifecycle. SAST (Static Application Security Testing) analyzes code before it runs to find vulnerabilities, while DAST (Dynamic Application Security Testing) tests a running application externally, mimicking a hacker. IAST (Interactive Application Security Testing) combines both, analyzing a running application from the inside. Lastly, RASP (Runtime Application Self-Protection) is a self-defense mechanism that protects the application from attacks in real-time, directly in the production environment.
SAST, DAST, IAST, and RASP are application security testing methods used throughout the software lifecycle. SAST (Static Application Security Testing) analyzes code before it runs to find vulnerabilities, while DAST (Dynamic Application Security Testing) tests a running application externally, mimicking a hacker. IAST (Interactive Application Security Testing) combines both, analyzing a running application from the inside. Lastly, RASP (Runtime Application Self-Protection) is a self-defense mechanism that protects the application from attacks in real-time, directly in the production environment.
0 Kommentare
0 Anteile
2496 Ansichten
0 Vorschau