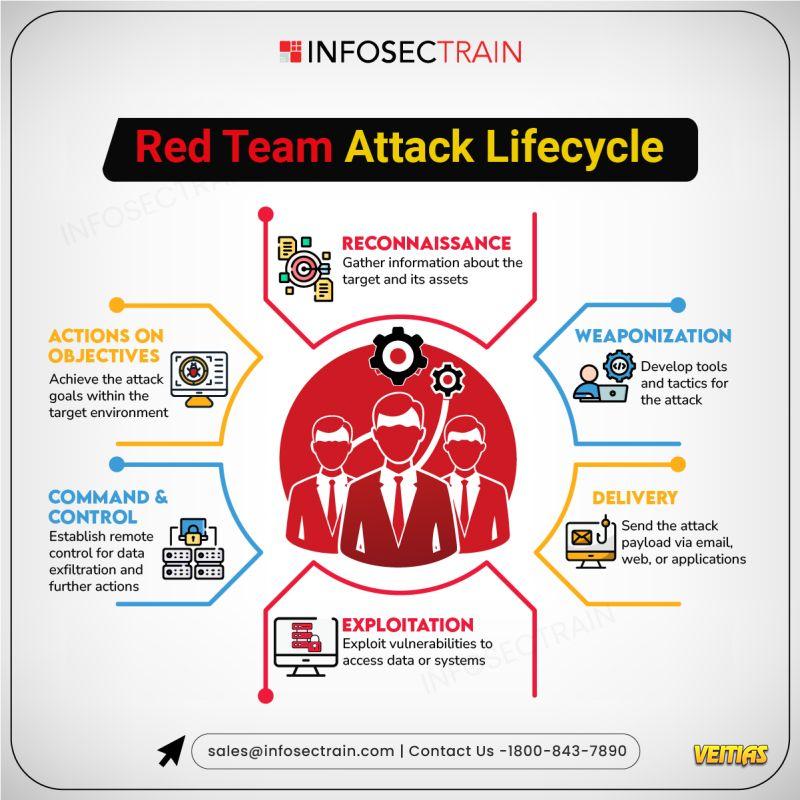
The Red Team Attack Lifecycle is a structured approach that simulates real-world cyberattacks to assess an organization’s security posture. It typically includes stages such as reconnaissance (gathering intelligence about the target), initial access (exploiting vulnerabilities to gain entry), establishing persistence (maintaining access), privilege escalation (gaining higher-level control), lateral movement (spreading within the network), and finally exfiltration or impact (stealing data or demonstrating objectives). By following this lifecycle, red teams provide organizations with valuable insights into weaknesses, helping strengthen defenses against advanced threats.
The Red Team Attack Lifecycle is a structured approach that simulates real-world cyberattacks to assess an organization’s security posture. It typically includes stages such as reconnaissance (gathering intelligence about the target), initial access (exploiting vulnerabilities to gain entry), establishing persistence (maintaining access), privilege escalation (gaining higher-level control), lateral movement (spreading within the network), and finally exfiltration or impact (stealing data or demonstrating objectives). By following this lifecycle, red teams provide organizations with valuable insights into weaknesses, helping strengthen defenses against advanced threats.
0 Comments
0 Shares
2162 Views
0 Reviews