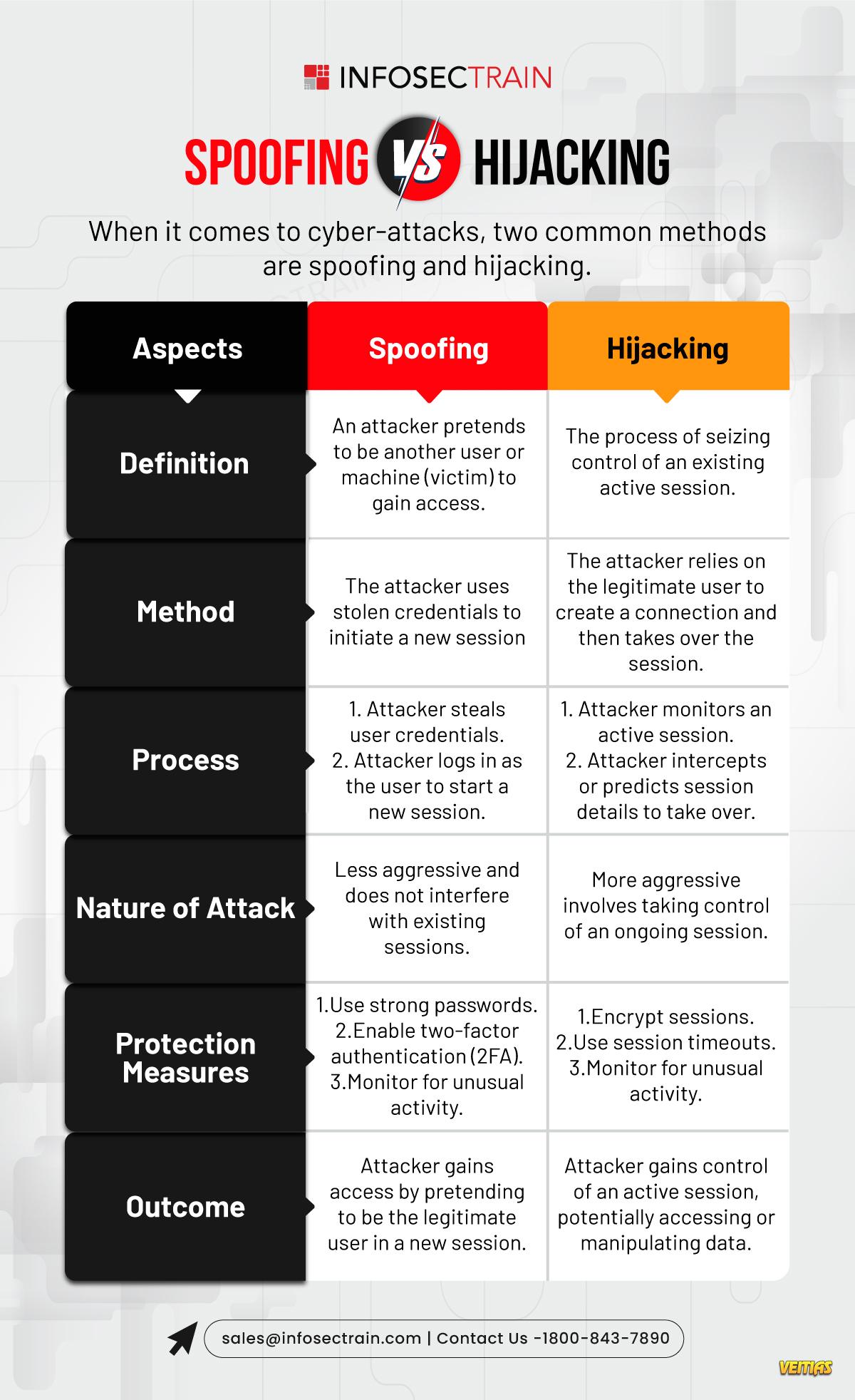
Spoofing vs. Hijacking: Know the Difference!
InfosecTrain presents a clear comparison between spoofing and hijacking to help you understand these two common cyber threats. Spoofing involves impersonating a legitimate user or device to gain unauthorized access. Common types include email spoofing, IP spoofing, and DNS spoofing, with the primary goal of deceiving users, stealing data, or spreading malware. Hijacking, on the other hand, involves taking over a legitimate session or communication channel.
https://www.infosectrain.com/
#CyberSecurity #Spoofing #Hijacking #InfoSec #DataProtection #ITSecurity #infosectrain #learntorise
InfosecTrain presents a clear comparison between spoofing and hijacking to help you understand these two common cyber threats. Spoofing involves impersonating a legitimate user or device to gain unauthorized access. Common types include email spoofing, IP spoofing, and DNS spoofing, with the primary goal of deceiving users, stealing data, or spreading malware. Hijacking, on the other hand, involves taking over a legitimate session or communication channel.
https://www.infosectrain.com/
#CyberSecurity #Spoofing #Hijacking #InfoSec #DataProtection #ITSecurity #infosectrain #learntorise
Spoofing vs. Hijacking: Know the Difference!
InfosecTrain presents a clear comparison between spoofing and hijacking to help you understand these two common cyber threats. Spoofing involves impersonating a legitimate user or device to gain unauthorized access. Common types include email spoofing, IP spoofing, and DNS spoofing, with the primary goal of deceiving users, stealing data, or spreading malware. Hijacking, on the other hand, involves taking over a legitimate session or communication channel.
https://www.infosectrain.com/
#CyberSecurity #Spoofing #Hijacking #InfoSec #DataProtection #ITSecurity #infosectrain #learntorise
0 Comments
0 Shares
2081 Views
0 Reviews