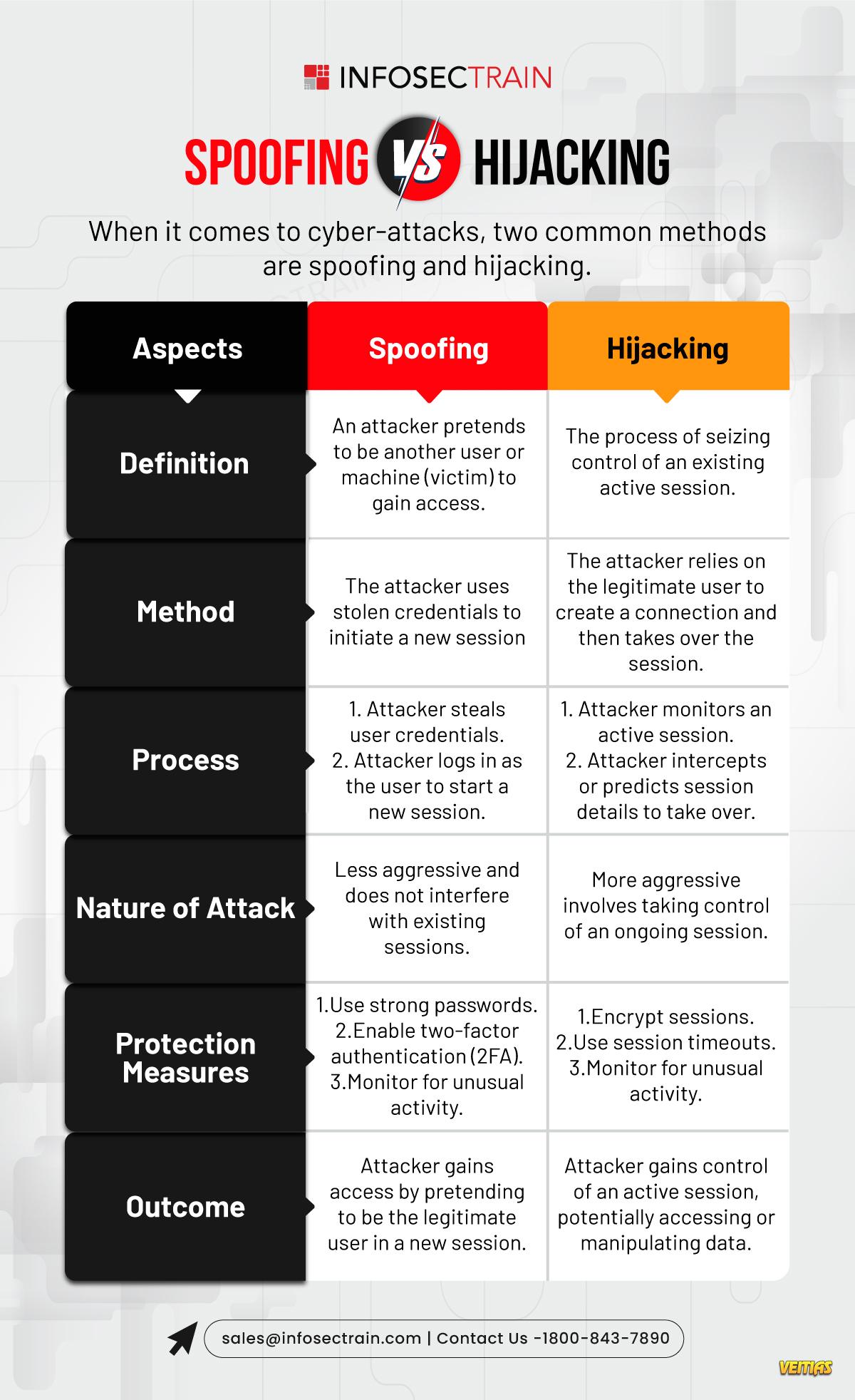
Introduction to CEH Module 11: Session Hijacking
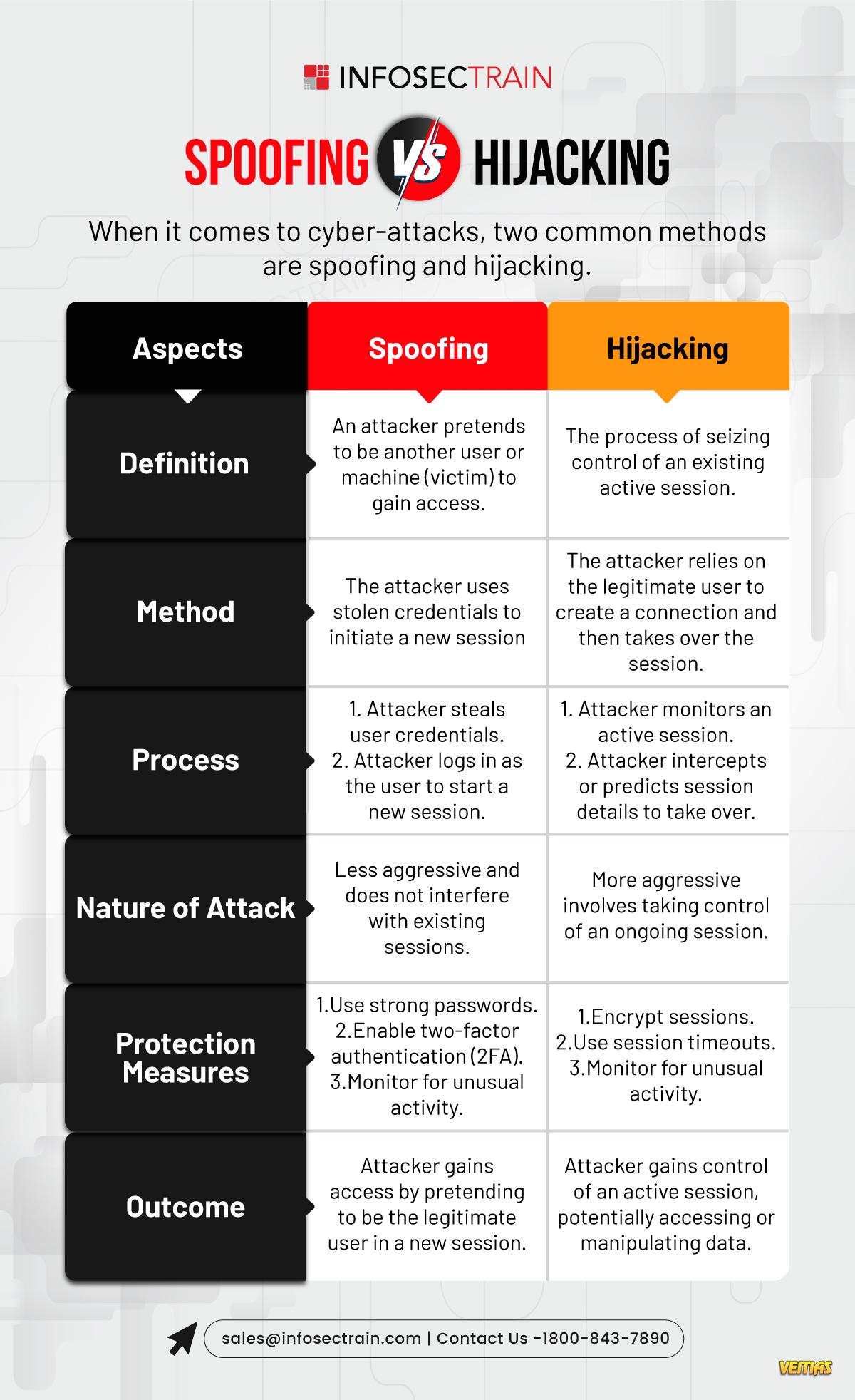
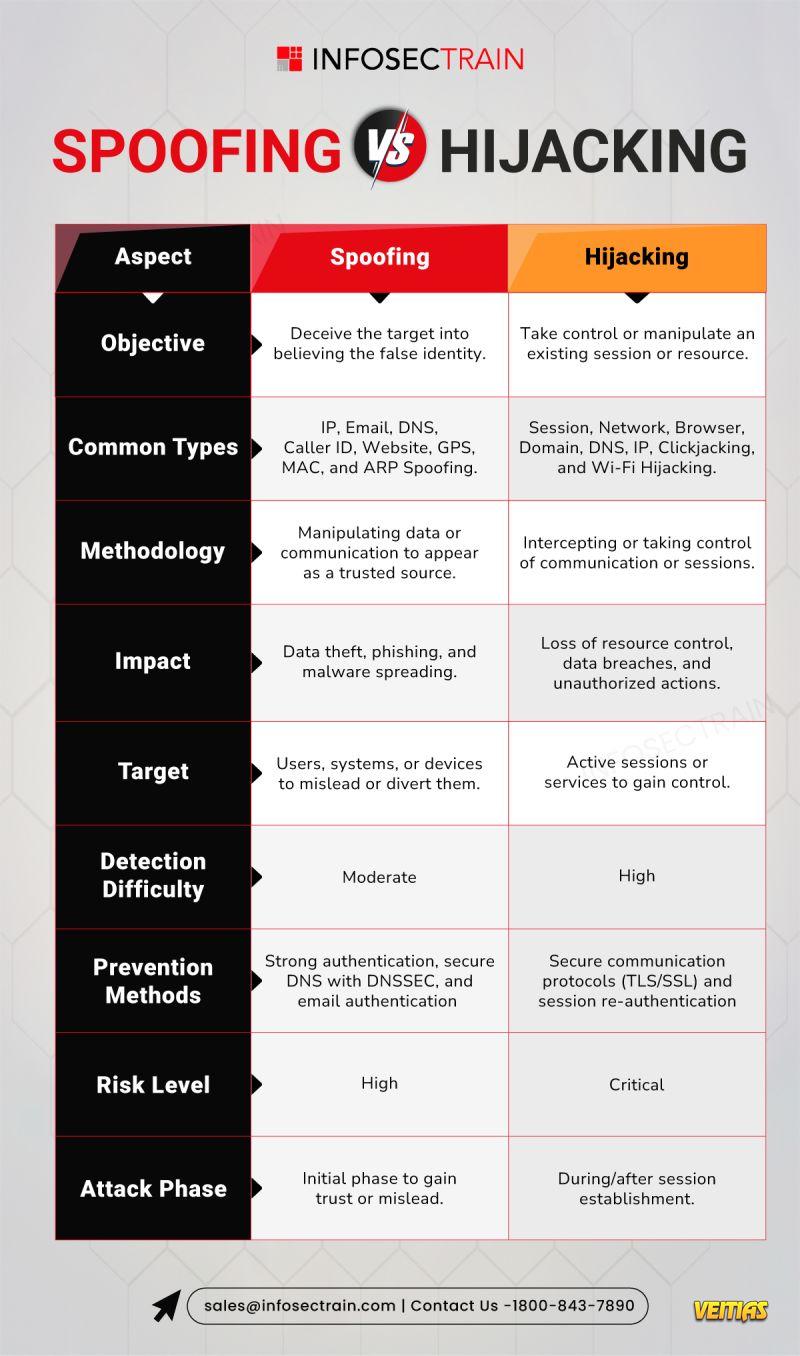
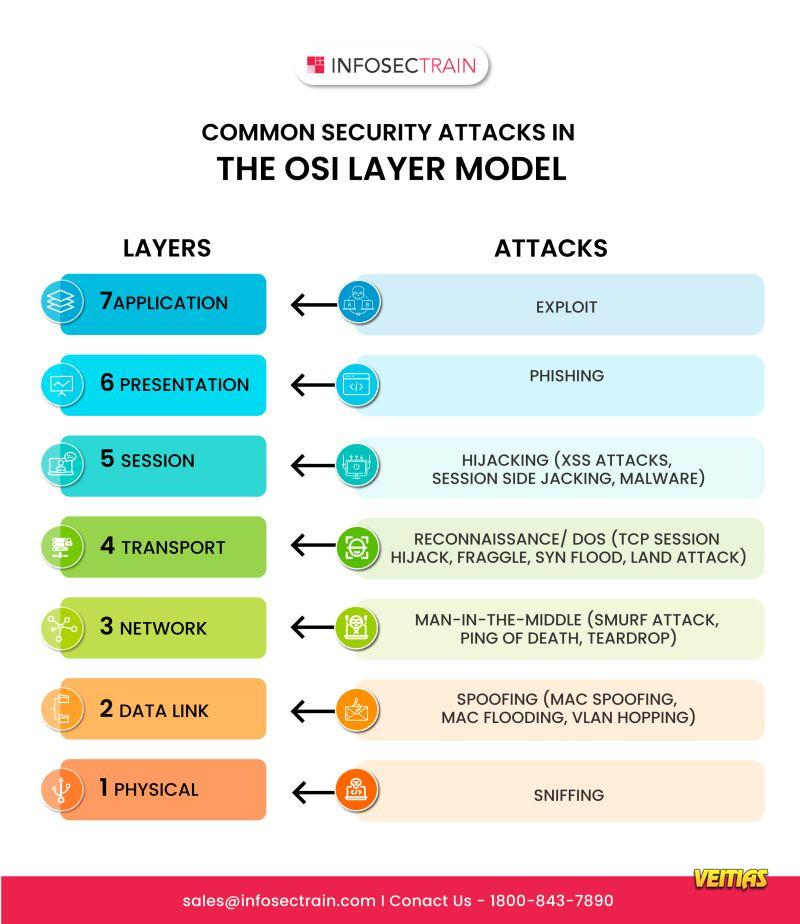
Session hijacking, a critical concern in cybersecurity, involves intercepting and exploiting authenticated sessions between clients and servers.
Read Here: https://www.infosectrain.com/blog/introduction-to-ceh-module-11-session-hijacking/
Understanding session hijacking is crucial for protecting web applications and maintaining secure user sessions.
#CEH #Cybersecurity #SessionHijacking #InfoSec #WebSecurity #NetworkSecurity #CyberDefense #infosectrain
Session hijacking, a critical concern in cybersecurity, involves intercepting and exploiting authenticated sessions between clients and servers.
Read Here: https://www.infosectrain.com/blog/introduction-to-ceh-module-11-session-hijacking/
Understanding session hijacking is crucial for protecting web applications and maintaining secure user sessions.
#CEH #Cybersecurity #SessionHijacking #InfoSec #WebSecurity #NetworkSecurity #CyberDefense #infosectrain
Introduction to CEH Module 11: Session Hijacking
Session hijacking, a critical concern in cybersecurity, involves intercepting and exploiting authenticated sessions between clients and servers.
Read Here: https://www.infosectrain.com/blog/introduction-to-ceh-module-11-session-hijacking/
Understanding session hijacking is crucial for protecting web applications and maintaining secure user sessions.
#CEH #Cybersecurity #SessionHijacking #InfoSec #WebSecurity #NetworkSecurity #CyberDefense #infosectrain
0 Comments
0 Shares
1417 Views
0 Reviews