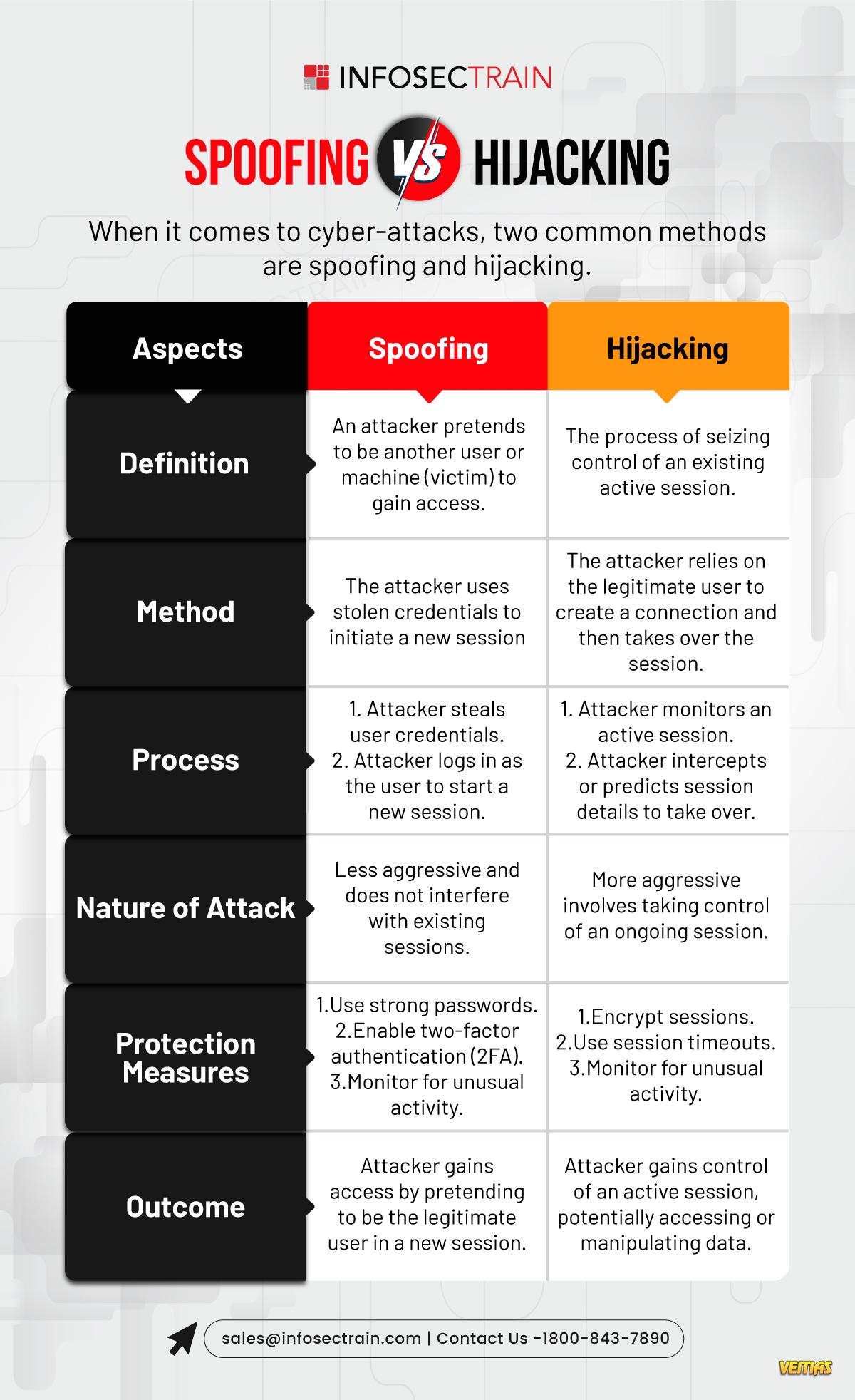
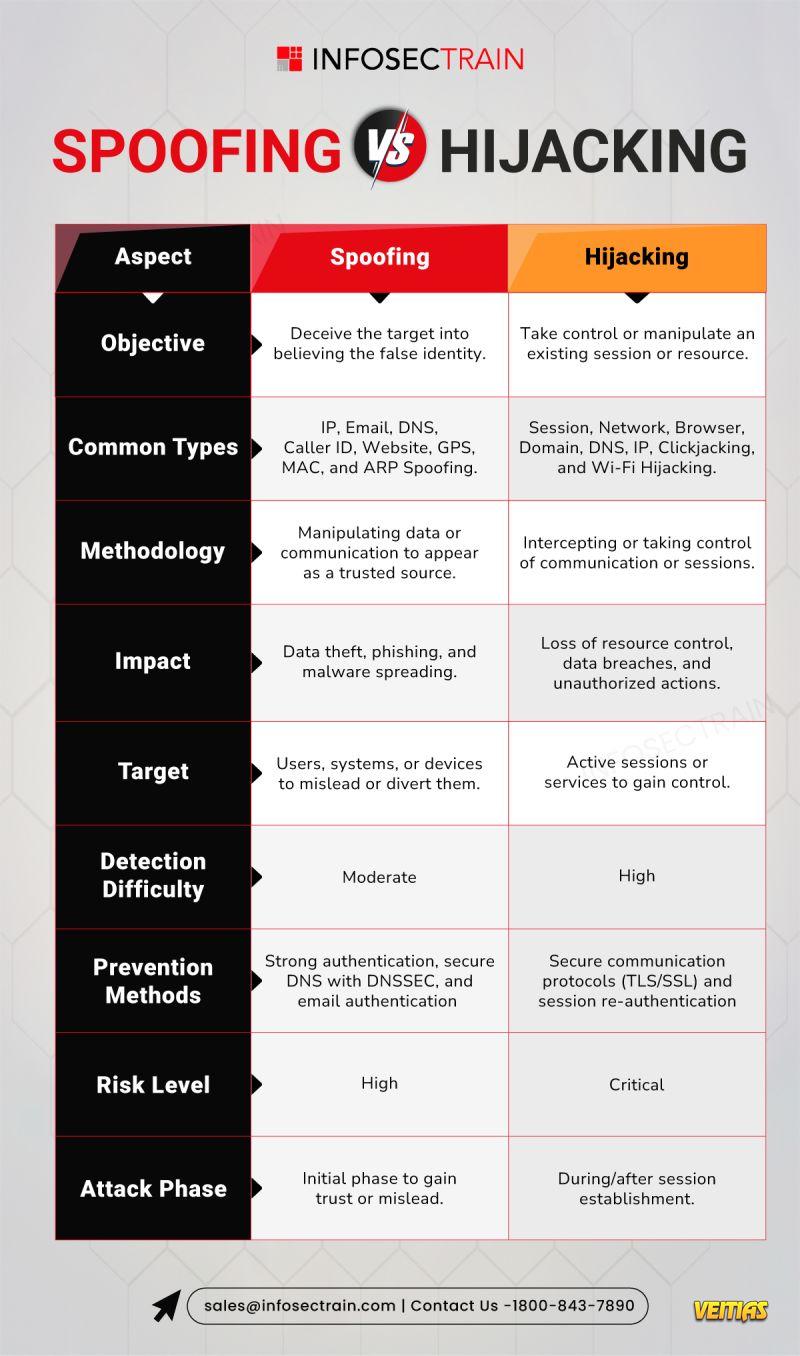
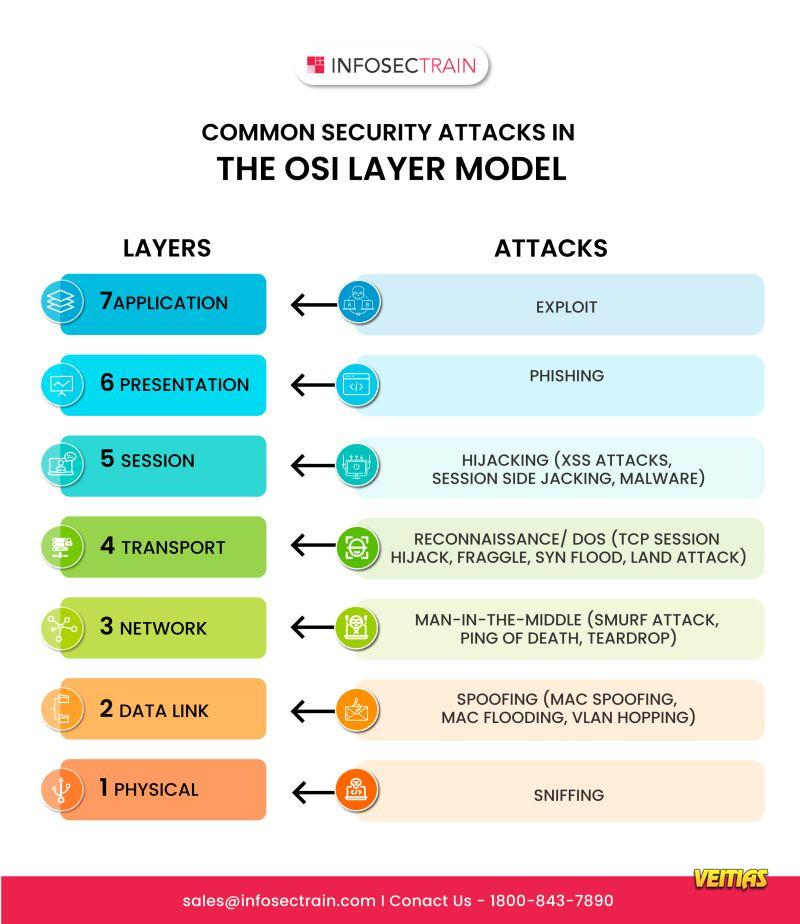
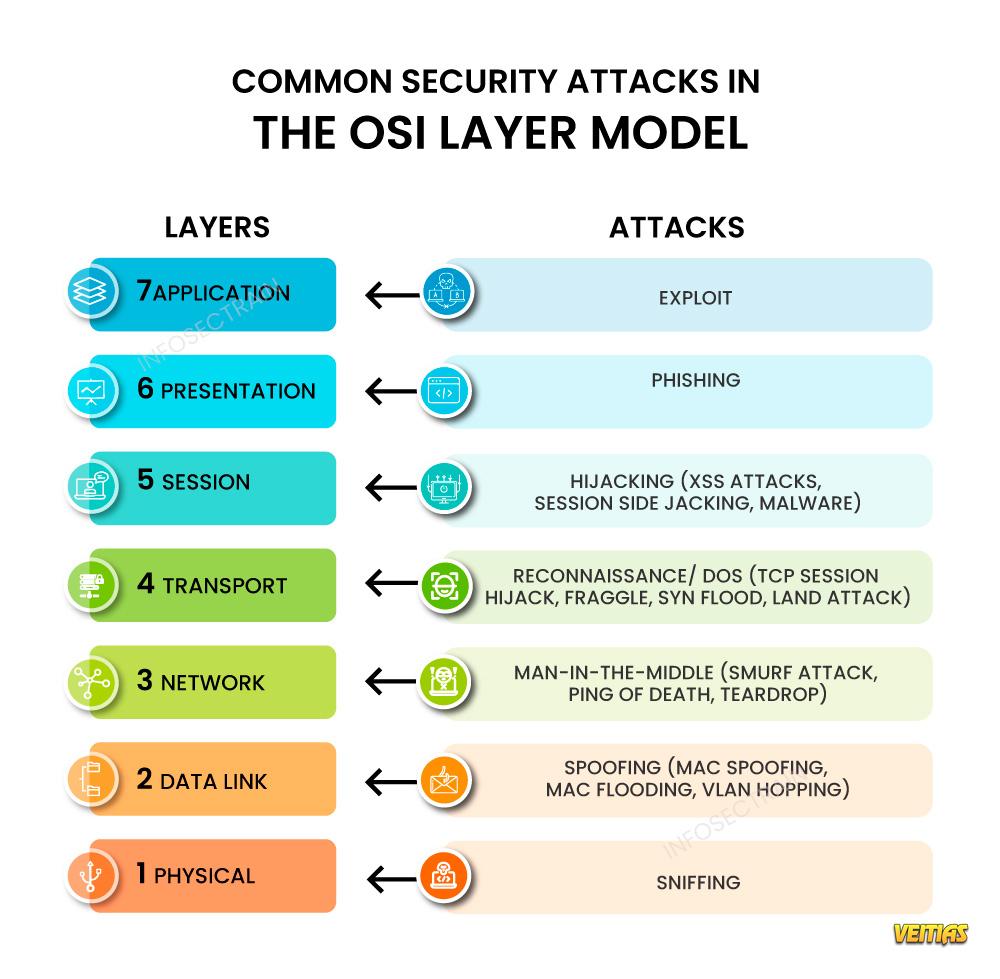
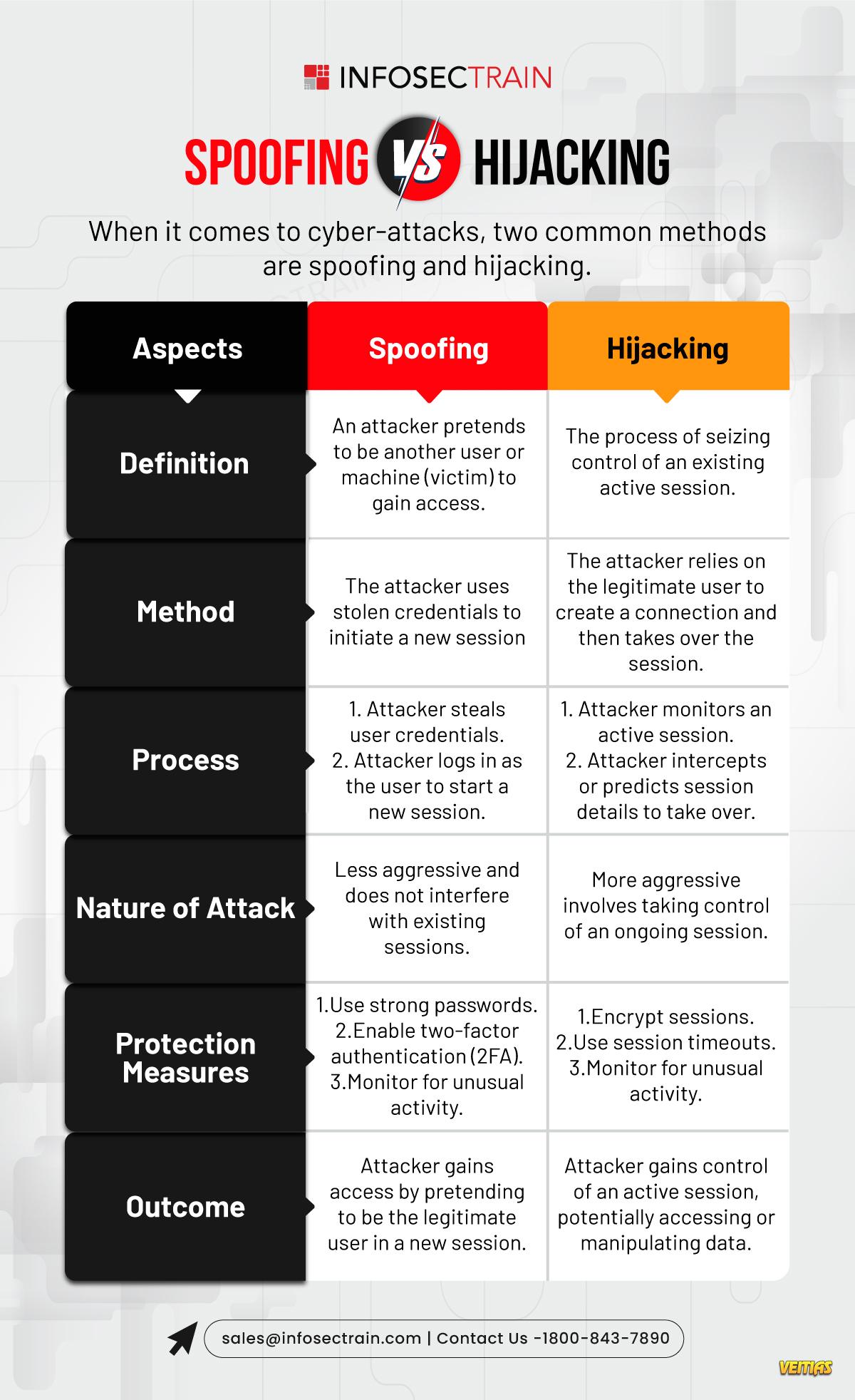
Spoofing vs. Hijacking - Know the Difference!
Confused between spoofing and hijacking? Spoofing involves pretending to be a trusted entity to deceive victims, often targeting credentials or sensitive data. Hijacking, on the other hand, takes over a legitimate session or connection to gain unauthorized access. Learn how these cyberattacks differ, their real-world implications, and the best strategies to prevent them with InfosecTrain. Stay ahead in cybersecurity with us!
More Info: - https://www.infosectrain.com/
#SpoofingVsHijacking #CyberSecurity #InfosecTrain #ThreatDetection #NetworkSecurity #CyberAttacks #InformationSecurity #SecurityTraining #OnlineThreats #CyberSecurityAwareness
Confused between spoofing and hijacking? Spoofing involves pretending to be a trusted entity to deceive victims, often targeting credentials or sensitive data. Hijacking, on the other hand, takes over a legitimate session or connection to gain unauthorized access. Learn how these cyberattacks differ, their real-world implications, and the best strategies to prevent them with InfosecTrain. Stay ahead in cybersecurity with us!
More Info: - https://www.infosectrain.com/
#SpoofingVsHijacking #CyberSecurity #InfosecTrain #ThreatDetection #NetworkSecurity #CyberAttacks #InformationSecurity #SecurityTraining #OnlineThreats #CyberSecurityAwareness
Spoofing vs. Hijacking - Know the Difference!
Confused between spoofing and hijacking? Spoofing involves pretending to be a trusted entity to deceive victims, often targeting credentials or sensitive data. Hijacking, on the other hand, takes over a legitimate session or connection to gain unauthorized access. Learn how these cyberattacks differ, their real-world implications, and the best strategies to prevent them with InfosecTrain. Stay ahead in cybersecurity with us!
More Info: - https://www.infosectrain.com/
#SpoofingVsHijacking #CyberSecurity #InfosecTrain #ThreatDetection #NetworkSecurity #CyberAttacks #InformationSecurity #SecurityTraining #OnlineThreats #CyberSecurityAwareness
0 Комментарии
0 Поделились
1058 Просмотры
0 предпросмотр