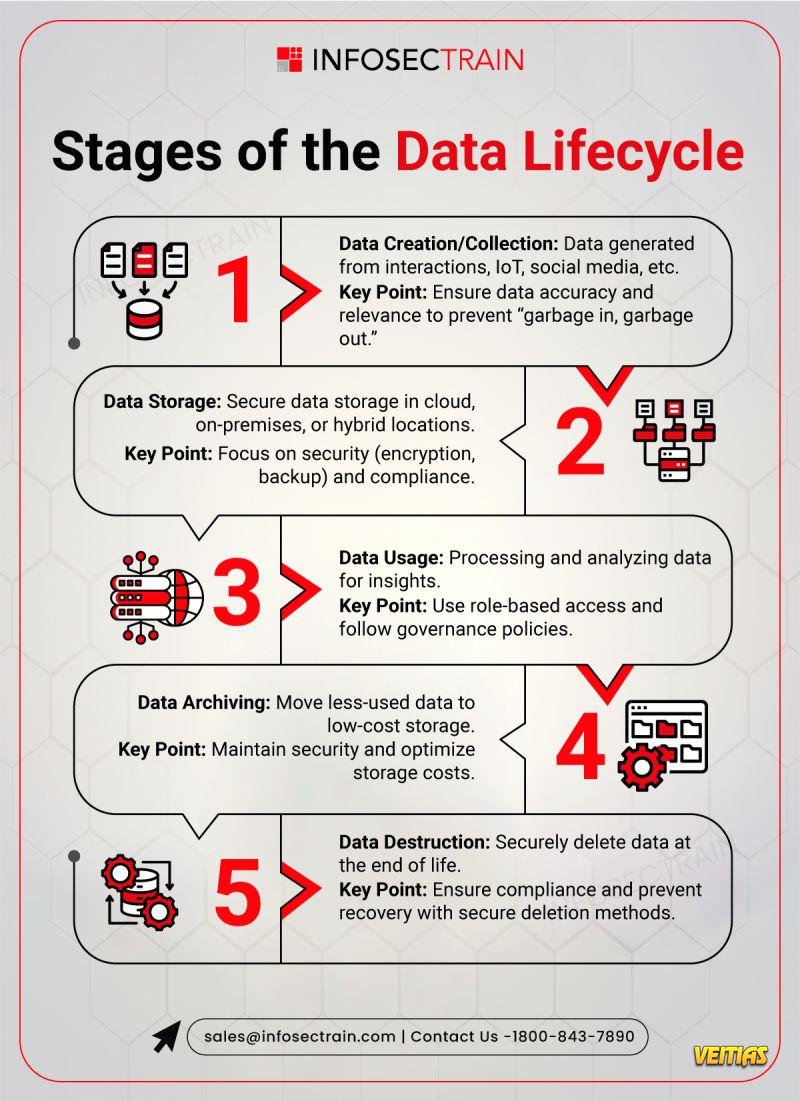
Data is a valuable asset that goes through various stages. Understanding each phase ensures better data management, security, and compliance. Here’s your quick guide!
1 . Data Creation/Collection
Data is generated from various sources like user interactions, IoT devices, social media, etc.
Key Point: Ensure hashtag#accuracy and hashtag#relevance to avoid “garbage in, garbage out.”
2 . Data Storage
Data is stored in hashtag#cloud, hashtag#on-premises , or hashtag#hybrid environments.
Key Point: Prioritize hashtag#security (encryption, backups) and ensure hashtag#compliance with regulations.
3. Data Usage
Data is processed and analyzed to extract valuable insights.
Key Point : Implement hashtag#rolebasedaccess and enforce hashtag#governancepolicies for secure use.
1 . Data Creation/Collection
Data is generated from various sources like user interactions, IoT devices, social media, etc.
Key Point: Ensure hashtag#accuracy and hashtag#relevance to avoid “garbage in, garbage out.”
2 . Data Storage
Data is stored in hashtag#cloud, hashtag#on-premises , or hashtag#hybrid environments.
Key Point: Prioritize hashtag#security (encryption, backups) and ensure hashtag#compliance with regulations.
3. Data Usage
Data is processed and analyzed to extract valuable insights.
Key Point : Implement hashtag#rolebasedaccess and enforce hashtag#governancepolicies for secure use.
Data is a valuable asset that goes through various stages. Understanding each phase ensures better data management, security, and compliance. Here’s your quick guide! 👇
1 . Data Creation/Collection
Data is generated from various sources like user interactions, IoT devices, social media, etc.
Key Point: Ensure hashtag#accuracy and hashtag#relevance to avoid “garbage in, garbage out.” 📊
2 . Data Storage
Data is stored in hashtag#cloud, hashtag#on-premises , or hashtag#hybrid environments.
Key Point: Prioritize hashtag#security (encryption, backups) and ensure hashtag#compliance with regulations. 🛡️
3. Data Usage
Data is processed and analyzed to extract valuable insights.
Key Point : Implement hashtag#rolebasedaccess and enforce hashtag#governancepolicies for secure use. 🔍
0 Comentários
0 Compartilhamentos
8392 Visualizações
0 Anterior