Free webinar on "AI-Powered Spreadsheet Skills: Get Smarter with Data"
Date: 08 Nov (Sat)
Time: 7:00 – 08:00 PM (IST)
Format: Free Masterclass + Live Q&A
Agenda for the Masterclass
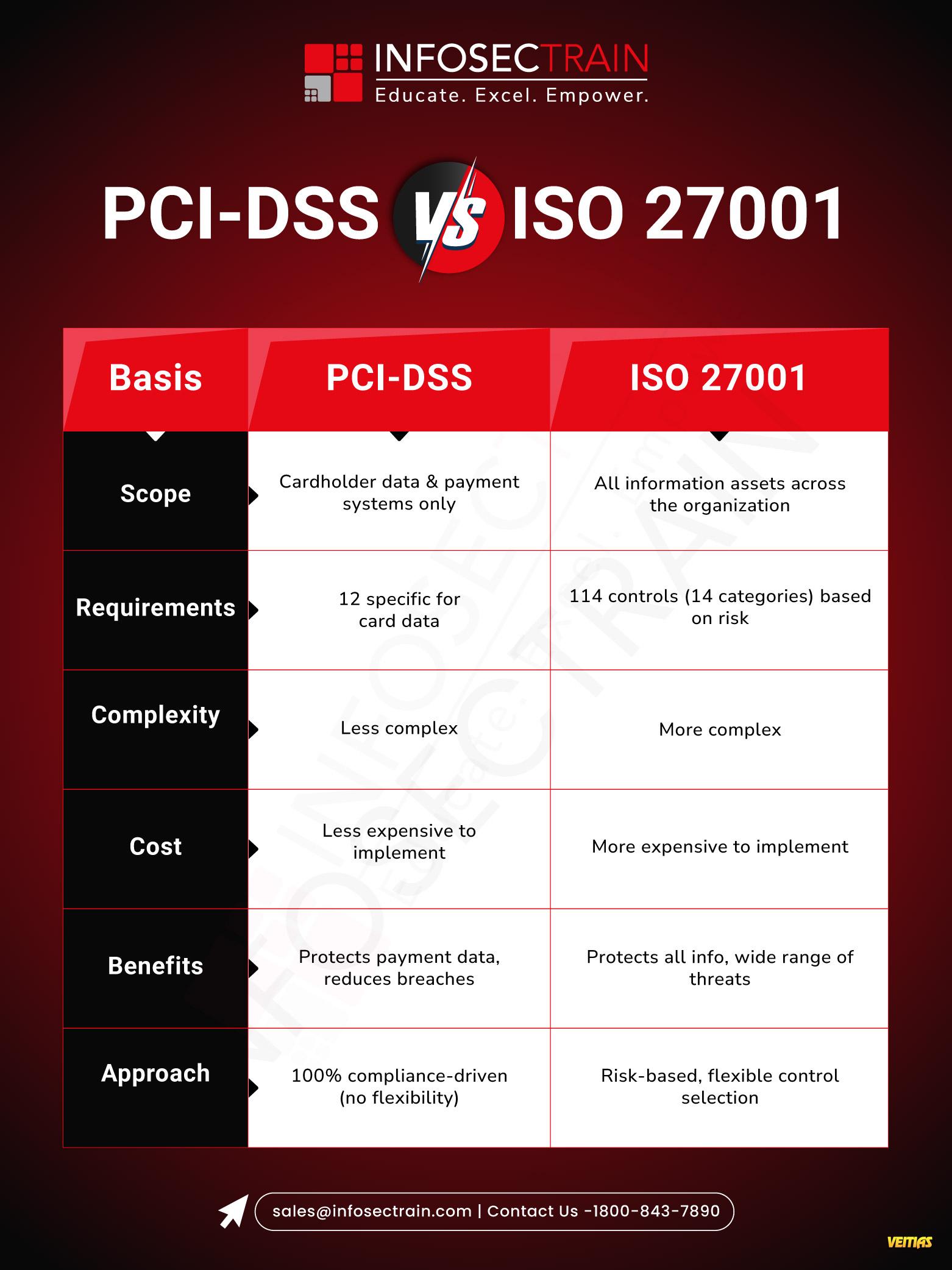
Quick tour of the Spreadsheet Workspace (Cells, Rows, Columns).
Core Skill #1: Essential Formulas & Functions
Core Skill #2: Organizing Your Data
Introducing Your AI Assistant: Finding and using AI tools in your spreadsheet.
What AI features are in Excel & Google Sheets?
AI in Action: Using plain English to generate formulas, clean messy data, and create instant charts.
Instant Analysis & Charts
Automated Data Cleaning
How AI recognizes patterns and understands plain language.
Interactive Q & A
Speaker: Anas Hamid
Why Attend?
• Get CPE Certificate
• FREE Career Guidance & Mentorship
• Learn from Industry Experts
Seats are limited — Register for FREE now!
https://www.infosectrain.com/events/ai-powered-spreadsheet-skills-get-smarter-with-data/
Date: 08 Nov (Sat)
Time: 7:00 – 08:00 PM (IST)
Format: Free Masterclass + Live Q&A
Agenda for the Masterclass
Quick tour of the Spreadsheet Workspace (Cells, Rows, Columns).
Core Skill #1: Essential Formulas & Functions
Core Skill #2: Organizing Your Data
Introducing Your AI Assistant: Finding and using AI tools in your spreadsheet.
What AI features are in Excel & Google Sheets?
AI in Action: Using plain English to generate formulas, clean messy data, and create instant charts.
Instant Analysis & Charts
Automated Data Cleaning
How AI recognizes patterns and understands plain language.
Interactive Q & A
Speaker: Anas Hamid
Why Attend?
• Get CPE Certificate
• FREE Career Guidance & Mentorship
• Learn from Industry Experts
Seats are limited — Register for FREE now!
https://www.infosectrain.com/events/ai-powered-spreadsheet-skills-get-smarter-with-data/
Free webinar on "AI-Powered Spreadsheet Skills: Get Smarter with Data"
📅 Date: 08 Nov (Sat)
🕗 Time: 7:00 – 08:00 PM (IST)
🎓 Format: Free Masterclass + Live Q&A
Agenda for the Masterclass
👉 Quick tour of the Spreadsheet Workspace (Cells, Rows, Columns).
👉 Core Skill #1: Essential Formulas & Functions
👉 Core Skill #2: Organizing Your Data
👉 Introducing Your AI Assistant: Finding and using AI tools in your spreadsheet.
👉 What AI features are in Excel & Google Sheets?
👉 AI in Action: Using plain English to generate formulas, clean messy data, and create instant charts.
👉 Instant Analysis & Charts
👉 Automated Data Cleaning
👉 How AI recognizes patterns and understands plain language.
👉 Interactive Q & A
🎤 Speaker: Anas Hamid
🔍 Why Attend?
• Get CPE Certificate
• FREE Career Guidance & Mentorship
• Learn from Industry Experts
🔗 Seats are limited — Register for FREE now!
👉 https://www.infosectrain.com/events/ai-powered-spreadsheet-skills-get-smarter-with-data/
0 Comments
0 Shares
534 Views
0 Reviews