Key Components of Identity and Access Management (IAM) in Cloud Security
In today’s cloud-first world, protecting access to sensitive data is more crucial than ever. Here's a breakdown of the key IAM components that safeguard your cloud environment:
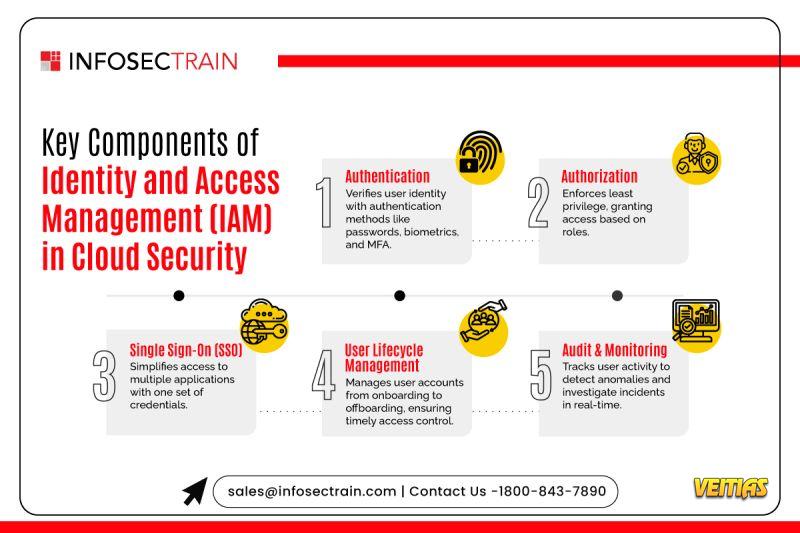
Authentication: Verifies the identity of users through methods like passwords, biometrics, and Multi-Factor Authentication (MFA).
Authorization: Ensures that users only access what they’re authorized to, enforcing the principle of least privilege. 🛡
Single Sign-On (SSO): Simplifies the user experience by allowing access to multiple applications with just one set of credentials.
User Lifecycle Management: Manages user accounts from onboarding to offboarding, ensuring proper access controls at every stage.
Audit & Monitoring: Tracks user activity and monitors for suspicious behavior, helping to detect and respond to security incidents in real-time.
By strengthening your IAM practices, you can ensure secure, efficient, and seamless access to your cloud resources.
#CloudSecurity #IAM #CyberSecurity #MFA #SSO #Authorization #AuditAndMonitoring #ZeroTrust #CloudComputing #infosectrain #learntorise
In today’s cloud-first world, protecting access to sensitive data is more crucial than ever. Here's a breakdown of the key IAM components that safeguard your cloud environment:
Authentication: Verifies the identity of users through methods like passwords, biometrics, and Multi-Factor Authentication (MFA).
Authorization: Ensures that users only access what they’re authorized to, enforcing the principle of least privilege. 🛡
Single Sign-On (SSO): Simplifies the user experience by allowing access to multiple applications with just one set of credentials.
User Lifecycle Management: Manages user accounts from onboarding to offboarding, ensuring proper access controls at every stage.
Audit & Monitoring: Tracks user activity and monitors for suspicious behavior, helping to detect and respond to security incidents in real-time.
By strengthening your IAM practices, you can ensure secure, efficient, and seamless access to your cloud resources.
#CloudSecurity #IAM #CyberSecurity #MFA #SSO #Authorization #AuditAndMonitoring #ZeroTrust #CloudComputing #infosectrain #learntorise
Key Components of Identity and Access Management (IAM) in Cloud Security ☁️🔐
In today’s cloud-first world, protecting access to sensitive data is more crucial than ever. Here's a breakdown of the key IAM components that safeguard your cloud environment:
Authentication: Verifies the identity of users through methods like passwords, biometrics, and Multi-Factor Authentication (MFA). 🔑
Authorization: Ensures that users only access what they’re authorized to, enforcing the principle of least privilege. 🛡
Single Sign-On (SSO): Simplifies the user experience by allowing access to multiple applications with just one set of credentials. 🔄
User Lifecycle Management: Manages user accounts from onboarding to offboarding, ensuring proper access controls at every stage. 🔄👤
Audit & Monitoring: Tracks user activity and monitors for suspicious behavior, helping to detect and respond to security incidents in real-time. 📊🔍
💡 By strengthening your IAM practices, you can ensure secure, efficient, and seamless access to your cloud resources.
#CloudSecurity #IAM #CyberSecurity #MFA #SSO #Authorization #AuditAndMonitoring #ZeroTrust #CloudComputing #infosectrain #learntorise
0 Commentarii
0 Distribuiri
580 Views
0 previzualizare