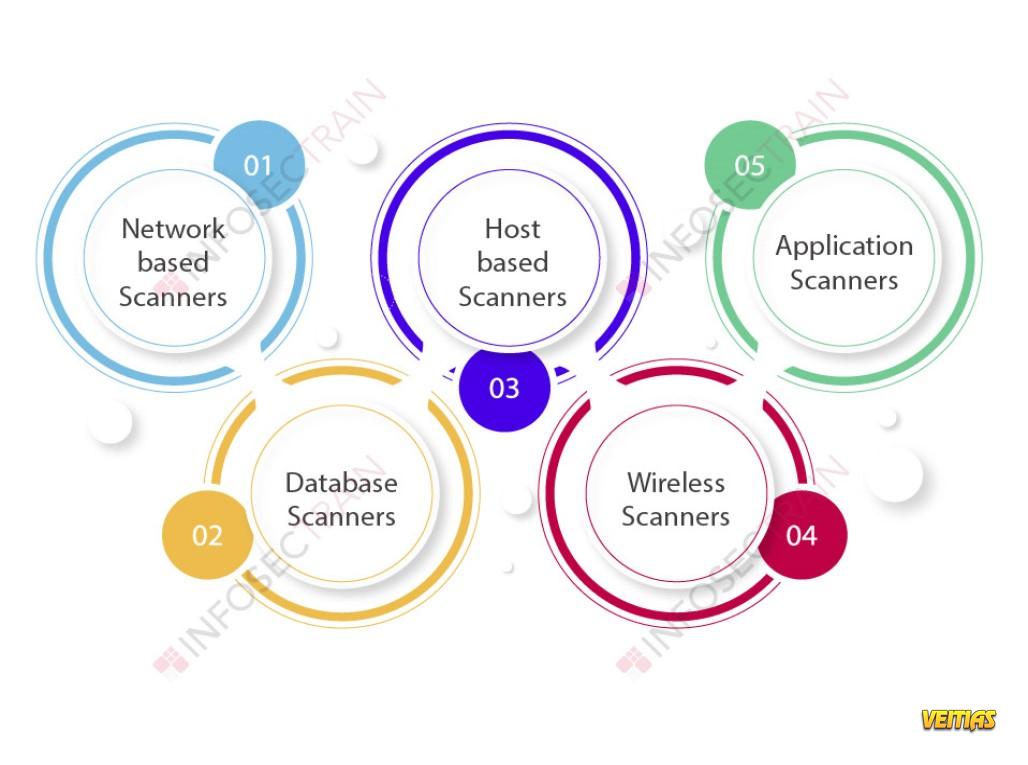
Types of Network Scanning for Ethical Hacking
In the world of cybersecurity, ethical hacking plays a crucial role in identifying vulnerabilities and securing systems from potential threats. One of the key techniques used in ethical hacking is network scanning, which involves probing a network to discover active hosts, open ports, and services running on those ports. Understanding the different types of network scanning is essential for ethical hackers to conduct thorough security assessments and protect sensitive information from cyber attacks.
Read Here: https://medium.com/@Infosec-Train/types-of-network-scanning-for-ethical-hacking-254de2876091
#NetworkScanningMethods #EthicalHackingTechniques #CybersecurityScans #NetworkSecurity #EthicalHacking101 #NetworkVulnerability #InfoSecScanning #HackersToolkit #PenetrationTesting #SecurityAssessment #CyberDefense #infosectrain #learntorise
In the world of cybersecurity, ethical hacking plays a crucial role in identifying vulnerabilities and securing systems from potential threats. One of the key techniques used in ethical hacking is network scanning, which involves probing a network to discover active hosts, open ports, and services running on those ports. Understanding the different types of network scanning is essential for ethical hackers to conduct thorough security assessments and protect sensitive information from cyber attacks.
Read Here: https://medium.com/@Infosec-Train/types-of-network-scanning-for-ethical-hacking-254de2876091
#NetworkScanningMethods #EthicalHackingTechniques #CybersecurityScans #NetworkSecurity #EthicalHacking101 #NetworkVulnerability #InfoSecScanning #HackersToolkit #PenetrationTesting #SecurityAssessment #CyberDefense #infosectrain #learntorise
Types of Network Scanning for Ethical Hacking
In the world of cybersecurity, ethical hacking plays a crucial role in identifying vulnerabilities and securing systems from potential threats. One of the key techniques used in ethical hacking is network scanning, which involves probing a network to discover active hosts, open ports, and services running on those ports. Understanding the different types of network scanning is essential for ethical hackers to conduct thorough security assessments and protect sensitive information from cyber attacks.
Read Here: https://medium.com/@Infosec-Train/types-of-network-scanning-for-ethical-hacking-254de2876091
#NetworkScanningMethods #EthicalHackingTechniques #CybersecurityScans #NetworkSecurity #EthicalHacking101 #NetworkVulnerability #InfoSecScanning #HackersToolkit #PenetrationTesting #SecurityAssessment #CyberDefense #infosectrain #learntorise
0 Commentarii
0 Distribuiri
14882 Views
0 previzualizare