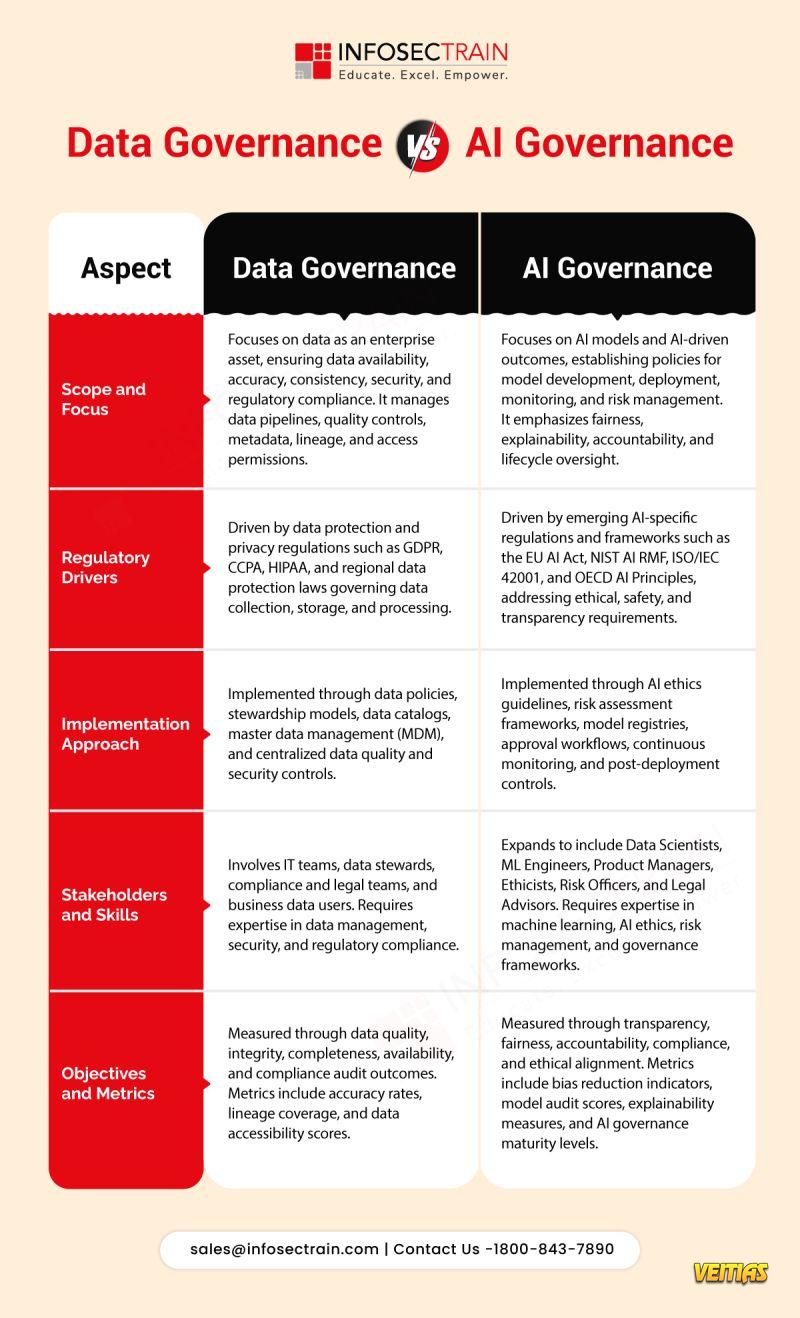
AI governance is no longer optional. InfosecTrain’s 𝗜𝗦𝗢/𝗜𝗘𝗖 𝟰𝟮𝟬𝟬𝟭 𝗟𝗲𝗮𝗱 𝗜𝗺𝗽𝗹𝗲𝗺𝗲𝗻𝘁𝗲𝗿 𝗧𝗿𝗮𝗶𝗻𝗶𝗻𝗴 is a hands-on, expert-led program designed to help professionals implement, manage, and audit 𝗔𝗜 𝗠𝗮𝗻𝗮𝗴𝗲𝗺𝗲𝗻𝘁 𝗦𝘆𝘀𝘁𝗲𝗺𝘀 (𝗔𝗜𝗠𝗦) aligned with the world’s first AI governance standard.
This program goes beyond theory - focusing on end-to-end implementation, real AI use cases, and practical readiness for organizational adoption.
Instructor: Prabh Nair (18+ years of industry experience) The training blends governance, risk, compliance, and AI expertise into a job-ready learning experience.
This program goes beyond theory - focusing on end-to-end implementation, real AI use cases, and practical readiness for organizational adoption.
Instructor: Prabh Nair (18+ years of industry experience) The training blends governance, risk, compliance, and AI expertise into a job-ready learning experience.
AI governance is no longer optional. InfosecTrain’s 𝗜𝗦𝗢/𝗜𝗘𝗖 𝟰𝟮𝟬𝟬𝟭 𝗟𝗲𝗮𝗱 𝗜𝗺𝗽𝗹𝗲𝗺𝗲𝗻𝘁𝗲𝗿 𝗧𝗿𝗮𝗶𝗻𝗶𝗻𝗴 is a hands-on, expert-led program designed to help professionals implement, manage, and audit 𝗔𝗜 𝗠𝗮𝗻𝗮𝗴𝗲𝗺𝗲𝗻𝘁 𝗦𝘆𝘀𝘁𝗲𝗺𝘀 (𝗔𝗜𝗠𝗦) aligned with the world’s first AI governance standard.
This program goes beyond theory - focusing on end-to-end implementation, real AI use cases, and practical readiness for organizational adoption.
👨🏫 Instructor: Prabh Nair (18+ years of industry experience) The training blends governance, risk, compliance, and AI expertise into a job-ready learning experience.
0 Commenti
0 condivisioni
526 Views
0 Anteprima