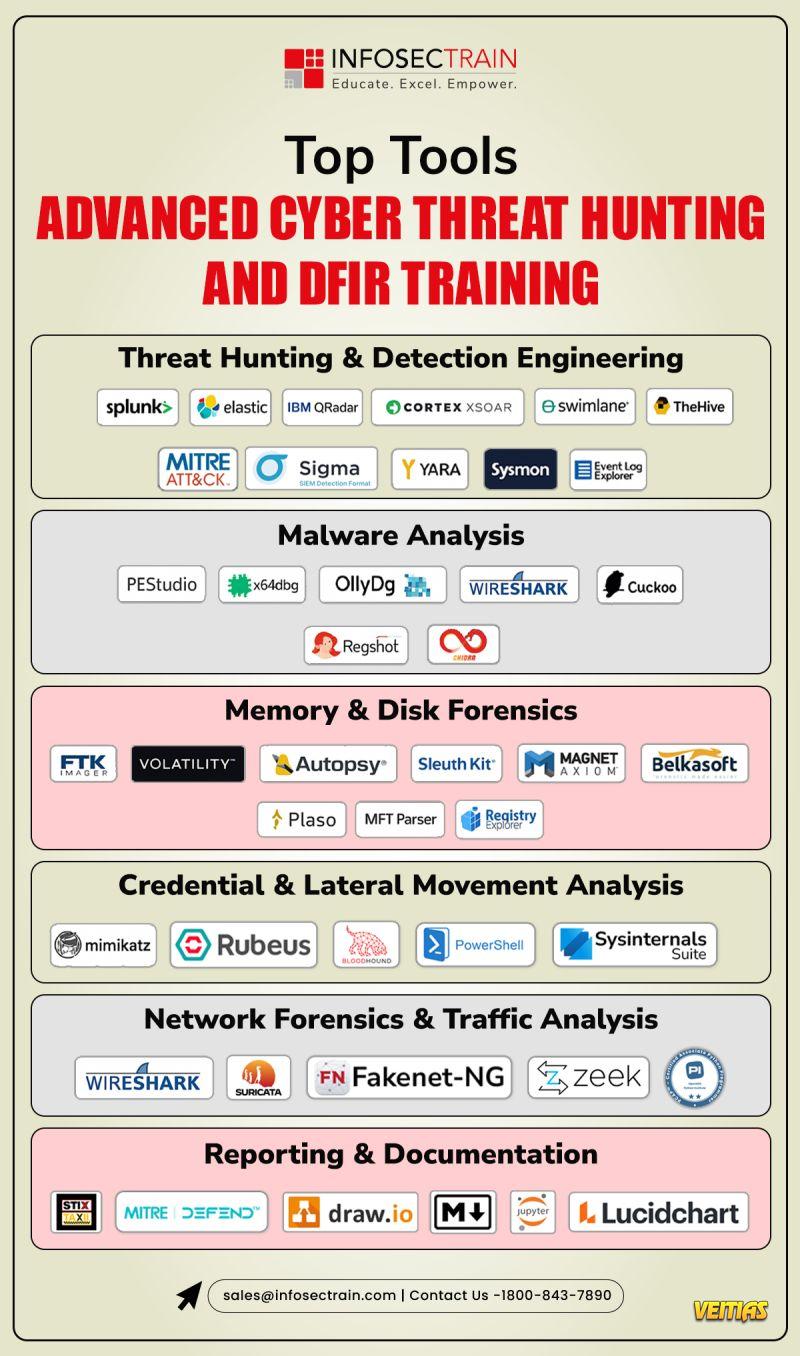
𝐇𝐨𝐰 𝐭𝐨 𝐔𝐬𝐞 𝐃𝐚𝐭𝐚 𝐒𝐨𝐮𝐫𝐜𝐞𝐬 𝐭𝐨 𝐒𝐮𝐩𝐩𝐨𝐫𝐭 𝐚𝐧 𝐈𝐧𝐯𝐞𝐬𝐭𝐢𝐠𝐚𝐭𝐢𝐨𝐧?
Have you ever seen a detective put together clues to figure out a mystery?
That is exactly what 𝐜𝐲𝐛𝐞𝐫 𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐩𝐫𝐨𝐟𝐞𝐬𝐬𝐢𝐨𝐧𝐚𝐥𝐬 𝐝𝐨 aside from fingerprints and videos (CCTV), 𝐭𝐡𝐞 𝐜𝐥𝐮𝐞𝐬 𝐚𝐫𝐞 𝐥𝐨𝐠 𝐝𝐚𝐭𝐚, 𝐯𝐮𝐥𝐧𝐞𝐫𝐚𝐛𝐢𝐥𝐢𝐭𝐲 𝐬𝐜𝐚𝐧𝐬, 𝐚𝐧𝐝 𝐩𝐚𝐜𝐤𝐞𝐭 𝐜𝐚𝐩𝐭𝐮𝐫𝐞𝐬.
Every click, every login attempt, every firewall alert points to a bigger context.
Log data from firewalls, applications, and endpoint devices help understand what attack vectors exist.
Vulnerability scans show the weak spots before an attacker is able to take advantage of them.
Packet captures show exactly what is traversing through the network.
Just like assembling a puzzle, there are tools such as a SIEM and even file metadata that can help piece together the timing of a breach.
𝐑𝐞𝐚𝐝 𝐦𝐨𝐫𝐞: https://www.infosectrain.com/blog/how-to-use-data-sources-to-support-an-investigation/
The take away? Data is not just a series of numbers, it is the narrative of your network security. The better you can read the data, the faster you can mitigate threats.
#CyberSecurity #SecurityPlus #CompTIA #SIEM #DataDrivenSecurity #CyberThreats #BlueTeam #SOC #CyberAwareness #infosectrain
Have you ever seen a detective put together clues to figure out a mystery?
That is exactly what 𝐜𝐲𝐛𝐞𝐫 𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐩𝐫𝐨𝐟𝐞𝐬𝐬𝐢𝐨𝐧𝐚𝐥𝐬 𝐝𝐨 aside from fingerprints and videos (CCTV), 𝐭𝐡𝐞 𝐜𝐥𝐮𝐞𝐬 𝐚𝐫𝐞 𝐥𝐨𝐠 𝐝𝐚𝐭𝐚, 𝐯𝐮𝐥𝐧𝐞𝐫𝐚𝐛𝐢𝐥𝐢𝐭𝐲 𝐬𝐜𝐚𝐧𝐬, 𝐚𝐧𝐝 𝐩𝐚𝐜𝐤𝐞𝐭 𝐜𝐚𝐩𝐭𝐮𝐫𝐞𝐬.
Every click, every login attempt, every firewall alert points to a bigger context.
Log data from firewalls, applications, and endpoint devices help understand what attack vectors exist.
Vulnerability scans show the weak spots before an attacker is able to take advantage of them.
Packet captures show exactly what is traversing through the network.
Just like assembling a puzzle, there are tools such as a SIEM and even file metadata that can help piece together the timing of a breach.
𝐑𝐞𝐚𝐝 𝐦𝐨𝐫𝐞: https://www.infosectrain.com/blog/how-to-use-data-sources-to-support-an-investigation/
The take away? Data is not just a series of numbers, it is the narrative of your network security. The better you can read the data, the faster you can mitigate threats.
#CyberSecurity #SecurityPlus #CompTIA #SIEM #DataDrivenSecurity #CyberThreats #BlueTeam #SOC #CyberAwareness #infosectrain
𝐇𝐨𝐰 𝐭𝐨 𝐔𝐬𝐞 𝐃𝐚𝐭𝐚 𝐒𝐨𝐮𝐫𝐜𝐞𝐬 𝐭𝐨 𝐒𝐮𝐩𝐩𝐨𝐫𝐭 𝐚𝐧 𝐈𝐧𝐯𝐞𝐬𝐭𝐢𝐠𝐚𝐭𝐢𝐨𝐧?
Have you ever seen a detective put together clues to figure out a mystery?
That is exactly what 𝐜𝐲𝐛𝐞𝐫 𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐩𝐫𝐨𝐟𝐞𝐬𝐬𝐢𝐨𝐧𝐚𝐥𝐬 𝐝𝐨 aside from fingerprints and videos (CCTV), 𝐭𝐡𝐞 𝐜𝐥𝐮𝐞𝐬 𝐚𝐫𝐞 𝐥𝐨𝐠 𝐝𝐚𝐭𝐚, 𝐯𝐮𝐥𝐧𝐞𝐫𝐚𝐛𝐢𝐥𝐢𝐭𝐲 𝐬𝐜𝐚𝐧𝐬, 𝐚𝐧𝐝 𝐩𝐚𝐜𝐤𝐞𝐭 𝐜𝐚𝐩𝐭𝐮𝐫𝐞𝐬.
➡️Every click, every login attempt, every firewall alert points to a bigger context.
➡️ Log data from firewalls, applications, and endpoint devices help understand what attack vectors exist.
➡️ Vulnerability scans show the weak spots before an attacker is able to take advantage of them.
➡️ Packet captures show exactly what is traversing through the network.
Just like assembling a puzzle, there are tools such as a SIEM and even file metadata that can help piece together the timing of a breach.
👉 𝐑𝐞𝐚𝐝 𝐦𝐨𝐫𝐞: https://www.infosectrain.com/blog/how-to-use-data-sources-to-support-an-investigation/
✅ The take away? Data is not just a series of numbers, it is the narrative of your network security. The better you can read the data, the faster you can mitigate threats.
#CyberSecurity #SecurityPlus #CompTIA #SIEM #DataDrivenSecurity #CyberThreats #BlueTeam #SOC #CyberAwareness #infosectrain
0 Commentaires
0 Parts
2006 Vue
0 Aperçu