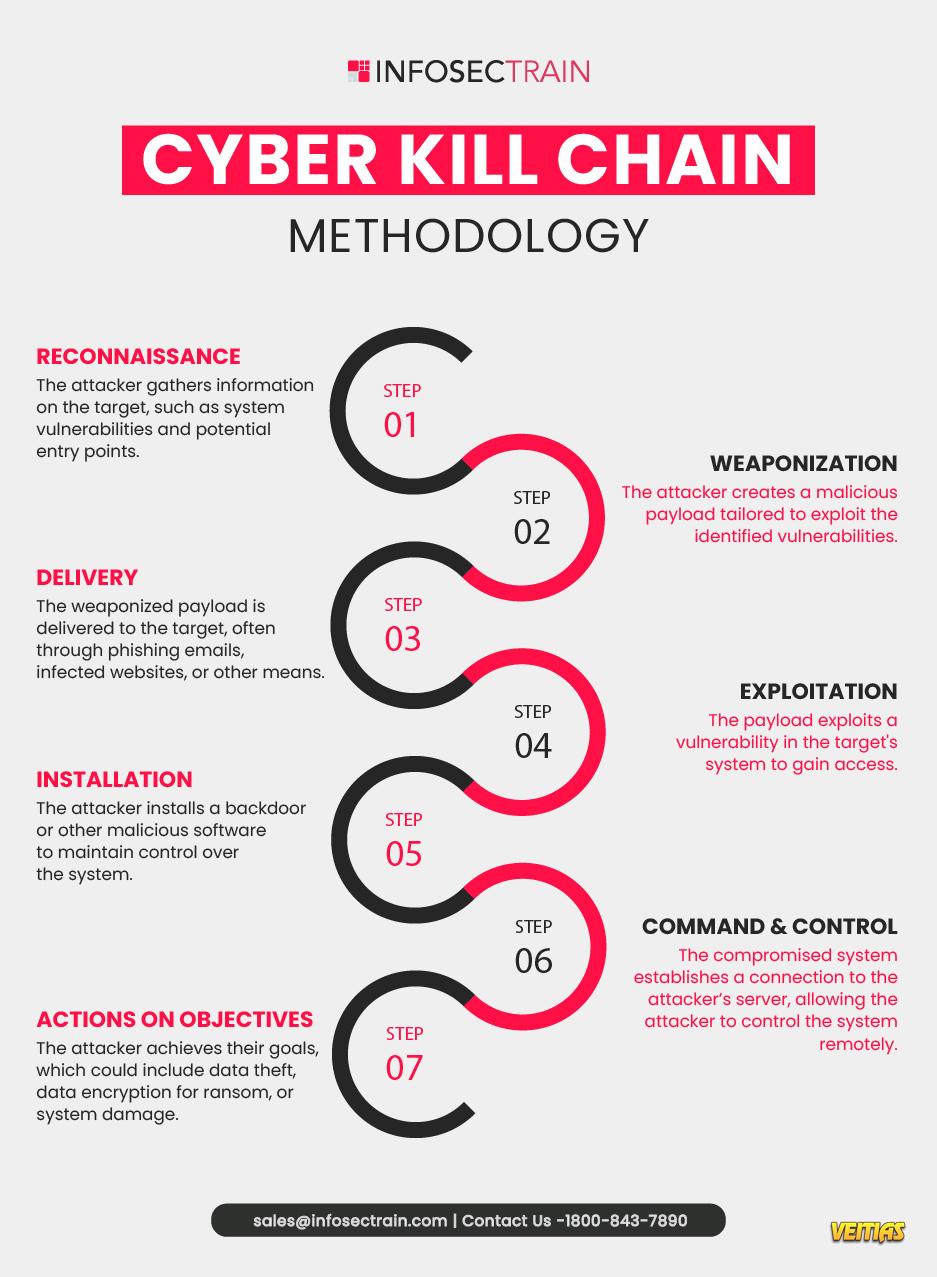
The Cyber Kill Chain: 7 Stages of a Cyber Attack Every Security Pro Should Know
Reconnaissance: Attackers gather intel about their target
Weaponization: Creating malicious payloads
Delivery: Transmitting the weapon to the target
Exploitation: Triggering the malicious code
Installation: Installing malware on the asset
Command & Control (C2): Establishing persistent access
Actions on Objectives: Achieving the attack goals
Understanding these phases helps organizations build stronger defenses at each step.
Watch Here: https://www.youtube.com/watch?v=VJ4yMQSt-DY
#CyberKillChain #KillChainPhases #CyberSecurity #ThreatLifecycle #NetworkSecurity #CyberThreats #SecurityAwareness #ThreatDetection #CyberDefense #InfosecTraining
Reconnaissance: Attackers gather intel about their target
Weaponization: Creating malicious payloads
Delivery: Transmitting the weapon to the target
Exploitation: Triggering the malicious code
Installation: Installing malware on the asset
Command & Control (C2): Establishing persistent access
Actions on Objectives: Achieving the attack goals
Understanding these phases helps organizations build stronger defenses at each step.
Watch Here: https://www.youtube.com/watch?v=VJ4yMQSt-DY
#CyberKillChain #KillChainPhases #CyberSecurity #ThreatLifecycle #NetworkSecurity #CyberThreats #SecurityAwareness #ThreatDetection #CyberDefense #InfosecTraining
The Cyber Kill Chain: 7 Stages of a Cyber Attack Every Security Pro Should Know
✅ Reconnaissance: Attackers gather intel about their target
✅ Weaponization: Creating malicious payloads
✅ Delivery: Transmitting the weapon to the target
✅ Exploitation: Triggering the malicious code
✅ Installation: Installing malware on the asset
✅ Command & Control (C2): Establishing persistent access
✅ Actions on Objectives: Achieving the attack goals
Understanding these phases helps organizations build stronger defenses at each step.
Watch Here: https://www.youtube.com/watch?v=VJ4yMQSt-DY
#CyberKillChain #KillChainPhases #CyberSecurity #ThreatLifecycle #NetworkSecurity #CyberThreats #SecurityAwareness #ThreatDetection #CyberDefense #InfosecTraining

0 Reacties
0 aandelen
2930 Views
0 voorbeeld