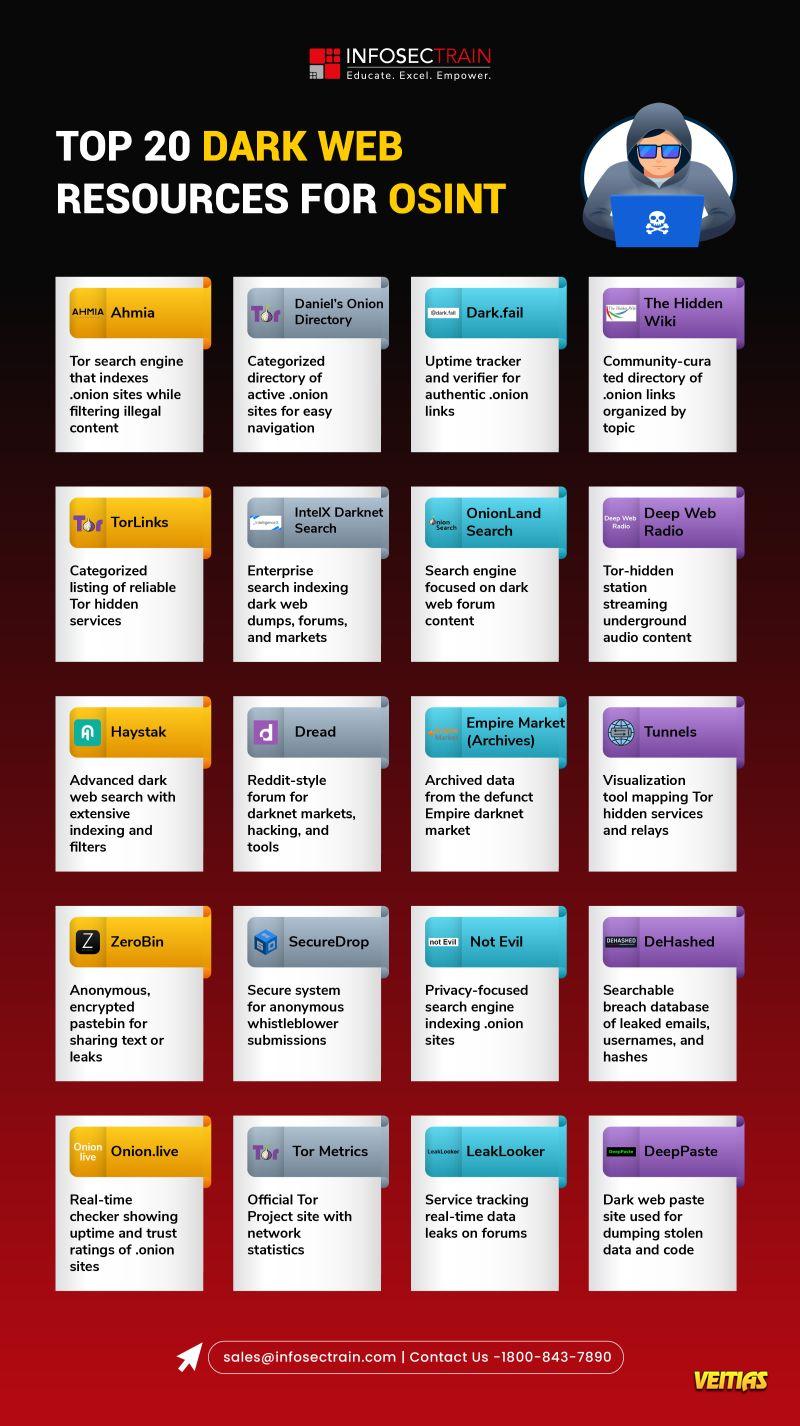
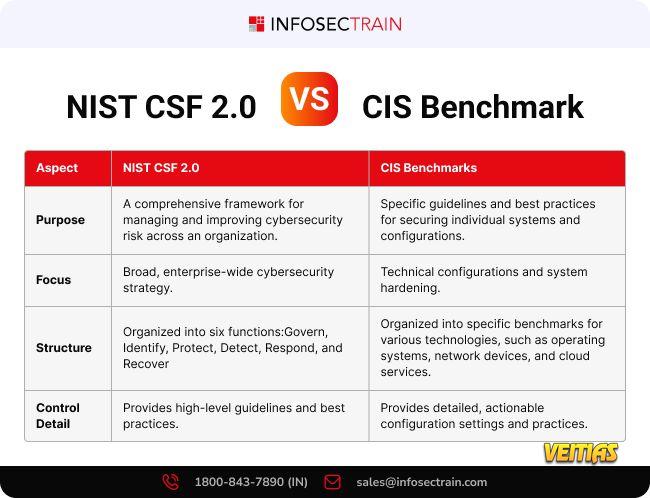
Automated Dispensing
Automated dispensing lockers Dispensation of garments, accessories and PPE, System easily scalable by incorporating modules, Fully customizable locker settings, Automated database Ethernet and Wifi connection, Wide catalog of readers of identification cards
Acerca de la compañía:-
La Fábrica de Software es una empresa de ingeniería especializada en el desarrollo de sistemas informáticos integrados con nuestros equipos y máquinas, para la gestión automatizada y control textil en hospitales, fábricas, lavanderías industriales, tintorerías, etc.
Contamos con personal cualificado dedicado a la investigación y desarrollo de soluciones innovadoras orientadas a atender las necesidades específicas de cada uno de nuestros clientes. Somos creadores del Lavander 4, un sistema informático diseñado para ofrecer, desde cualquier dispositivo, el control real e inmediato de albaranes, facturas, stocks, producción y rentabilidad de una planta, entre otras muchas funcionalidades.
Ofrecemos sistemas de última generación para el control de vestuario profesional, entre lo que destacamos nuestros dispensadores automáticos de ropa laboral, máquinas de retorno de unformidad y sistemas de taquillas inteligentes.
Haga clic aquí para más información.:-
https://lafabricadesoftware.es/en/taquillas/
Enlaces de perfil de redes sociales-
https://www.facebook.com/LaFabricaSoft/ https://twitter.com/LaFabricaSoft https://www.linkedin.com/company/la-fabrica-de-software-sl/?viewAsMember=trueAutomated Dispensing
Automated dispensing lockers Dispensation of garments, accessories and PPE, System easily scalable by incorporating modules, Fully customizable locker settings, Automated database Ethernet and Wifi connection, Wide catalog of readers of identification cards
Acerca de la compañía:-
La Fábrica de Software es una empresa de ingeniería especializada en el desarrollo de sistemas informáticos integrados con nuestros equipos y máquinas, para la gestión automatizada y control textil en hospitales, fábricas, lavanderías industriales, tintorerías, etc.
Contamos con personal cualificado dedicado a la investigación y desarrollo de soluciones innovadoras orientadas a atender las necesidades específicas de cada uno de nuestros clientes. Somos creadores del Lavander 4, un sistema informático diseñado para ofrecer, desde cualquier dispositivo, el control real e inmediato de albaranes, facturas, stocks, producción y rentabilidad de una planta, entre otras muchas funcionalidades.
Ofrecemos sistemas de última generación para el control de vestuario profesional, entre lo que destacamos nuestros dispensadores automáticos de ropa laboral, máquinas de retorno de unformidad y sistemas de taquillas inteligentes.
Haga clic aquí para más información.:- https://lafabricadesoftware.es/en/taquillas/
Enlaces de perfil de redes sociales-
https://www.facebook.com/LaFabricaSoft/
https://twitter.com/LaFabricaSoft
https://www.linkedin.com/company/la-fabrica-de-software-sl/?viewAsMember=true