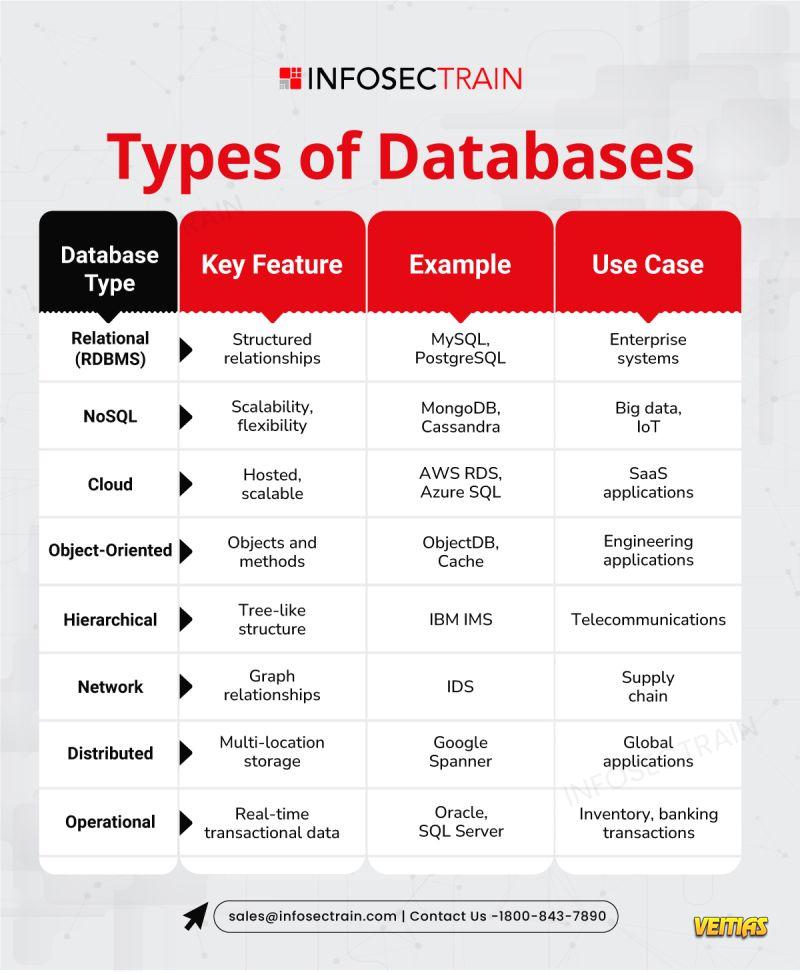
Databases are categorized into various types based on their structure, functionality, and use cases. Relational databases like MySQL, PostgreSQL, and Oracle organize data in structured tables with rows and columns, allowing easy querying using SQL. NoSQL databases, such as MongoDB, Cassandra, and Redis, are designed for unstructured or semi-structured data and are popular for handling large-scale, distributed data. Object-oriented databases store data as objects, aligning well with object-oriented programming languages. Graph databases, like Neo4j, excel at handling data with complex relationships, making them ideal for social networks and recommendation engines.
Databases are categorized into various types based on their structure, functionality, and use cases. Relational databases like MySQL, PostgreSQL, and Oracle organize data in structured tables with rows and columns, allowing easy querying using SQL. NoSQL databases, such as MongoDB, Cassandra, and Redis, are designed for unstructured or semi-structured data and are popular for handling large-scale, distributed data. Object-oriented databases store data as objects, aligning well with object-oriented programming languages. Graph databases, like Neo4j, excel at handling data with complex relationships, making them ideal for social networks and recommendation engines.