𝐖𝐡𝐚𝐭 𝐠𝐞𝐭𝐬 𝐦𝐞𝐚𝐬𝐮𝐫𝐞𝐝 𝐠𝐞𝐭𝐬 𝐦𝐚𝐧𝐚𝐠𝐞𝐝, 𝐞𝐬𝐩𝐞𝐜𝐢𝐚𝐥𝐥𝐲 𝐚𝐭 𝐭𝐡𝐞 𝐂𝐈𝐒𝐎 𝐥𝐞𝐯𝐞𝐥.
Modern security leadership isn’t about counting alerts.
It’s about 𝐭𝐞𝐥𝐥𝐢𝐧𝐠 𝐚 𝐜𝐥𝐞𝐚𝐫, 𝐛𝐮𝐬𝐢𝐧𝐞𝐬𝐬-𝐟𝐨𝐜𝐮𝐬𝐞𝐝 𝐫𝐢𝐬𝐤 𝐬𝐭𝐨𝐫𝐲 𝐭𝐨 𝐭𝐡𝐞 𝐛𝐨𝐚𝐫𝐝.
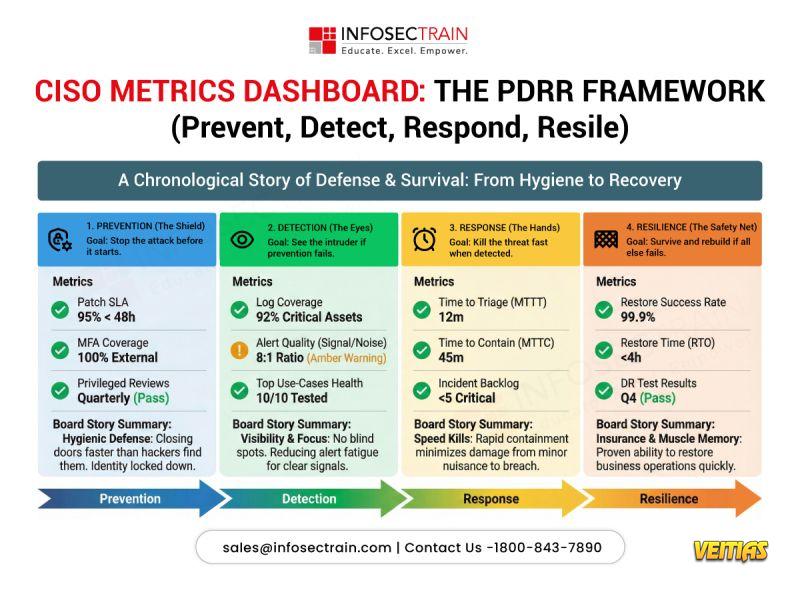
The PDRR framework (𝐏𝐫𝐞𝐯𝐞𝐧𝐭, 𝐃𝐞𝐭𝐞𝐜𝐭, 𝐑𝐞𝐬𝐩𝐨𝐧𝐝, 𝐑𝐞𝐬𝐢𝐥𝐞) helps CISOs align metrics across the entire security lifecycle:
• 𝐏𝐫𝐞𝐯𝐞𝐧𝐭 – Reduce attack opportunities
• 𝐃𝐞𝐭𝐞𝐜𝐭 – Gain early, high-fidelity visibility
• 𝐑𝐞𝐬𝐩𝐨𝐧𝐝 – Contain threats quickly
• 𝐑𝐞𝐬𝐢𝐥𝐞 – Recover and sustain business operations
When metrics follow this structure, 𝐜𝐨𝐧𝐯𝐞𝐫𝐬𝐚𝐭𝐢𝐨𝐧𝐬 𝐬𝐡𝐢𝐟𝐭 𝐟𝐫𝐨𝐦 𝐭𝐨𝐨𝐥𝐬 𝐭𝐨 𝐫𝐢𝐬𝐤, 𝐫𝐞𝐬𝐢𝐥𝐢𝐞𝐧𝐜𝐞, 𝐚𝐧𝐝 𝐨𝐮𝐭𝐜𝐨𝐦𝐞𝐬.
Modern security leadership isn’t about counting alerts.
It’s about 𝐭𝐞𝐥𝐥𝐢𝐧𝐠 𝐚 𝐜𝐥𝐞𝐚𝐫, 𝐛𝐮𝐬𝐢𝐧𝐞𝐬𝐬-𝐟𝐨𝐜𝐮𝐬𝐞𝐝 𝐫𝐢𝐬𝐤 𝐬𝐭𝐨𝐫𝐲 𝐭𝐨 𝐭𝐡𝐞 𝐛𝐨𝐚𝐫𝐝.
The PDRR framework (𝐏𝐫𝐞𝐯𝐞𝐧𝐭, 𝐃𝐞𝐭𝐞𝐜𝐭, 𝐑𝐞𝐬𝐩𝐨𝐧𝐝, 𝐑𝐞𝐬𝐢𝐥𝐞) helps CISOs align metrics across the entire security lifecycle:
• 𝐏𝐫𝐞𝐯𝐞𝐧𝐭 – Reduce attack opportunities
• 𝐃𝐞𝐭𝐞𝐜𝐭 – Gain early, high-fidelity visibility
• 𝐑𝐞𝐬𝐩𝐨𝐧𝐝 – Contain threats quickly
• 𝐑𝐞𝐬𝐢𝐥𝐞 – Recover and sustain business operations
When metrics follow this structure, 𝐜𝐨𝐧𝐯𝐞𝐫𝐬𝐚𝐭𝐢𝐨𝐧𝐬 𝐬𝐡𝐢𝐟𝐭 𝐟𝐫𝐨𝐦 𝐭𝐨𝐨𝐥𝐬 𝐭𝐨 𝐫𝐢𝐬𝐤, 𝐫𝐞𝐬𝐢𝐥𝐢𝐞𝐧𝐜𝐞, 𝐚𝐧𝐝 𝐨𝐮𝐭𝐜𝐨𝐦𝐞𝐬.
𝐖𝐡𝐚𝐭 𝐠𝐞𝐭𝐬 𝐦𝐞𝐚𝐬𝐮𝐫𝐞𝐝 𝐠𝐞𝐭𝐬 𝐦𝐚𝐧𝐚𝐠𝐞𝐝, 𝐞𝐬𝐩𝐞𝐜𝐢𝐚𝐥𝐥𝐲 𝐚𝐭 𝐭𝐡𝐞 𝐂𝐈𝐒𝐎 𝐥𝐞𝐯𝐞𝐥.
Modern security leadership isn’t about counting alerts.
It’s about 𝐭𝐞𝐥𝐥𝐢𝐧𝐠 𝐚 𝐜𝐥𝐞𝐚𝐫, 𝐛𝐮𝐬𝐢𝐧𝐞𝐬𝐬-𝐟𝐨𝐜𝐮𝐬𝐞𝐝 𝐫𝐢𝐬𝐤 𝐬𝐭𝐨𝐫𝐲 𝐭𝐨 𝐭𝐡𝐞 𝐛𝐨𝐚𝐫𝐝.
The PDRR framework (𝐏𝐫𝐞𝐯𝐞𝐧𝐭, 𝐃𝐞𝐭𝐞𝐜𝐭, 𝐑𝐞𝐬𝐩𝐨𝐧𝐝, 𝐑𝐞𝐬𝐢𝐥𝐞) helps CISOs align metrics across the entire security lifecycle:
• 𝐏𝐫𝐞𝐯𝐞𝐧𝐭 – Reduce attack opportunities
• 𝐃𝐞𝐭𝐞𝐜𝐭 – Gain early, high-fidelity visibility
• 𝐑𝐞𝐬𝐩𝐨𝐧𝐝 – Contain threats quickly
• 𝐑𝐞𝐬𝐢𝐥𝐞 – Recover and sustain business operations
When metrics follow this structure, 𝐜𝐨𝐧𝐯𝐞𝐫𝐬𝐚𝐭𝐢𝐨𝐧𝐬 𝐬𝐡𝐢𝐟𝐭 𝐟𝐫𝐨𝐦 𝐭𝐨𝐨𝐥𝐬 𝐭𝐨 𝐫𝐢𝐬𝐤, 𝐫𝐞𝐬𝐢𝐥𝐢𝐞𝐧𝐜𝐞, 𝐚𝐧𝐝 𝐨𝐮𝐭𝐜𝐨𝐦𝐞𝐬.
0 Comments
0 Shares
274 Views
0 Reviews