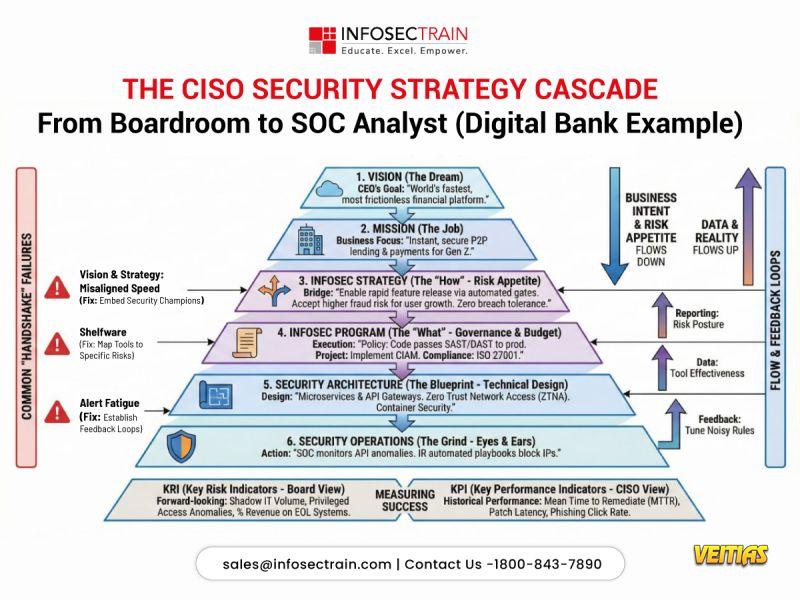
Why do security strategies fail between the boardroom and the SOC?
Because vision doesn’t always translate into execution.
A strong CISO strategy must cascade clearly:
* From business vision to defined risk appetite
* From governance to security architecture
* From architecture to SOC actions
* From alerts to measurable business outcomes
When this alignment breaks, organizations experience misaligned priorities, shelfware tools, and alert fatigue. Modern security leadership is about connecting intent, risk, technology, and operations into a single, continuous feedback loop.
If you’re stepping into, or already in, a CISO role, mastering this translation from strategy to execution is non-negotiable.
Build real CISO-level strategy and execution skills.
Because vision doesn’t always translate into execution.
A strong CISO strategy must cascade clearly:
* From business vision to defined risk appetite
* From governance to security architecture
* From architecture to SOC actions
* From alerts to measurable business outcomes
When this alignment breaks, organizations experience misaligned priorities, shelfware tools, and alert fatigue. Modern security leadership is about connecting intent, risk, technology, and operations into a single, continuous feedback loop.
If you’re stepping into, or already in, a CISO role, mastering this translation from strategy to execution is non-negotiable.
Build real CISO-level strategy and execution skills.
Why do security strategies fail between the boardroom and the SOC?
Because vision doesn’t always translate into execution.
A strong CISO strategy must cascade clearly:
* From business vision to defined risk appetite
* From governance to security architecture
* From architecture to SOC actions
* From alerts to measurable business outcomes
When this alignment breaks, organizations experience misaligned priorities, shelfware tools, and alert fatigue. Modern security leadership is about connecting intent, risk, technology, and operations into a single, continuous feedback loop.
If you’re stepping into, or already in, a CISO role, mastering this translation from strategy to execution is non-negotiable.
Build real CISO-level strategy and execution skills.
0 Commentarios
0 Acciones
2840 Views
0 Vista previa