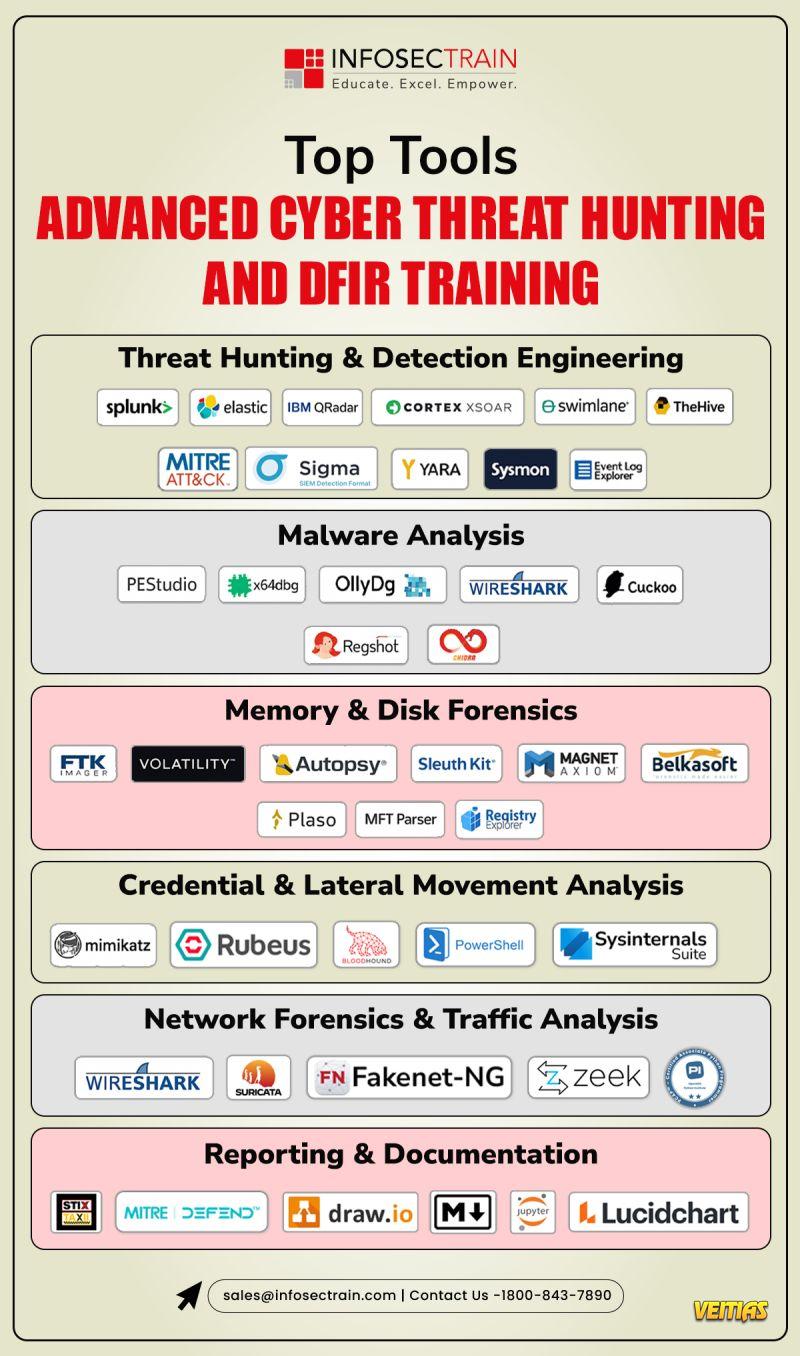
𝐒𝐈𝐄𝐌 𝐯𝐬 𝐒𝐈𝐌 𝐯𝐬 𝐒𝐄𝐌: 𝐖𝐡𝐚𝐭’𝐬 𝐭𝐡𝐞 𝐃𝐢𝐟𝐟𝐞𝐫𝐞𝐧𝐜𝐞?
Ever wondered what makes 𝐒𝐈𝐄𝐌, 𝐒𝐈𝐌, 𝐚𝐧𝐝 𝐒𝐄𝐌 different and why cybersecurity teams keep talking about them?
SIMThe data keeper: collects & stores logs
SEM The watchdog: detects threats in real time
SIEMThe brain: combines both for total defense
𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐝𝐞𝐭𝐚𝐢𝐥𝐞𝐝 𝐛𝐫𝐞𝐚𝐤𝐝𝐨𝐰𝐧 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/siem-vs-sim-vs-sem/
In today’s world of complex cyber threats, SIEM stands at the heart of modern SOC operations, empowering teams to detect, respond, and stay compliant all from a single platform.
At Infosec Train, we help aspiring SOC Analysts get hands-on with tools like Splunk and Wireshark to master SIEM in real-world environments.
#CyberSecurity #SIEM #SOCAnalyst #InfoSecTrain #ThreatDetection #DataProtection #SecurityOperations
Ever wondered what makes 𝐒𝐈𝐄𝐌, 𝐒𝐈𝐌, 𝐚𝐧𝐝 𝐒𝐄𝐌 different and why cybersecurity teams keep talking about them?
SIMThe data keeper: collects & stores logs
SEM The watchdog: detects threats in real time
SIEMThe brain: combines both for total defense
𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐝𝐞𝐭𝐚𝐢𝐥𝐞𝐝 𝐛𝐫𝐞𝐚𝐤𝐝𝐨𝐰𝐧 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/siem-vs-sim-vs-sem/
In today’s world of complex cyber threats, SIEM stands at the heart of modern SOC operations, empowering teams to detect, respond, and stay compliant all from a single platform.
At Infosec Train, we help aspiring SOC Analysts get hands-on with tools like Splunk and Wireshark to master SIEM in real-world environments.
#CyberSecurity #SIEM #SOCAnalyst #InfoSecTrain #ThreatDetection #DataProtection #SecurityOperations
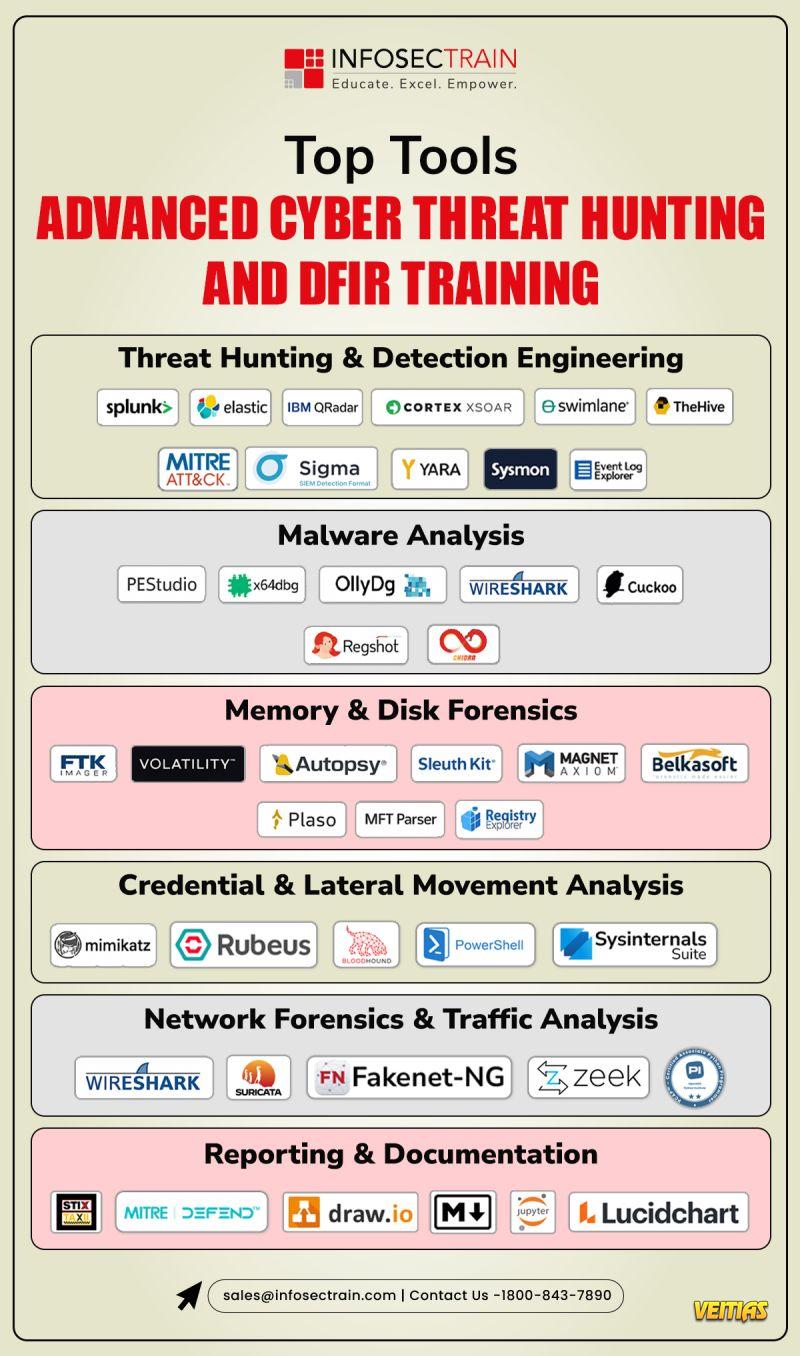
𝐒𝐈𝐄𝐌 𝐯𝐬 𝐒𝐈𝐌 𝐯𝐬 𝐒𝐄𝐌: 𝐖𝐡𝐚𝐭’𝐬 𝐭𝐡𝐞 𝐃𝐢𝐟𝐟𝐞𝐫𝐞𝐧𝐜𝐞?
Ever wondered what makes 𝐒𝐈𝐄𝐌, 𝐒𝐈𝐌, 𝐚𝐧𝐝 𝐒𝐄𝐌 different and why cybersecurity teams keep talking about them?
🔹SIM👉The data keeper: collects & stores logs
🔹SEM👉 The watchdog: detects threats in real time
🔹SIEM👉The brain: combines both for total defense
🔗 𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐝𝐞𝐭𝐚𝐢𝐥𝐞𝐝 𝐛𝐫𝐞𝐚𝐤𝐝𝐨𝐰𝐧 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/siem-vs-sim-vs-sem/
In today’s world of complex cyber threats, SIEM stands at the heart of modern SOC operations, empowering teams to detect, respond, and stay compliant all from a single platform.
At Infosec Train, we help aspiring SOC Analysts get hands-on with tools like Splunk and Wireshark to master SIEM in real-world environments.
#CyberSecurity #SIEM #SOCAnalyst #InfoSecTrain #ThreatDetection #DataProtection #SecurityOperations
0 Comments
0 Shares
2483 Views
0 Reviews