Keep Your Inbox Safe: Master Email Security Protocols!
Did you know that email is one of the most targeted attack vectors for hackers? From phishing scams to data breaches, unsecured emails can expose sensitive business and personal information.
That’s why Email Security Protocols are your first line of defense.
Key Protocols You Should Know:
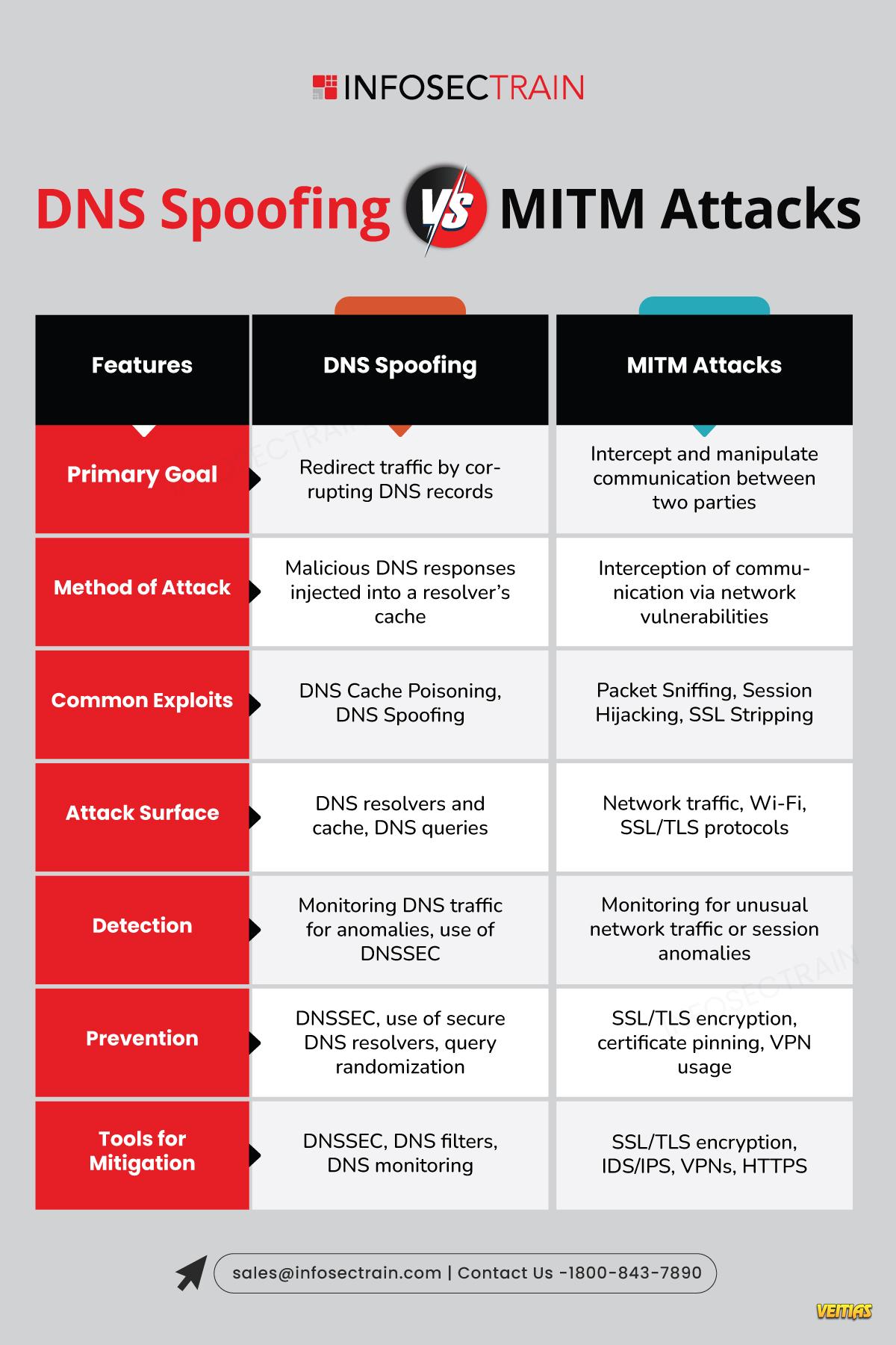
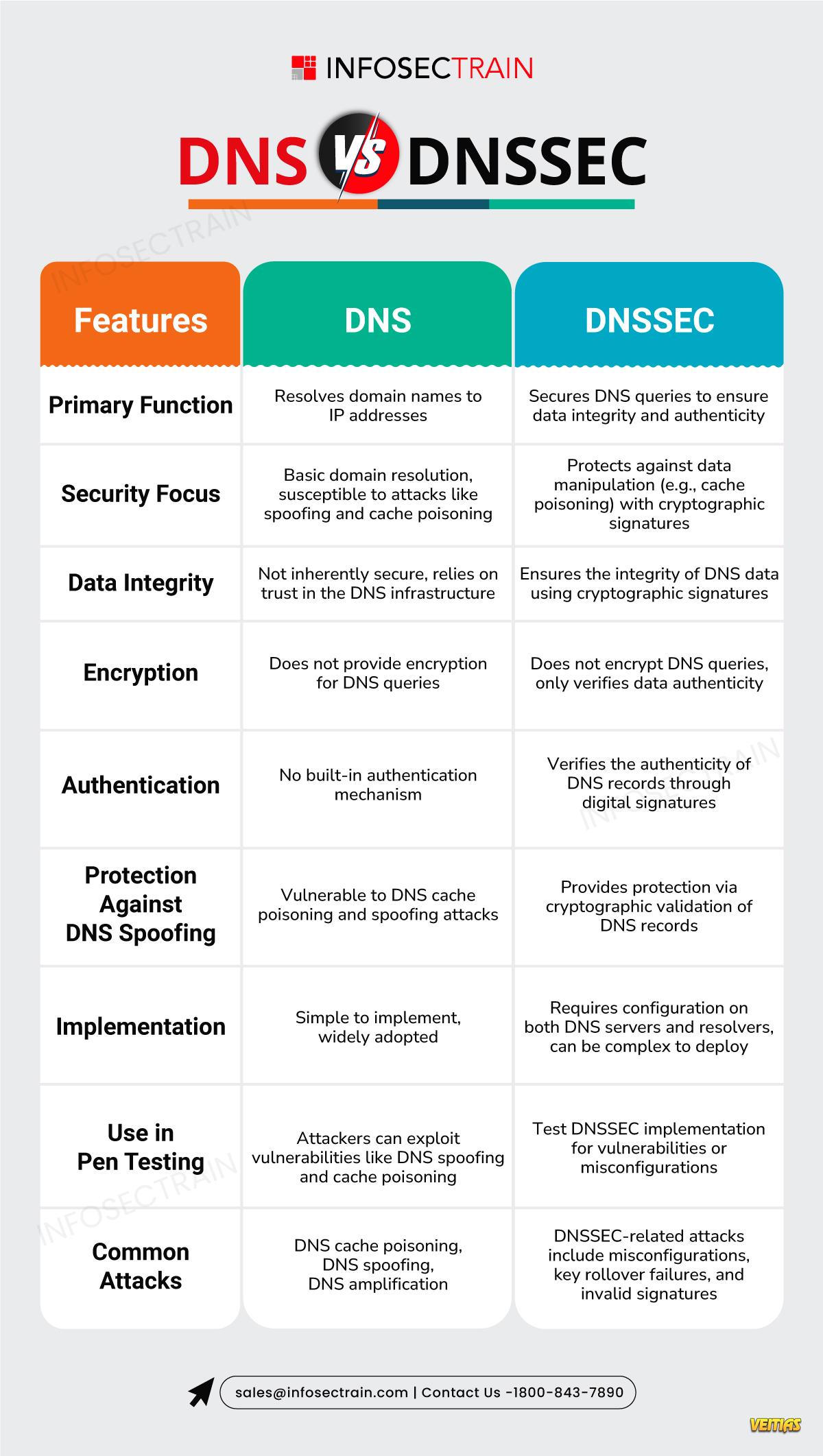
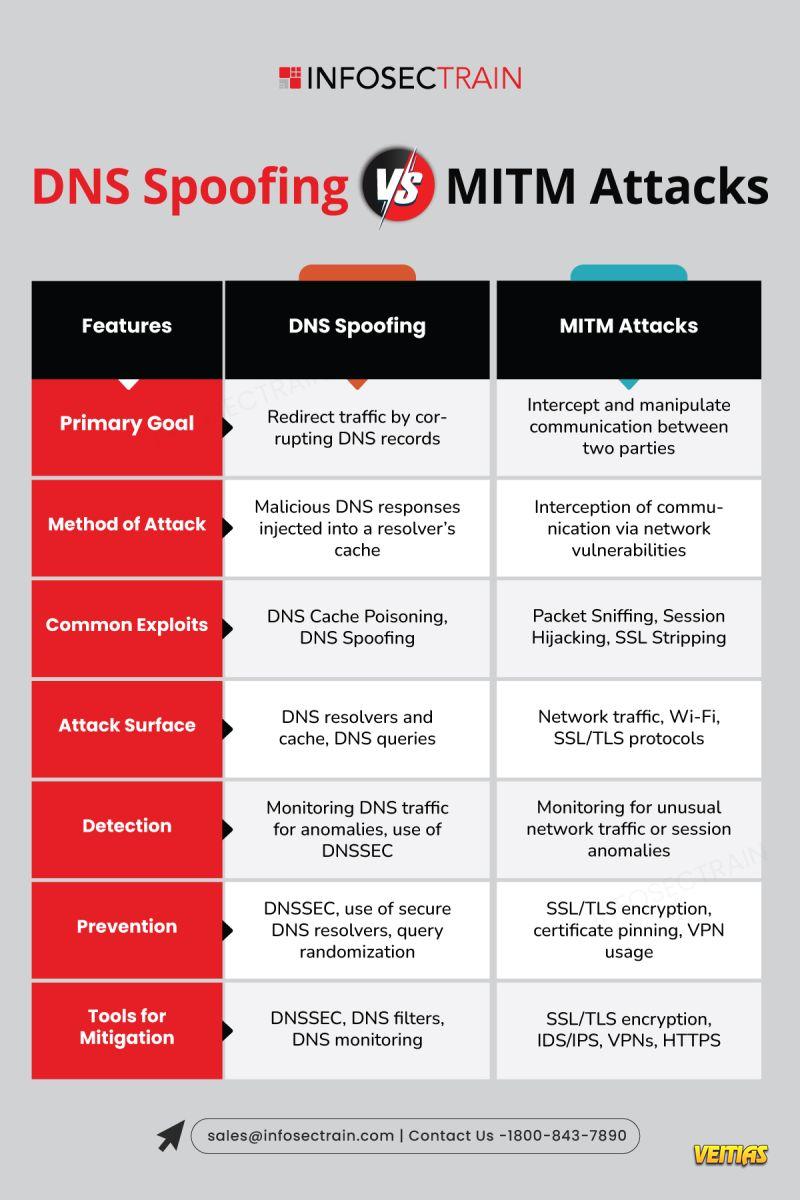
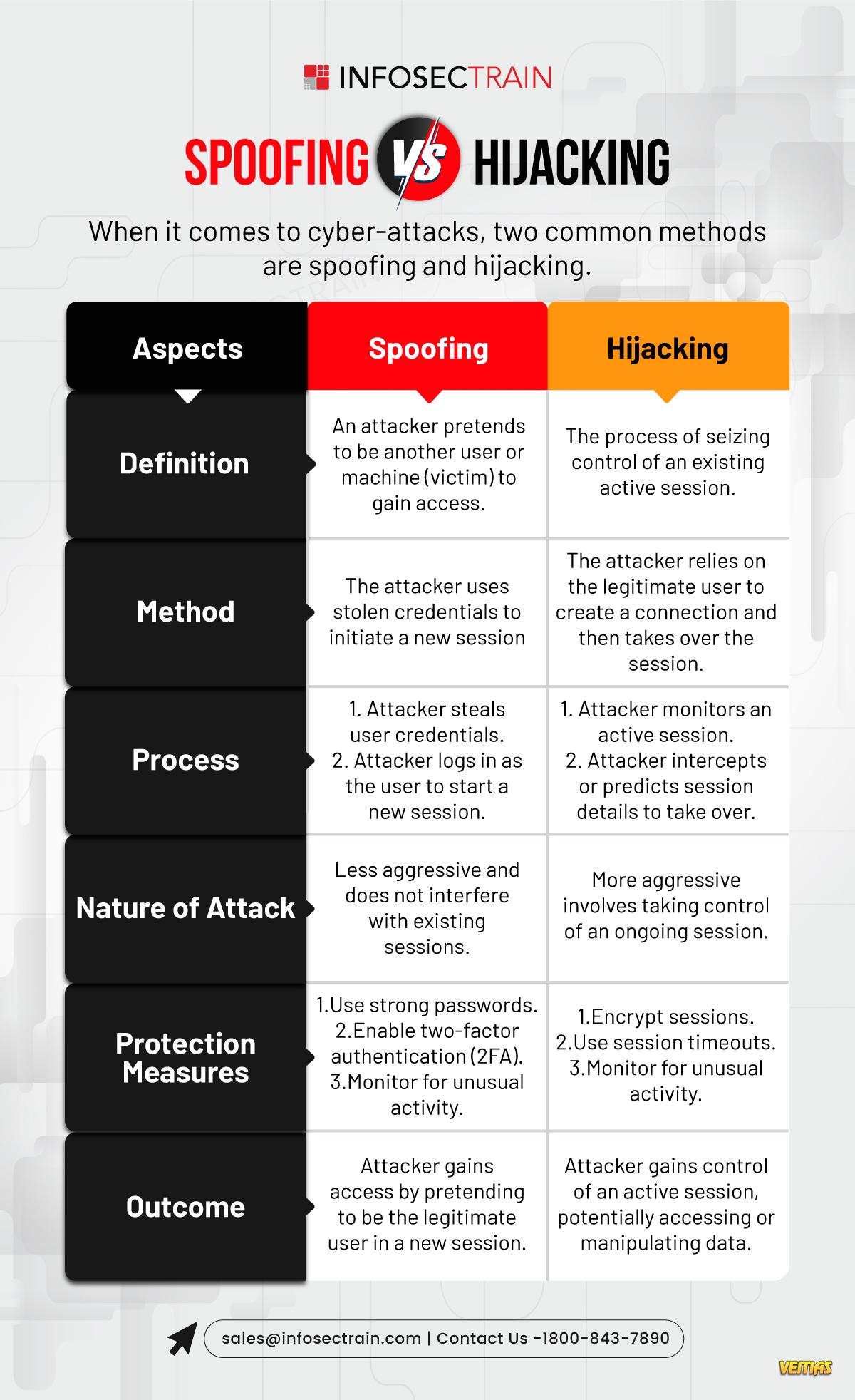
Authentication Protocols – SPF, DKIM, DMARC (Stop spoofing & ensure authenticity)
Transmission Security Protocols – TLS, STARTTLS (Encrypt emails in transit)
End-to-End Encryption Protocols – S/MIME, PGP (Protect content with encryption & signatures)
Together, these protocols shield your emails from interception, forgery, and unauthorized access.
Learn more about strengthening your email security: www.infosectrain.com
#CyberSecurityAwareness #EmailSecurity #PhishingProtection #InfoSec #CyberDefense #SecureEmail #DataProtection #OnlineSafety #CyberHygiene #SPF #DKIM #DMARC #Encryption #InfoSecTrain
Did you know that email is one of the most targeted attack vectors for hackers? From phishing scams to data breaches, unsecured emails can expose sensitive business and personal information.
That’s why Email Security Protocols are your first line of defense.
Key Protocols You Should Know:
Authentication Protocols – SPF, DKIM, DMARC (Stop spoofing & ensure authenticity)
Transmission Security Protocols – TLS, STARTTLS (Encrypt emails in transit)
End-to-End Encryption Protocols – S/MIME, PGP (Protect content with encryption & signatures)
Together, these protocols shield your emails from interception, forgery, and unauthorized access.
Learn more about strengthening your email security: www.infosectrain.com
#CyberSecurityAwareness #EmailSecurity #PhishingProtection #InfoSec #CyberDefense #SecureEmail #DataProtection #OnlineSafety #CyberHygiene #SPF #DKIM #DMARC #Encryption #InfoSecTrain
📧🔐 Keep Your Inbox Safe: Master Email Security Protocols!
Did you know that email is one of the most targeted attack vectors for hackers? From phishing scams to data breaches, unsecured emails can expose sensitive business and personal information.
That’s why Email Security Protocols are your first line of defense.
✨ Key Protocols You Should Know:
✅ Authentication Protocols – SPF, DKIM, DMARC (Stop spoofing & ensure authenticity)
✅ Transmission Security Protocols – TLS, STARTTLS (Encrypt emails in transit)
✅ End-to-End Encryption Protocols – S/MIME, PGP (Protect content with encryption & signatures)
💡 Together, these protocols shield your emails from interception, forgery, and unauthorized access.
🔗 Learn more about strengthening your email security: www.infosectrain.com
#CyberSecurityAwareness #EmailSecurity #PhishingProtection #InfoSec #CyberDefense #SecureEmail #DataProtection #OnlineSafety #CyberHygiene #SPF #DKIM #DMARC #Encryption #InfoSecTrain
0 Комментарии
0 Поделились
4209 Просмотры
0 предпросмотр