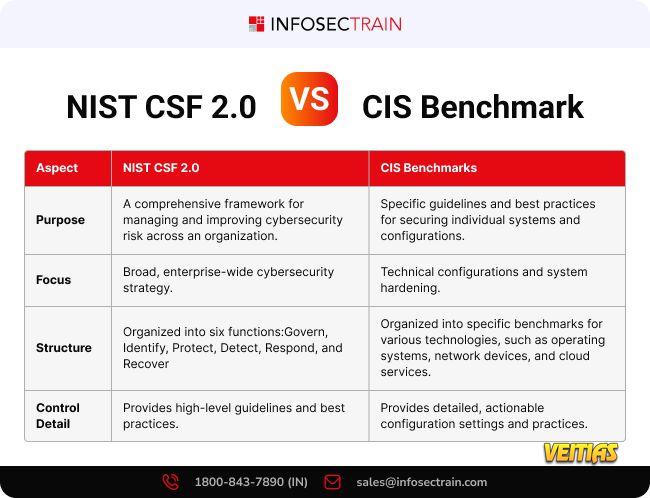
𝐒𝐲𝐬𝐭𝐞𝐦 𝐇𝐚𝐫𝐝𝐞𝐧𝐢𝐧𝐠: 𝐘𝐨𝐮𝐫 𝐅𝐢𝐫𝐬𝐭 𝐋𝐢𝐧𝐞 𝐨𝐟 𝐃𝐞𝐟𝐞𝐧𝐬𝐞!
System hardening serves as a fundamental security measure which organizations use to stop cyber threats from breaching their systems.
The concept appears in 𝐈𝐒𝐂𝟐 𝐂𝐞𝐫𝐭𝐢𝐟𝐢𝐞𝐝 𝐢𝐧 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 (𝐂𝐂) – 𝐃𝐨𝐦𝐚𝐢𝐧 𝟓.𝟐: The concept operates through these fundamental components:
Configuration management, secure baseline, and
Version control, and patch management
The process of reducing configuration vulnerabilities requires the application of security measures.
The process of establishing strong account security measures serves as a defense system which protects user accounts from unauthorized access.
The correct implementation of hardening techniques provides protection to your IT infrastructure by creating a stable and secure environment. This also passes audits against complex cyber threats.
𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐝𝐞𝐭𝐚𝐢𝐥𝐞𝐝 𝐛𝐥𝐨𝐠 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/isc2-cc-domain-5-5-2-understand-system-hardening/
#Cybersecurity #SystemHardening #ConfigurationManagement #PatchManagement #ISC2CC #InfosecTrain #CyberSec #InfoSec #SecurityAwareness
System hardening serves as a fundamental security measure which organizations use to stop cyber threats from breaching their systems.
The concept appears in 𝐈𝐒𝐂𝟐 𝐂𝐞𝐫𝐭𝐢𝐟𝐢𝐞𝐝 𝐢𝐧 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 (𝐂𝐂) – 𝐃𝐨𝐦𝐚𝐢𝐧 𝟓.𝟐: The concept operates through these fundamental components:
Configuration management, secure baseline, and
Version control, and patch management
The process of reducing configuration vulnerabilities requires the application of security measures.
The process of establishing strong account security measures serves as a defense system which protects user accounts from unauthorized access.
The correct implementation of hardening techniques provides protection to your IT infrastructure by creating a stable and secure environment. This also passes audits against complex cyber threats.
𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐝𝐞𝐭𝐚𝐢𝐥𝐞𝐝 𝐛𝐥𝐨𝐠 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/isc2-cc-domain-5-5-2-understand-system-hardening/
#Cybersecurity #SystemHardening #ConfigurationManagement #PatchManagement #ISC2CC #InfosecTrain #CyberSec #InfoSec #SecurityAwareness
𝐒𝐲𝐬𝐭𝐞𝐦 𝐇𝐚𝐫𝐝𝐞𝐧𝐢𝐧𝐠: 𝐘𝐨𝐮𝐫 𝐅𝐢𝐫𝐬𝐭 𝐋𝐢𝐧𝐞 𝐨𝐟 𝐃𝐞𝐟𝐞𝐧𝐬𝐞!
System hardening serves as a fundamental security measure which organizations use to stop cyber threats from breaching their systems.
The concept appears in 𝐈𝐒𝐂𝟐 𝐂𝐞𝐫𝐭𝐢𝐟𝐢𝐞𝐝 𝐢𝐧 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 (𝐂𝐂) – 𝐃𝐨𝐦𝐚𝐢𝐧 𝟓.𝟐: The concept operates through these fundamental components:
🔸 Configuration management, secure baseline, and
🔸 Version control, and patch management
✅The process of reducing configuration vulnerabilities requires the application of security measures.
✅The process of establishing strong account security measures serves as a defense system which protects user accounts from unauthorized access.
✅ The correct implementation of hardening techniques provides protection to your IT infrastructure by creating a stable and secure environment. This also passes audits against complex cyber threats.
👉 𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐝𝐞𝐭𝐚𝐢𝐥𝐞𝐝 𝐛𝐥𝐨𝐠 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/isc2-cc-domain-5-5-2-understand-system-hardening/
#Cybersecurity #SystemHardening #ConfigurationManagement #PatchManagement #ISC2CC #InfosecTrain #CyberSec #InfoSec #SecurityAwareness
0 Commenti
0 condivisioni
4931 Views
0 Anteprima